Are Cell Phones Risking Your Cybersecurity?

It’s Friday afternoon and in just a few short hours your employees will be making their way out of the office, eagerly venturing off to the exciting weekend ahead of them.
Knowing they have a long commute after leaving, one of your employees decides to charge their cell phone with an office computer’s USB port. Entirely unknown to them, they have just compromised sensitive customer data with a harmful virus that is rapidly spreading across your internal network.
As a business owner, it is your responsibility to ensure that sensitive customer data is protected. In our ever-evolving technological landscape, hackers are becoming increasingly clever in discovering new methods of acquiring the emails, addresses, and financial details of your customers.
As your organization continues to grow, the potential to cause serious data breaches increases greatly. How can you stay on top of things so that you can focus on what you do best? The answer is implementing an endpoint security plan.
What is Endpoint Security?
In networking, an “Endpoint” refers to the physical devices connected to your network. This not only includes common devices such as desktops, laptops, and smartphones, but also retail kiosks and POS terminals.
Organizations with corporate data held on endpoint devices can unknowingly cause a serious cybersecurity concern should the data fall into the wrong hands.
Endpoint Security is the practice of ensuring that these ‘endpoints’ are safe from data breaches by preventing the installation of malicious software and the transfer of data to unauthorized devices – this is often accomplished with Endpoint Security Software.
What is Endpoint Security Software?
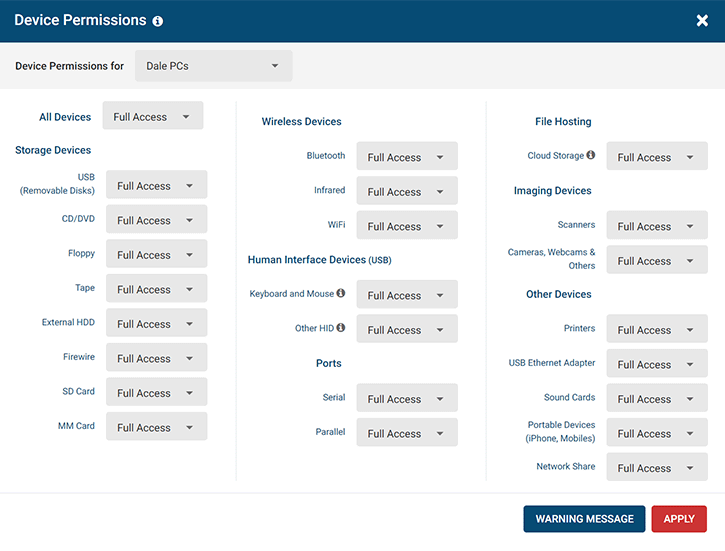
Endpoint Security Software, such as CurrentWare’s AccessPatrol, prevents malware attacks and data breaches by proactively disabling the ability to transfer data and malware from unauthorized devices, increasing network security for businesses of all sizes.
A robust Endpoint Security Software gives you the tools you need to implement a suitable data loss prevention strategy with access to features such as the ability to selectively modify device permissions, block external devices, and protect your valuable data by controlling who has access to it, how it is handled, and where it is stored.
How Can I Get Started?
If you are ready to start taking your company’s data security seriously, our expert team is here to help. Download our full-feature free trial and we can guide you every step of the way.
Companies around the world are falling victim to data breaches and malware attacks because they are not implementing endpoint security software to protect their computers.
AccessPatrol is a proactive solution for securing company endpoints to prevent the illicit transfer of data and download of malware from unauthorized devices, resulting in an increase of network and data security for businesses of all sizes.



