What You Must Know Before Using an Employee Activity Tracker
Want to track employee computer activity? There are some critical things that you need to know before you get started. This article will help business owners analyze the pros and cons of employee monitoring and provide managers with the best practices that they should follow when they use a monitoring app to track their team’s productivity.
Software to Track Activity on Employee Computers
Ready to improve productivity and endpoint security? With CurrentWare’s computer tracking software, tracking the computer activity of your users is as easy as installing the solution on their computers and remotely running reports from a convenient central console.
- Track web browsing including time spent on each site, the exact URL, the web page title, and more
- Monitor app usage to see who is playing games or using unauthorized software
- Get automatic screenshots of user desktops when they use certain apps and websites
- Track idle time to see how active each user is on their computers
- Check bandwidth usage to see who is slowing down the network with Netflix, Twitch, and Sports streaming
- Pros and Cons of Employee Monitoring
- Why Do Employers Monitor Employee Computer Activity?
- How to Monitor Employee Computer Activity
- How to Track Employee Internet Activity
- How Monitor What Web Browsers Are Used
- How to Monitor App Use
- How to Monitor Computer Activity Remotely
- How to Monitor User Logons
- How to Monitor USB Activity
- How Much Employee Monitoring Is Too Much?
Pros and Cons of Employee Monitoring Software

If you’re reading this article, chances are that you plan to start monitoring your employees with computer tracking software—if you aren’t already.
Understanding the potential concerns of your employees is critical for increasing employee buy-in for employee monitoring software. Before you deploy employee monitoring software in your business, let’s evaluate the pros and cons of monitoring employees.
Employee Monitoring: Pros
- Collect valuable user activity data to improve business intelligence
- Reduce your employee’s temptations to browse unproductive websites
- Discover which departments or employees are overworked or underworked
- Make acceptable use policies easier to enforce
- Reduce software expenses by tracking utilization rates
- Improve visibility into the working habits of in-office and remote employees
- Detect the use of unauthorized or pirated software
- Time tracking features keep track of time spent on computers during work hours
Employee Monitoring: Cons
- Employees may feel that their employers are monitoring them because they do not trust them to act professionally.
- Employees may be concerned that their work habits will be micromanaged and that any small deviance will be held against them, removing their sense of autonomy.
- Sensitive personal information about the employee may be captured, especially if employees use work devices for personal tasks.
- Employee monitoring may be regulated by data privacy and workplace surveillance laws.
As you can see, monitoring employees in the workplace with computer tracking software is not inherently risk-free.
In order for managers to get the full benefits of computer tracking software companies need to have a clear understanding of the laws that affect their business. Companies must also be prepared to address potential objections that your employees may have. I will touch more on what you can do to mitigate these concerns later in this article.
Want to create a successful employee monitoring strategy? Check out the Ultimate Guide to Employee Monitoring, an in-depth guide with tips for increasing employee buy-in, choosing the best employee monitoring software for your business, and legal considerations you need to know when monitoring employees.
Why Do Companies Use User Tracking Tools?
Note: The above video showcases a legacy user interface for BrowseReporter. To see the most up-to-date features and interface please visit the BrowseReporter product page
The top reasons why companies track computer activity
- Deterring counterproductive work behaviors (CWB) such as tardiness, theft, workplace bullying, and absenteeism.
- Improving employee productivity by deterring excessive personal internet usage (social media, personal email, etc), providing managers with deeper insights into workflows, and time tracking.
- Protecting sensitive data against high-risk desktop activity use such as visiting potentially dangerous websites or uploading files to personal cloud storage accounts.
Enforce Acceptable Use Policies
Companies will use a computer use policy to communicate the acceptable use of work devices to their users. Having a documented acknowledgment of expectations is essential for ensuring that users are aware of their responsibilities, but it’s not the full solution.
A study by Dr. Kimberly S. Young & Dr. Carl J. Case found that among large firms, user activity monitoring software was rated as the most effective deterrent of inappropriate web use, followed by policies and training.
Workplaces that want to enforce their acceptable use policies will deploy software that monitors employee computer activity to provide managers with evidence of misuse. These desktop tracking software solutions provide activity logs with details such as internet activity, bandwidth consumption, and app usage.
Desktop use reports are incredibly valuable for understanding whether or not each user is using technology appropriately.
- Are they putting the network and company data at risk by visiting high-risk websites?
- Are they making their coworkers feel unsafe or uncomfortable at work by visiting explicit websites?
- Are they using company resources for personal tasks and projects?
- Are they misrepresenting their efforts and spending excessive amounts of time on unproductive web browsing? (Social media, sports, news, etc)
To improve the enforcement of their acceptable use policies companies will combine a user activity monitoring tool with web filtering software. This allows them to proactively block inappropriate websites while monitoring internet usage for websites that may need to be blocked or restricted.
Monitor Employee Productivity

Throughout their careers most employees will come to know a “shirker”—a coworker or colleague who goes out of their way to avoid doing their fair share of the work.
These shirkers are likely to engage in goldbricking and cyberloafing, spending much of their work time on social media and other unproductive websites rather than their assigned projects.
Shirkers are more than just a major productivity drain, they’re a serious detriment to employee morale. Once employees catch on that one of their team members is getting away with spending their days surfing the internet while they work tirelessly, resentment is guaranteed to follow.
Managers need to be aware of these morale-draining shirkers so they can address their behavior before it affects their team’s projects.
How computer tracking software improve productivity
- It provides disengaged employees, managers, and HR with a benchmark that they can use as a part of an Employee Performance Improvement Plan (PIP).
- Time tracking features provide real time evidence of staff members that are overextending their allocated breaks.
- Are deadlines being missed because employees are spending too much time surfing the web at work? A quick overview of their web browsing activity can help you tell.
- Employees with flexible schedules can be tracked to ensure that they are maintaining an acceptable level of activity.
Naturally, tracking employee computer usage is just one of many ways to spot when an employee isn’t working to their full potential. The key value in using monitoring tools to collect this data is to have a clear picture of what is happening throughout your entire workforce so you can make data-informed productivity management decisions.
Why do employees browse non-work websites?
- 34% of employees say they are not challenged enough
- 34% say they work long hours
- 32% say there are no incentives to work harder
- 30% are unsatisfied with their employment
- 23% say they’re bored at work
- 18% say it’s due to low wages
– Salary.com: Wasting Time at Work Survey 2013
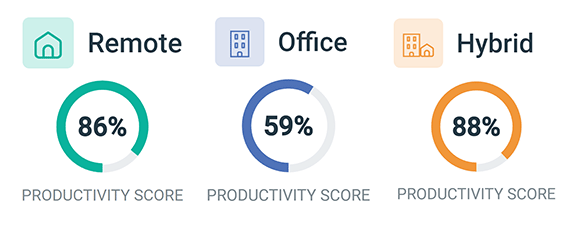
Improve Visibility of Remote Workers
The COVID-19 pandemic presented an urgent need for many businesses to provide work-from-home accommodations for their employees.
Unless you already managed a remote-first organization this transition must have been a serious learning curve.
Now that there has been plenty of time to settle down, you may have noticed that there are a lot of challenges when managing remote teams.
- How can you be certain that your remote employees are as productive working from home as they are in the office?
- Are your employees working as expected or are they taking advantage of the work-from-home arrangement to misrepresent their work hours?
- There are far fewer touchpoints when employees work remotely. How do you keep a pulse on their activity levels when everyone is so disconnected from each other?
Remote work isn’t going away anytime soon, either. 82% of U.S. office workers in a Global Workplace Analytics survey said that they want to continue to work from home, at least weekly, when the pandemic is over. If you’d like to remain competitive, you may want to consider offering remote work options well after the pandemic is over.
When it comes to remote workforce management many leaders worry that their employees will be distracted, or worse – actively disengaged – while they work from home. These concerns are perfectly normal, especially when assessing new employees that have not yet built trusting relationships.
While it’s true that remote employee computer tracking software can help identify poor performers, it can be used for so much more than that. The insights provided by these tools provide an opportunity to improve visibility and refine work processes when employees work from home.
The important thing to realize is that While managing a remote workforce comes with unique challenges, many of the very same skills and tools that you used to manage in-office workers can be used to manage remote employees as well.
The benefits of monitoring remote employees
- Fight Time Theft: With monitoring and time tracking software remote employees can easily prove that they are starting and ending their workdays at agreed-upon times. The timesheets of nonexempt employees can even be compared against their user activity data to prevent time theft while working remotely.
- Improve Visibility: 90% of employees in a Prodoscore survey stated that they are open to their employer having visibility into their daily productivity. The improved visibility offered by desktop monitoring and time tracking software provides remote employees with an effortless way to demonstrate their contributions.
- Self Management: Employees that work from home may worry that they are not as focused as they were in the office. These employees can use their activity data to self-monitor their productivity.
When using employee monitoring software to manage remote employees, it’s important to understand that desktop activity and automatic time tracking features are not reliable as a standalone productivity metric. Instead, this data helps to identify potential problems that may need to be addressed such as excessive distractions from key projects.
Optimize Bandwidth

To keep your business operations flowing smoothly your employees need access to reliable, secure, and fast internet connections. To ensure that your network performs at its best you need to limit the number of bandwidth hogs on your network.
What’s a bandwidth hog? A bandwidth hog is a source of internet traffic that uses a large amount of data. This includes large files that take a long time to download, video streaming services, and data-heavy applications.
Not all bandwidth hogs are inherently bad. Some business resources genuinely need to send or receive a large amount of data to meet your company’s needs. Unfortunately, if your network is strained from nonproductive bandwidth hogs there may not be enough bandwidth for mission-critical systems.
Monitoring bandwidth usage improves the speed of your network by identifying the sources of excessive bandwidth consumption so that you can address them. These tools will show you if employees are abusing bandwidth hogs such as video streaming services like YouTube, Twitch, or Netflix.
Depending on your environment blocking these sites altogether may be counterproductive; video sites such as YouTube can be truly valuable resources for tutorials.
So, how can you tell the difference between productive and unproductive use? Once the bandwidth usage reports have alerted you to a problematic site you can easily monitor employee web browsing history to see whether their use is providing value to the company.
Once you’ve identified the bandwidth hogs, you can decide what method works best for you: You can block them entirely or coach your employees to limit their bandwidth usage.
Once employees have been coached, you can continue to monitor their bandwidth usage to verify if they made the expected adjustments to their web browsing habits. If not, their data will provide clear evidence that further corrective actions are required.
Prevent Data Loss

The data that you can collect with employee tracking software isn’t limited to internet browsing history.
The tracking features of these tools also provide insights into other desktop activities such as the use of an unauthorized app, anomalous data transfers to USB devices, and suspicious login attempts.
Collecting this data is essential for making sure that confidential material isn’t leaving the company.
How tracking user desktop usage protects data
- Data Theft Prevention: Employees can easily steal sensitive data with something as simple as a USB flash drive. To prevent this you can block unauthorized portable storage devices and audit what data is transferred to work-issued devices.
- Audit Logons: Malicious insider threats can try to log in to company systems after hours and try to steal sensitive data undetected. Auditing when employees log in and out provides opportunities to detect these suspicious activities.
- Data Exfiltration: Anomalous bandwidth spikes, visits to unauthorized cloud storage sites, and high-risk USB activity are all potential indicators of malicious activity. A user activity monitoring tool can alert cybersecurity teams to these behaviors so they can determine whether data is at risk.
Time Tracking

Automated time tracking features help managers keep track of projects, tasks, and overall team productivity. From a team and project management perspective some time tracking tools will integrate directly with project management tools such as Trello, Asana, and Monday.
Automatic time tracking features allows team members to focus on their projects without manually clocking in and out for each task, though there is a risk that the team time tracking features will inaccurately attribute time spent on one project to another project. For this reason automatic team time tracking features are best used to validate existing team time tracking measures rather than outright replacing them.
For example, team time tracking software could be used for idle time tracking in your team; you can see which team members are actively using their workstations and which team members are spending project time elsewhere.
Protect the Business From Liability Risks

As an employer, you may tolerate a degree of personal use on company computers, but most companies need to be careful about what websites their employees are accessing. If employees use the internet to access websites with pornography or prejudiced content their employer may be held liable for their actions.
How employee monitoring protects companies from liability risks
- Data Security & Compliance: Companies that process or store sensitive data are typically required to maintain compliance with cybersecurity frameworks such as NIST SP 800-171. Monitoring employee desktop use can help companies detect an insider threat in real time before high-risk tasks result in a security incident.
- Hostile Work Environment: Allowing employees to access NSFW sites on work computers is a serious liability risk. Restricting and monitoring employee internet use helps to ensure that employees are using company resources as intended.
- Workplace Piracy: If employees are caught using pirated software on work computers there is a significant risk that their employer will be held liable. Software usage tracking provides a clear indication of each app that is used, allowing companies to spot unauthorized software.
While web filters are an excellent tool for preventing access to inappropriate content, they are not entirely foolproof. Some websites may not yet be on your block list or tech-savvy employees may even find a way to bypass web filters altogether. Combining a web filter with a user activity monitoring tool provides an added layer of defense against unwanted internet activities.
How to Use User Tracking Software

Want to learn how to track the computer use of your users? The best solution to monitor computer activities for you will depend on the type of activities you would like to track.
If you would like to try tracking user activity today, you can get started with a free trial of any of CurrentWare’s user tracking software solutions.
- AccessPatrol: Device control software to monitor and restrict USB storage devices
- BrowseReporter: User activity monitoring software to keep track of user internet activity, bandwidth consumption, and app usage
- BrowseControl: Web content filtering software for blocking a user from accessing a certain website or app.
- enPowerManager: Remote PC power management software to control and monitor PC power states, including logons.
How to Track Employee Internet Activity
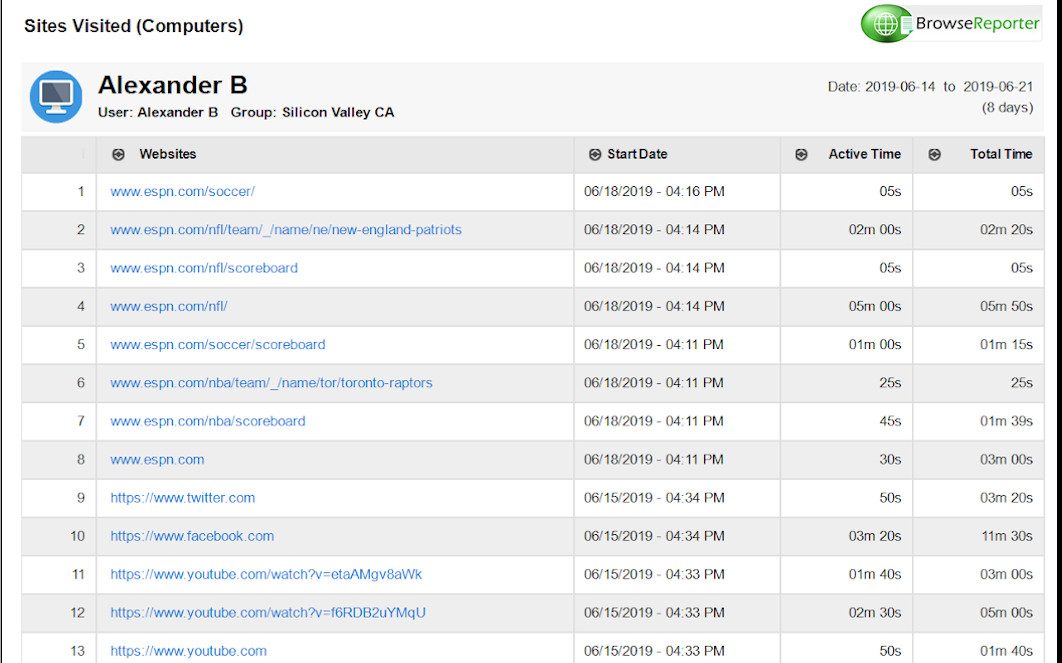
The best way to increase productivity and see what websites your employees have visited is with CurrentWare’s employee tracking software BrowseReporter. Using this software allows you to see the specific websites that your employees have visited, how long they have spent actively using the websites, and when they visited them.
Manually checking employee web browser history and viewing temporary internet cache files is unreliable as employees can use private browsing modes to hide their web browsing activity. A dedicated activity monitoring software such as BrowseReporter will track employee internet use for unproductive and suspicious activity while keeping that data safe from tampering to ensure accuracy.
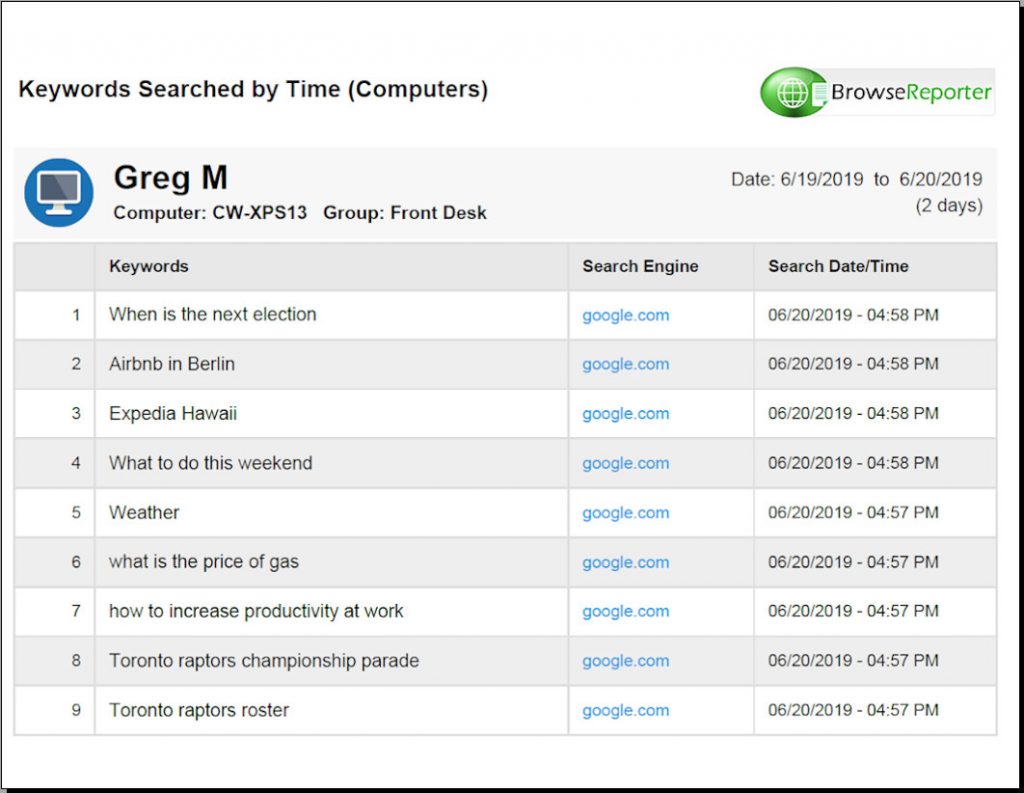
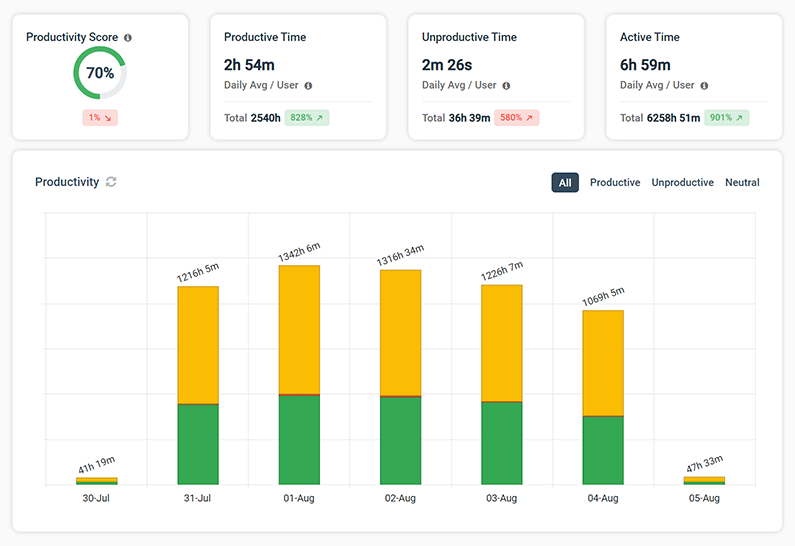
Sample internet usage reports
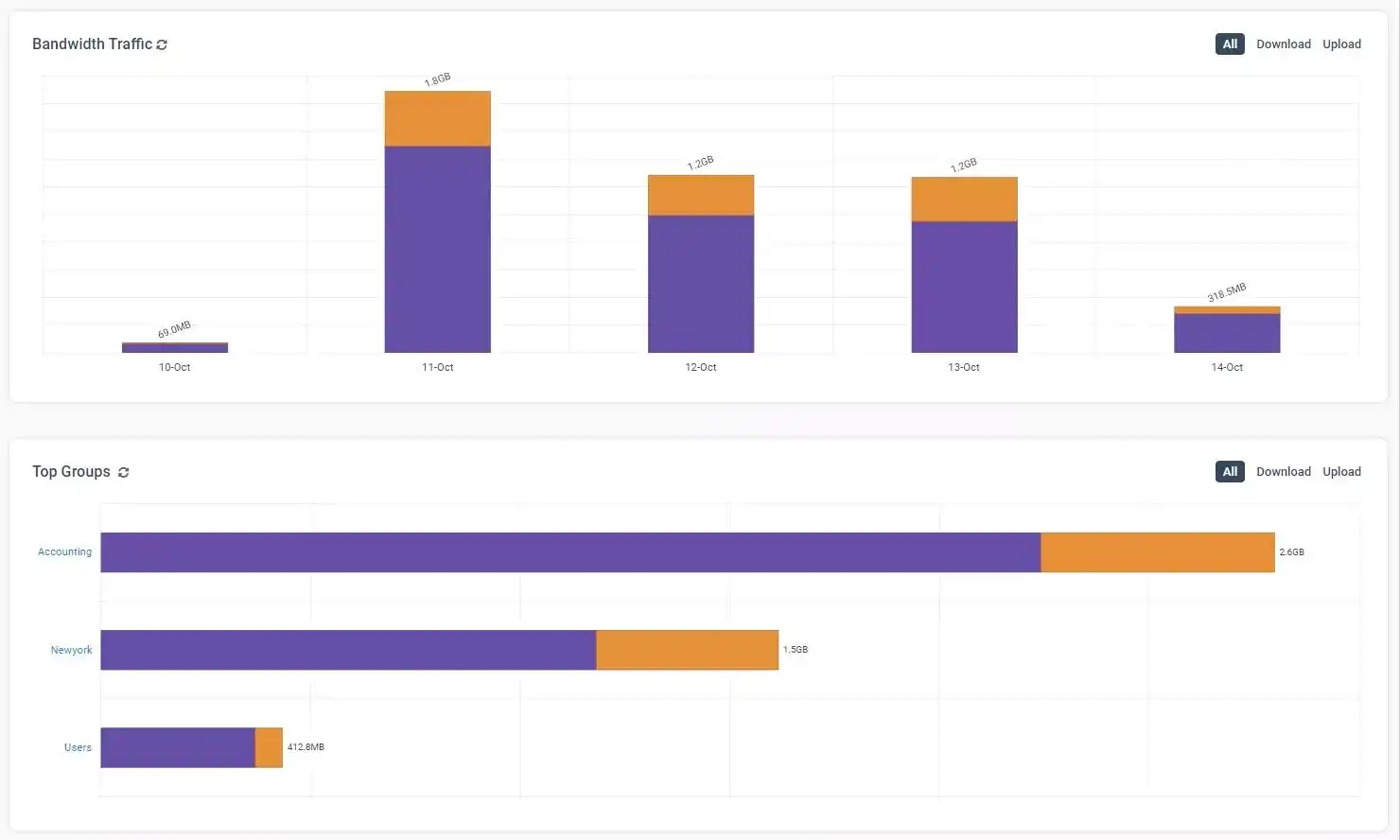
How to Monitor What Web Browsers Are Used

If you would like to know what web browsers your employees are using (Chrome, Edge, Firefox, Opera, etc) you can use BrowseReporter’s app usage monitoring features. After identifying what browsers are in use you can add any unsupported browsers to the blocked list of an application blocker to prevent further use.
Why monitor and limit the web browsers that employees can use?
- To reduce the workload on your IT department by allowing them to focus on troubleshooting, securing, and maintaining a single browser
- To reduce cybersecurity risks by limiting the amount of applications
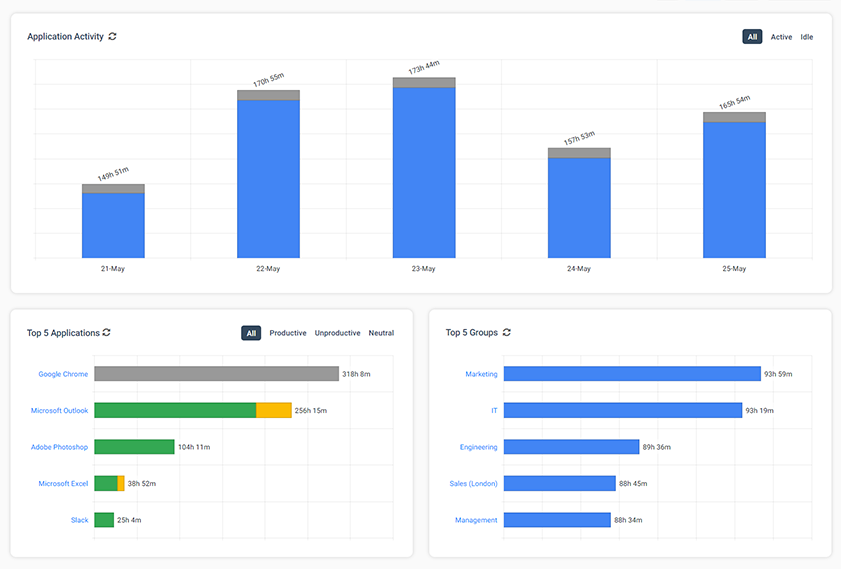
How to Monitor App Use
NOTE: The above video features a legacy user interface for BrowseReporter. To see the latest features and interface please visit the BrowseReporter product page.
The benefits of monitoring app usage
- Detect the use of shadow IT (unauthorized apps) in your network
- Reduce app sprawl by identifying and consolidating redundant software
- Track software adoption rates and license demand in your organization
Understanding the application usage of your employees is critical for streamlining your IT asset management process.
While the best practice is to lock down employee computers so that they cannot install unwanted software, this is not always enough to stop the use of an unwanted app.
For example, Software-as-a-Service (SaaS) platforms do not require a direct installation. Employees can simply sign up for a free account or get approval from their finance department for a paid account. This ease of acquisition has made app sprawl far more difficult to manage without some form of monitoring in place.
If there is any disconnect between your IT department and your procurement process, there is a significant risk that employees will use an app that your IT department is not aware of.
Even worse, there may even be non-IT employees in your company that have the permissions necessary to install programs on company computers.
Tracking the software that employees use
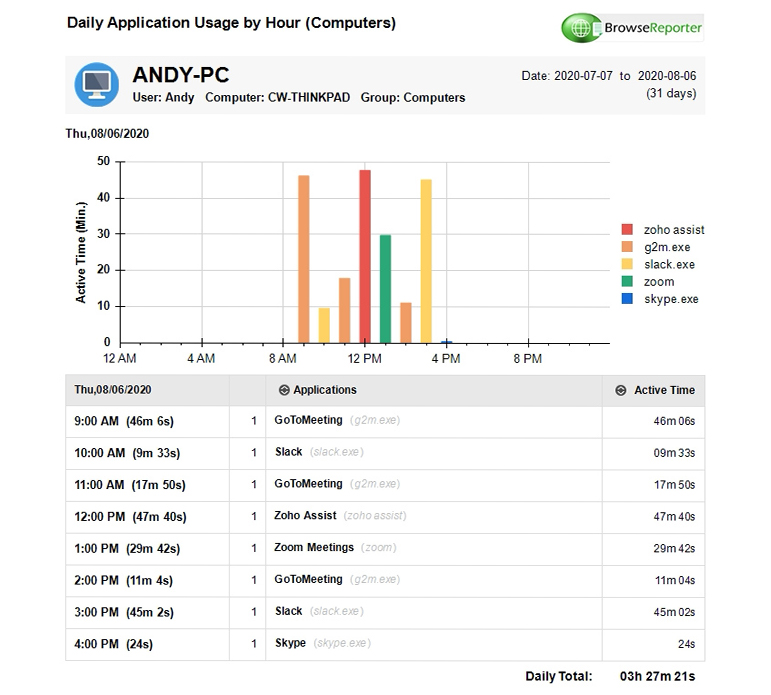
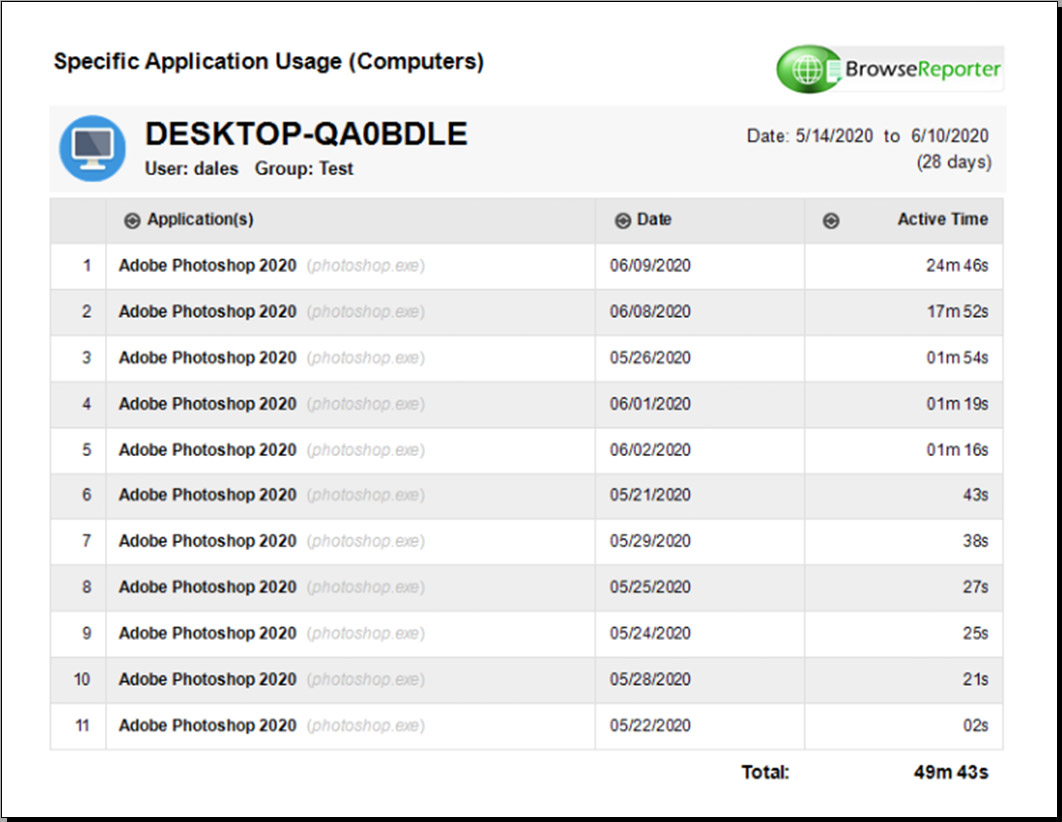
Ready to start tracking real-time computer usage? Get started today with a free trial of BrowseReporter, CurrentWare’s employee computer activity tracking software.
How to Monitor Computer Use Remotely
CurrentWare’s activity monitoring software BrowseReporter can also be used to monitor remote workers.
Options for monitoring remote workers with BrowseReporter
- Configure port forwarding to connect your off-site employee’s computers to your network.
- Have employees connect to a monitored desktop with a remote access solution (VPN, remote desktop, etc)
- Use the offsite mode feature to store computer usage data locally and have user activity reports automatically emailed to you on a set schedule.
- Deploy CurrentWare to the cloud
For more information, check out this article: How to Monitor Employees Working From Home
How to Monitor User Logons
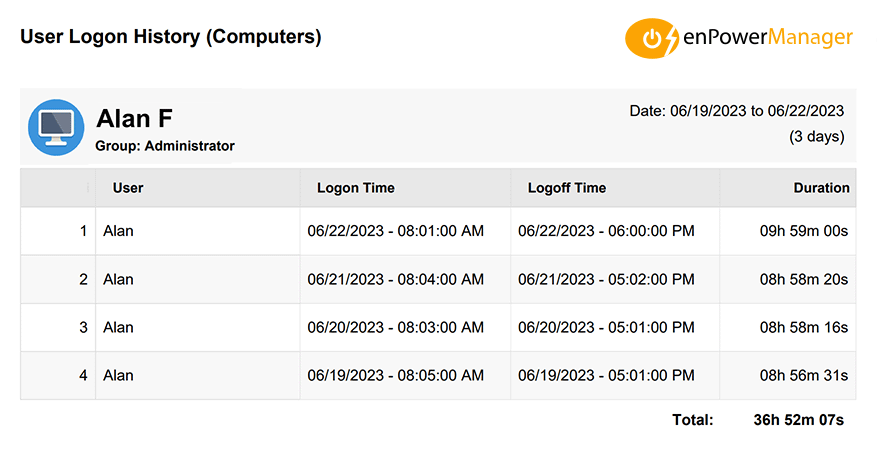
Malicious insider threats can try to log in to company systems after hours and try to steal sensitive data undetected. Auditing when employees log in and out provides opportunities to detect these suspicious activities.
CurrentWare’s remote power management software enPowerManager tracks when users log in, startup, shut down, or sleep their PCs. It also tracks user logon session time so you can easily see how long employees have been logged in.
To audit logon events with enPowerManager you simply need to install the CurrentWare client on your employee’s workstations and connect the clients to a self-hosted CurrentWare Server that is installed on-premises or on a cloud platform of your choice.
How to Monitor USB Activity
The best practice for preventing data breaches to insider threats with USB peripheral storage devices is to block them altogether with device control software such as CurrentWare’s AccessPatrol.
The thing is, it’s not always practical to completely block USB devices.
In environments where portable storage hardware is needed the devices that can be used can be limited to a company-approved Allowed List. As an added layer of protection, any file transfers to these USB devices can be monitored for suspicious activity.
Why audit USB device usage?
- Data Breaches: The loss, theft, or leakage of sensitive information is a significant event. Tracking employee USB device activity is one of many critical cybersecurity controls that protect data from insider threats.
- IT Asset Management: Monitoring what USB devices are used in your organization provides your IT department with a clear indication of what devices are in use, who is using them, and how often they are being used.
- Compliance: Many cybersecurity frameworks require audit trails that show how employees interact with data. These records are used to investigate potential security risks and determine the cause of data breaches.
How Much Employee Monitoring Is Too Much?

Is there such a thing as too much employee monitoring?
Yes, there most certainly is.
When it comes to what you are allowed to monitor, many believe that if an employee is using company equipment, on company time, and getting paid by the company, that the company has every right to monitor their equipment and what they are doing with it.
While in the majority of cases a company can leverage user activity monitoring software so long as the company has a legitimate business reason for doing so, it’s not always that simple. A variety of factors influence what employers can and cannot monitor.
There’s a resource management side to it as well; user activity monitoring software captures a lot of data. Will you or a member of your staff be manually reviewing the reports? Will you use alerts to notify you of specific activities? Will you only be checking in when other concerns prompt you to dig deeper?
How granular your approach is will depend on your company’s resources, risk tolerance, applicable regulatory or contractual requirements, and policies.
FREE WHITE PAPER
Best Practices for Monitoring Employees
In today’s privacy-conscious world employers need to monitor employees in a way that is transparent, minimally invasive, and respectful of employee privacy.
Want to use monitoring tools to get instant visibility into employee productivity, engagement, and PC usage? Read this white paper to learn the best practices for monitoring employees in the workplace.
Is Employee Monitoring Legal?

Yes, but there are limitations.
Even in jurisdictions where employers are allowed to use user activity monitoring software to monitor their employees, there are limitations as to what can and cannot be monitored. For examples, other forms of monitoring such as GPS tracking and audio recording are much more regulated than basic computer monitoring features.
When determining how employee monitoring will be used in your organization it is important to understand the potential privacy implications for your employees and what factors influence your right to monitor your users.
For example, organizations that are subject to GDPR are required to use a Data Protection Impact Assessment (DPIA) that evaluates their method of tracking against the potential impacts it may have on employee privacy.
Legal factors that influence employee monitoring
- Jurisdiction: Employee monitoring laws vary depending on where the employer and the employee reside. A catch-all approach may not be suitable for a multinational company.
- Union Agreements: Independent agreements with unions and other workers’ rights organizations may include limitations about what employers can track and how data will be used when monitoring employees.
- Proportionality: Different forms of monitoring may be restricted based on potential privacy impacts. For example monitoring individual keystrokes is more invasive than monitoring web browsing history as keystroke monitoring has a greater risk of capturing sensitive personal information such as passwords.
- Expectation of Privacy: Employees have a greater expectation of privacy on their personal devices. Monitoring laws may even go so far as to restrict the degree of monitoring that can take place when employees use business equipment for personal use.
- Company Policies: Has the company made a legitimate effort to inform employees that they are being monitored? Are employees clear about whether or not they have a reasonable expectation of privacy on workplace equipment?
As the relationship between workplace privacy and employee monitoring evolves there is a strong chance that data privacy laws that are similar to California Consumer Privacy Act (CCPA) and Europe’s General Data Protection Regulation (GDPR) will continue to be adopted.
When it comes to determining how to legally monitor your employees, the best practice is to consult with a legal professional. Employee monitoring laws vary considerably and as the world becomes more aware of data privacy there will be new laws and regulations to consider.
Best Practices for Using Employee Activity Apps
Ready to use employee PC activity tracking software in your business? Follow these best practices to create an effective employee monitoring strategy that is transparent, minimally invasive, and respectful of employee privacy.
If you would like to dive deeper into this topic, you can download our free white paper Employee Monitoring: Best Practices for Balancing Productivity, Security and Privacy.
Be Transparent About Employee Monitoring
“If organizations wish to monitor their employees, they should be clear about its purpose and that it brings real benefits. Organizations also need to make employees aware of the nature, extent, and reasons for any monitoring”
Spokesperson from the UK’s Information Commissioner’s Office
Employees that are not aware that they are being monitored, why they are being monitored, and how they are being monitored are less likely to find employee monitoring acceptable.
A survey by Dtex Systems found that 77% of employed Americans would be less concerned with employee monitoring so long as they are transparent about it and let them know up front.
Being openly transparent about workforce monitoring is essential. Using an employee activity tracker as a form of PC spy software risks harming employee morale and creating a culture of distrust in your company.
How to be transparent
- Allow employees to access their own time tracking and real-time activity data. This gives them the autonomy to see exactly what is being captured. They can also use this data to monitor their own productivity, which is more empowering than a top-down approach.
- Disclose the scope of employee monitoring during onboarding and within employee handbooks/policies.
- Ensure that employees understand how data is being collected, what data is being collected, and how it will be used.
- Involve a representative sample of employees during the planning process so that any potential concerns can be addressed and mitigated.
As an employer it is important that you do not lead with the assumption that your employees have the same expectations of privacy in the workplace as you do. Use company policies, handbooks, and other tools to set a clear indication as to whether or not your employees should expect privacy when they use company computers.

Workplace Monitoring Policy Template
- Disclose your company’s intent to monitor employees in the workplace
- Set workplace privacy expectations for employees
- Meet transparency requirements for compliance with privacy laws
Get started today—Download the FREE template and customize it to fit the needs of your organization.
Have Employees Sign an Acceptable Use Policy

In addition to improving transparency, an acceptable use policy is a perfect opportunity to provide your employees with clear expectations when they use technology in the workplace. Having these documents on file also provides an opportunity to demonstrate that your employees have provided you with informed consent for employee monitoring.
What to include in an acceptable use policy
- What types of uses are permitted and prohibited
- Whether or not there is a reasonable expectation of privacy on company equipment and networks
- Whether or not their workstations are subject to monitoring, what types of monitoring will take place, and how the data will be used
- What corrective actions may be taken when the policy is not abided by
Avoid Excessively Invasive Monitoring
“Employers must not use tech to control and micromanage their staff. Monitoring toilet breaks, tracking, and snooping on staff outside working hours creates fear and distrust. And it undermines morale.”
Frances O’Grady, General Secretary of the British Trades Union Congress (As reported by Raconteur)
When you monitor your employees the best practice is to only monitor what is needed to meet your organization’s goals.
You must also weigh the potential impacts on employee privacy against the benefits to your business. If a less invasive form of monitoring can adequately meet your company’s goals it is best to consider that alternative.
When it comes to actually viewing the data you collect, you should also consider whether or not you have a reasonable business case for doing so. For example, archiving employee emails is a standard business practice for many organizations but snooping through employee conversations without any suspicion of malfeasance will simply come off as spying rather than monitoring.
Example 1: Secretly Monitoring Employees & Monitoring Keystrokes
“In my view, information collected by keystroke logging software becomes ‘necessary’ within the meaning of section 33(c) of the Act only when there is no less intrusive way of collecting sufficient information to address a particular management issue.
Frank Work, Information and Privacy Commissioner of Alberta, 2005
Furthermore, surreptitious use of the software will result in ‘necessary’ information only where forewarning employees that such a program will be used means that information needed for management cannot be collected.”
In June of 2005 the Alberta Office of the Information and Privacy Commissioner released Order F2005-003. In this order Frank Work, the Information and Privacy Commissioner of Alberta, addressed a complaint against Parkland Regional Library.
The library had secretly installed keystroke logging software on the workstation of an information technology employee. When the employee discovered the computer spy software they made a complaint to the Office of the Information and Privacy Commissioner as they were concerned that this covert monitoring may have captured their personal banking information, including their usernames and password.
The library’s justification for using the keystroke monitoring tool was that they wanted to ensure that their workstations were being used for work purposes and that any personal use by employees be reasonably limited and controlled.
While the Commissioner did agree that using software to know how employees are using their working time may be necessary, the library had given their employee permission to conduct personal internet banking on their company-provided workstation during non-working time and they installed the overly-invasive monitoring software without the employee’s knowledge.
Due to the lack of transparency and the high probability that keystroke logging would capture sensitive personal information, the library’s use of the software was deemed to be unjust. The Commissioner also noted that less-intrusive means were available for collecting the information needed for managing.
Example 2: Monitoring Personal Devices (BYOD)

Using desktop monitoring apps for tracking employee activity on a personal device is likely to reveal sensitive personal information. This includes protected classes of information such as religion, sexuality, and health status.
Employee monitoring software also requires you to install some kind of monitoring agent on their individual devices. Employees using personal devices for work may not be comfortable having tracking software installed on their devices, especially if there is any doubt as to what is being captured and when.
Rather than directly monitoring an employee’s personal device, you can have them remotely connect to a monitored company-owned computer. That way any and all monitoring that takes place is limited to working hours on a computer that is intended to exclusively be used for work purposes.
Another alternative is to schedule employee monitoring to only occur during designated work hours. This allows employees to treat their devices as work-only devices during the workday while having full freedom to use the devices for personal use in their off-hours.
You can take this approach even further by providing employees with access to their own activity data. That way they can clearly see what is (and is not) being captured.
Avoid Using Employee Activity Trackers to Micromanage

When you first use employee monitoring software you’ll become acutely aware of computer use habits that you may not have been previously aware of.
When evaluating this data it’s important to realize that these browsing habits have always been there; you’re simply being given a granular overview of it.
At first it may be tempting to immediately curtail any and all computer activity that is considered unproductive, but being overzealous when doing so may actually negatively impact the overall productivity of your employees.
Consider this: As a leader you need to do all you can to enable your employees to perform their best. Employees that are empowered to improve their own productivity perform better than those who feel they are being subject to micromanagement.
If an otherwise high performing employee is immediately scolded for checking their Facebook during a slow period at work, they’re going to feel like they are not trusted to perform at their best.
Besides, computer activity data isn’t a reliable standalone productivity metric. There are other factors that need to be considered before deciding whether or not corrective actions need to be taken.
What to consider when evaluating activity data from monitoring tools
- Data Context: Raw data about how employees are using the internet and computer applications is not a reliable standalone productivity metric. What is considered unproductive or distracting for one employee may actually be work-related for another.
- Job-Adjacent Tasks: Monitoring software can’t tell when employees are engaged in tasks that don’t require using the computer, such as phone calls and problem solving. Small periods of inactivity throughout the course of the workday is completely normal.
- Is Cyberloafing Bad?: Brief periods of “unproductive” web browsing can actually be a productivity booster. According to Brent Coker of the University of Melbourne so-called “cyberloafing” can have a positive impact on employee productivity, but only so long as it does not consume more than 12% of their work time.
Ensuring that employees retain their autonomy when being monitored will go a long way to maintaining morale and satisfaction in the workplace. The best practice is to limit direct action on individual employees to serious infractions such as blatant time theft or browsing NSFW sites.
Rather than addressing every minor infraction you should use this data to make informed productivity management decisions. For example, excessive unproductive web browsing may be an indication that employees or departments are underutilized. You can use this data to identify opportunities to adjust work processes and reduce excessive idle time.
Naturally, if underperforming employees are maliciously spending excessive amounts of time on unproductive web browsing and their deadlines are being missed you will need to step in. But if otherwise high performing employees are maintaining their standard of excellence it is best to trust them to manage their own productivity.
Keep Employee Data Safe

Employee monitoring data can be highly sensitive depending on its nature. When you monitor your employees you need to treat the data the same way they would any other sensitive data. This includes providing it with protections such as restricting who can access the data and keeping it within a secured network.
Conclusion
Employee computer activity tracking tools are valuable assets for improving productivity and security.
If you would like to use these tracking tools in your business you first need to understand the data privacy laws of your jurisdiction, determine how you will monitor employees in a way that is transparent and fair, and find the best employee monitoring software for your needs.
Improve Employee Productivity With
CurrentWare’s Remote Employee Monitoring Software
Ready to get advanced insights into how your employees spend their time? Reach out to the CurrentWare team for a demo of BrowseReporter, CurrentWare’s employee and computer monitoring software.
- Improve Productivity
Track unproductive web browsing and idle time to detect time-wasting - Save Time With Intuitive Reports
User-friendly reports make it easy to understand employee computer activity - Enhance Visibility
See how employees spend their time—even on Terminal Server and Remote Desktop Services!