Trusted by
& many more
Trusted by
& many more
ISO 27001 & ISO 27002 Compliance Requirements
You Can Address With CurrentWare
| ISO 27001 Control | CurrentWare Modules & Features |
|
ISO 27001:2022 Controls:
ISO 27001:2013 Controls: Annex A.8.3 — Media Handling
Annex A.8.3 is about media handling. The objective in this Annex is to prevent unauthorized disclosure, modification, removal or destruction of information stored on media.
|
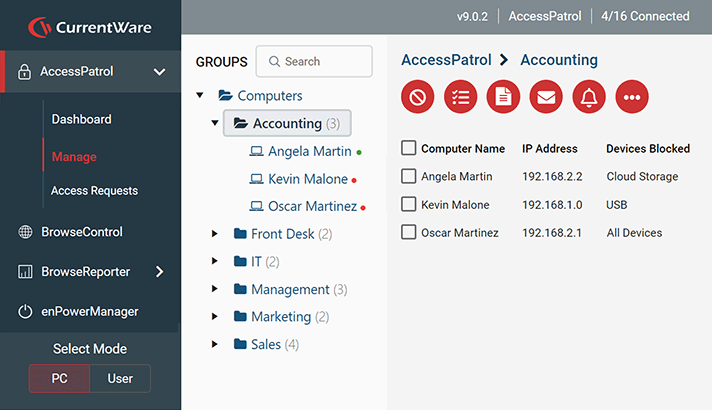
AccessPatrol
|
|
ISO 27001:2022 Controls:
ISO 27001:2013 Controls: Annex A.12.1 — Operations Security
A.12.4 — Logging and Monitoring Annex A.12.1 is about Operational Procedures and Responsibilities. The objective of A.12.1 is to ensure the secure operation of information processing facilities. Annex A.12.4 is about logging and monitoring. The objective in this Annex A area is to record events and generate evidence.
|
AccessPatrol
BrowseControl
BrowseReporter
enPowerManager
|
| ISO 27002 Control | CurrentWare Modules & Features |
|
8.12 Data Leakage Prevention (DLP) ISO 27002 control 8.12 modifies risk by implementing technical measures that proactively detect and prevent the disclosure and/or extraction of information. |
AccessPatrol
BrowseControl
BrowseReporter
Learn More: CurrentWare’s data loss prevention solutions |
|
8.16 Monitoring Activities ISO 27002 Control 8.16 modifies risk by optimizing monitoring activities to identify anomalous behavior and assists in the prompt analysis of information security events and incidents. |
AccessPatrol
BrowseReporter
enPowerManager
|
|
8.22 Web Filtering If employees visit websites that contain viruses, phishing materials, or other types of illegal information, this may expose corporate networks and information systems to security risks. With BrowseControl you can restrict the websites that employees can access to mitigate the risk of malicious sites.
|
BrowseControl
|
We’re Here to Help
The CurrentWare team prides itself on its high-quality customer support. We will support you every step of the way—whether you’re just starting your free trial or actively using CurrentWare in your network.
At CurrentWare, customer success is our priority at every stage of your journey. We take pride in providing high-quality and reliable pre and post-sale support to make your experience exceptional.
We offer the same level of high-quality support to all of our customers—no extra fees or packages necessary!
Mike Noseworthy
Customer Support Lead
Product Training
CurrentWare provides the documentation, training, and other resources you need to take full advantage of the capabilities of our products.
Technical Support
Our expert support team is here to help you. Reach out to us over email, live chat, or phone from 8:00 AM – 6:00 PM ET, Monday to Friday.
See What Our Customers Have to Say
The reports are very easy to understand and the fact that they can be emailed to you on a schedule is amazing, and have made finding productivity killers VERY easy. Customer support has been fantastic every time I've had to reach out to them; I highly recommend them!
Kristen S, Associate IT Director
The Coding Network, 700+ Employees
As a 'novice' I was able to set up with help from support in about an hour. Previous software took forever and didn't work as advertised. This software worked right out of the box.
Dr. Gerard B, Office Manager
Medical Practice, 2-10 Employees
In my nearly 40 years in the IT business I’ve worked with a lot of support teams. I really appreciate CurrentWare going the extra mile to help me get the most out of the product. They’ve definitely outweighed any of the other competitors that I’ve looked at.
J.S, Managed Services Provider
Vehicle Dealership, 150-200 Employees
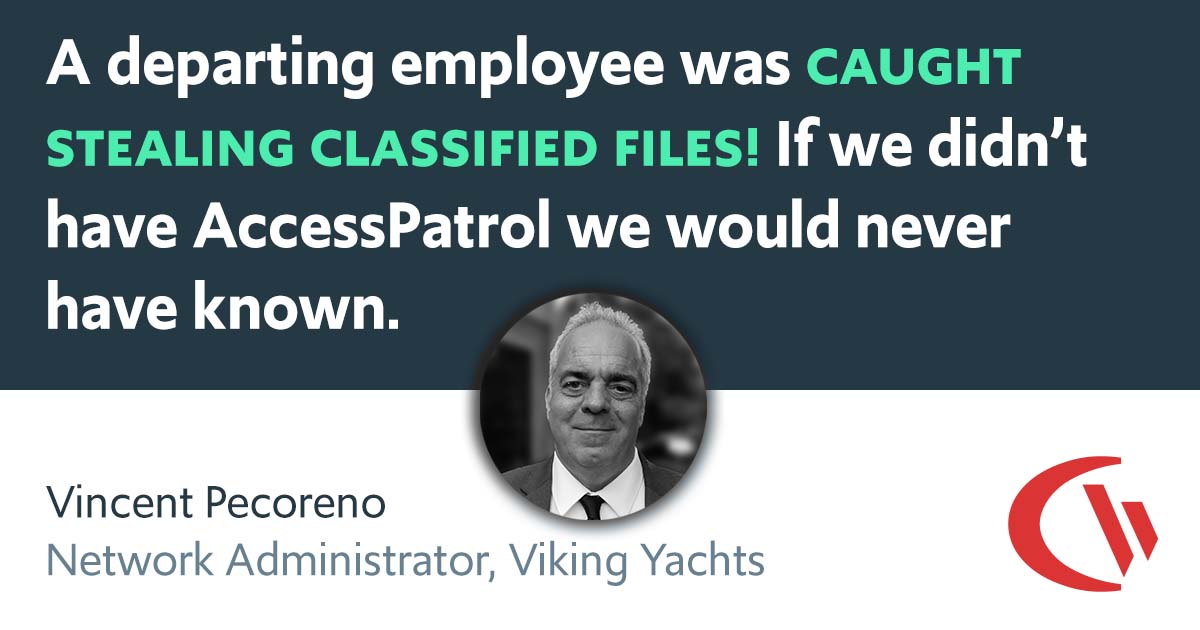
We have experienced data leaks by dishonest employees in the past and [CurrentWare's] AccessPatrol has helped us avoid them and work with greater security and peace of mind for us and our customers.
Julio V, Head of Information Technology
Financial Services Industry, 10,001+ employees
FREE DOWNLOAD
Removable Media Policy Template
Download this data security policy template to prevent data leakage to USB flash drives and other removable storage devices.
- Set data security standards for portable storage
- Define the acceptable use of removable media
- Inform your users about their security responsibilities
CurrentWare's Key Features
User Activity Monitoring
Track web browsing, software use, search queries, and more
Screenshot Monitoring
Take automatic screenshots or remotely view desktops
Track Software Usage
Get insights into software usage trends in your organization
Transparent & Stealth Modes
Run silently in the background or provide notice of monitoring
Block USB & Other Devices
Set full access, read only or no access on storage devices
Device Whitelist
Allow only authorized storage devices to be used
Block File Transfers
Prevent files from being transferred to portable storage
DLP Activity Reports
Track file transfers, storage device use, file operations, and more
Block Websites
Block websites based on
URLs & content categories
Block Downloads/Uploads
Prevent uploading and downloading based on file type
Application Blacklisting
Block specific Windows
applications from launching
PC Power Management
Remotely track and control PC power states
Central Web Console
Save time with a central admin console; optionally integrate Active
Directory OUs or security groups
Platform Security
Protect your CurrentWare console
with 2FA, passwords, privilege
management, and more
Offsite Management
Extend onsite security policies to computers running outside the corporate network
SQL Server Supported
Database scaled for enterprise and
large business operations using
Microsoft SQL Server
Learn How to Meet These Compliance Requirements With CurrentWare
NERC CIP
Protect TCAs & BCSI From Insider Threats
ISO 27001
Increase the Maturity of Your ISO27K ISMS
NIST 800-171/53
Protect Controlled Unclassified Information
CIPA for Education
Qualify for the FCC’s
E-Rate Program

Cyber Essentials
Critical Security Controls For Your Assessment

CMMC
Protect CUI to qualify for DoD contracts