Trusted by




& many more
Trusted by



& many more
See What Our Customers Have to Say
This software helps us to achieve compliance with industry and government requirements with respect to controlling the use of removable storage media. It fits the bill perfectly.
Matthew W, Project Manager
Aviation & Aerospace Industry, 11-50 employees
In my nearly 40 years in the IT business I’ve worked with a lot of support teams. I really appreciate CurrentWare going the extra mile to help me get the most out of the product. They’ve definitely outweighed any of the other competitors that I’ve looked at.
J.S, Managed Services Provider
Vehicle Dealership, 150-200 Employees
The reports are very easy to understand and the fact that they can be emailed to you on a schedule is amazing... Customer support has been fantastic every time I've had to reach out to them; I highly recommend them!
Kristen S, Associate IT Director
The Coding Network, 700+ Employees
We have experienced data leaks by dishonest employees in the past and AccessPatrol has helped us avoid them and work with greater security and peace of mind for us and our customers.
Julio V, Head of Information Technology
Financial Services Industry, 10,001+ employees
Expand your capabilities with CurrentWare's award-winning productivity and security software
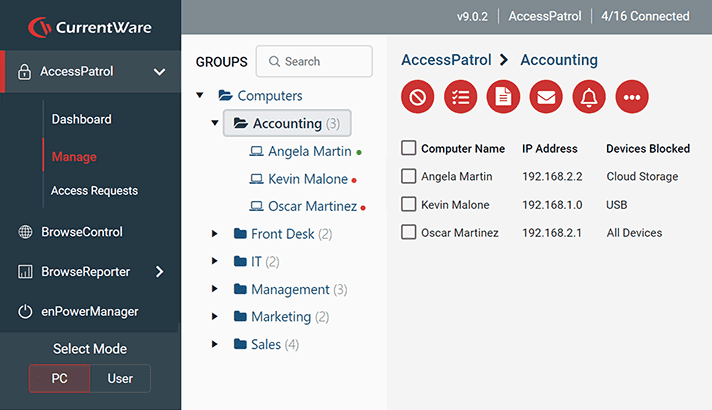
AccessPatrol’s USB Control & Data Loss Prevention Features
Block USB & Other Devices
Set full access, read only or no access on storage devices
Whitelist USB Devices
Allow only authorized storage devices to be used
Block File Transfers
Prevent files from being transferred to portable storage
Access Code Generator
Provide temporary access to peripheral devices
DLP Activity Reports
Track file transfers, storage device use, file operations, and more
File Transfer Monitoring
Monitor files that are copied to USBs, cloud storage, and more
Alerts & Reports
Automatically send USB activity reports to designated inboxes
Transparent & Stealth Modes
Run silently in the background or provide notice of monitoring
Central Web Console
Save time with a central admin console; optionally integrate Active
Directory OUs or security groups
Platform Security
Protect your CurrentWare console
with 2FA, passwords, privilege
management, and more
Offsite Management
Extend onsite security policies to computers running outside the corporate network
SQL Server Supported
Database scaled for enterprise and
large business operations using
Microsoft SQL Server