🆕Live Screen Monitoring, Audit Logins, DLP Upgrades & More (v9.0.2)
CurrentWare version 9.0.2 is here! This update introduces user activity monitoring upgrades to BrowseReporter such as live screen monitoring and on-demand screen captures, a variety of AccessPatrol DLP enhancements such as the ability to control HID devices, and much more!
As a CurrentWare customer, these quarterly product updates are included at no additional cost as a part of your subscription.
Need help upgrading? Our team is here to assist you every step of the way. We offer comprehensive documentation, training resources, and personalized support to ensure a smooth transition.
Should you have any questions or need further assistance, please reach out to our support team.
What’s New in CurrentWare Version 9.0.2?
 AccessPatrol Updates
AccessPatrol Updates
- ⌨ Whitelist Human Interface Devices (Keyboards, Mice, etc)
block HID that use the USB protocol such as mice and keyboards, while still allowing HID that are on an Allowed List (whitelist) - ⏬ Detect Unauthorized File Transfers (Upload/Download Tracking Updates)
Get alerts when high-risk keywords are detected in the names of files transferred via uploads/downloads, network drives, and cloud storage services

 BrowseReporter & enPowerManager Updates
BrowseReporter & enPowerManager Updates
- 📷 On-Demand Screenshots & Live Screen Monitoring
Remotely view employee screens and take real-time screenshots on-demand; combine with trigger-based and interval-based screenshots for complete coverage - 🔑 Login Sessions Dashboard & Active vs Idle Timeline
Get immediate insights into user activity patterns with an at-a-glance overview of when they’re actively using their computers. Readily see how user login/logoff times correspond with their active and idle time from a convenient dashboard - 👩💻 Track When Apps/Websites Were Last Used
View each users’ last accessed time for specific apps/websites for greater insights into recent activity and resource usage
 🔒 Quality-of-Life Updates, Security Improvements & Bug Fixes
🔒 Quality-of-Life Updates, Security Improvements & Bug Fixes
- Automated reports on CurrentWare operator activity (audit logs)
- Bulk apply licenses based on computer groups
- Misc bug fixes, performance enhancements & security updates
Learn more about updates to CurrentWare in our release notes.
🔔IMPORTANT
Version 8.0+ Required Before Further Troubleshooting
The CurrentWare team regularly releases updates to our software with valuable new features alongside critical security, performance, and compatibility updates.
As of January 31, 2024, the CurrentWare support team requires customers to upgrade to version 8.0 or above before providing further technical support.
This procedural change is necessary to ensure we continue to meet our commitment to delivering exceptional customer service and providing the highest level of security and performance.
Access to new versions is included as a part of your subscription. So long as you are an active customer you can get the latest version for free.
Our team is here to assist you every step of the way. We offer comprehensive documentation, training resources, and personalized support to ensure a smooth transition.
Should you have any questions or need further assistance, please reach out to our support team.
 AccessPatrol Data Loss Prevention Updates
AccessPatrol Data Loss Prevention Updates
AccessPatrol v9.0.2 introduces two data loss prevention upgrades
- ⌨ Whitelist Human Interface Devices (Keyboards, Mice, etc)
- ⏬ Greater Insights Into File Uploads/Downloads (Alerts/Logs)
These upgrades build upon CurrentWare’s existing data loss prevention capabilities to provide the advanced visibility and control your security teams need to keep data safe against insider threats.
New to AccessPatrol? Learn more about AccessPatrol’s role in keeping sensitive data safe or get started today with a free trial
PREVENT THE USE OF UNAUTHORIZED HIDs
⌨ Whitelist Human Interface Devices (Keyboards, Mice, etc)
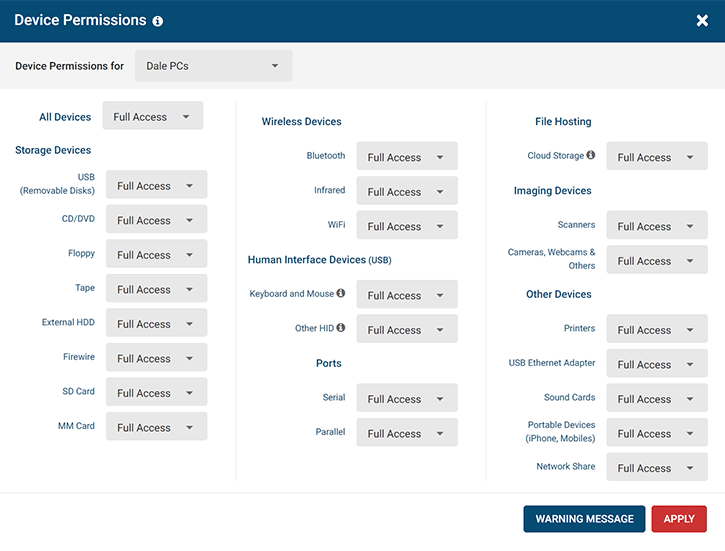
Does your Cyber Liability Insurance provider require you to block all unknown HID devices? Are you concerned about the security risks associated with users connecting unapproved keyboards, mice, and other human interface devices (HID) to the computers on your network?
We have the solution!
Thanks to feedback and suggestions from our customers, AccessPatrol’s peripheral devices whitelist now has the ability to block HID that use the USB protocol such as mice and keyboards, while still allowing HID are on an Allowed List (whitelist); devices are identified based on vendor provided IDs.
As with AccessPatrol’s other peripheral device restriction capabilities, your HID restriction policies can be customized based on groups of computers or users.
How to Use This Feature
Cybersecurity & Data Loss Prevention
By whitelisting HID, you can create a list of trusted devices that can connect to your computers, while blocking any unknown or unwanted ones. This can help you avoid potential threats such as keyloggers, malware, or data theft.
IT Asset Management (ITAM)
Enforce compliance with hardware inventory and acceptable use policies by ensuring that only authorized users can use HID devices
Learn More
- Which Devices Can I Control With AccessPatrol?
- How To Allow Only Specific Company Authorized USB HID Keyboards & Mice
DETECT UNAUTHORIZED FILE TRANSFERS
⏬ Greater Insights Into Uploaded/Downloaded Files (Alerts/Logs)
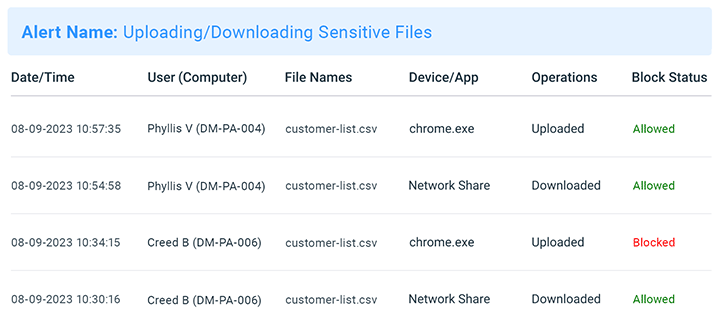
In version 9.0 we introduced the ability for AccessPatrol to monitor file uploads and downloads from sources such as cloud storage apps, network share drives, desktop apps, and more. This worked alongside BrowseControl’s download/upload blocker to provide greater visibility and control over the files your users could transmit to the web and across your network.
New enhancements in v9.0.2 to detect unauthorized file transfer attempts
- Email Alerts for Uploads/Downloads, Network Drive & Cloud App Transfer Activities
AccessPatrol has new alerts that can be configured to trigger when users download, upload, or transfer files with high-risk keywords in their file names - Log Blocked File Transfer Attempts
AccessPatrol’s activity log can now report what files have been blocked/allowed based on your security settings across the CurrentWare Suite
How to Use This Feature
Enforce Acceptable Use Policies
Monitor the file activity of your employees to ensure that they are not using authorized apps and websites for personal use or performing other actions that go against company policies.
Data Loss Prevention & Compliance
Detect and prevent data breaches to avoid the costs associated with them, such as fines, lawsuits, and reputation damage. You can also protect your intellectual property and trade secrets from being stolen or leaked by unauthorized parties.
Learn More

 BrowseReporter & enPowerManager Updates
BrowseReporter & enPowerManager Updates
CurrentWare v9.0.2 introduces significant enhancements to the platform’s user activity monitoring capabilities, building off of existing features to provide you with the insights you need to ensure the security and productivity of your workforce.
Some of these enhancements require both BrowseReporter and enPowerManager. If you’d like to take advantage of the best reporting capabilities CurrentWare has to offer, ensure you have both modules enabled. If you need a module that is not a part of your current subscription you can reach out to our sales team for an upgraded license—No need to re-deploy!
These enhancements include
- 📷 On-Demand Screenshots & Live Screen Monitoring
- 🔑 Login Sessions Dashboard & Active vs Idle Timeline
- 👩💻 Track When Apps/Websites Were Last Used
New to BrowseReporter? Learn more about BrowseReporter’s role in increasing your employees’ productivity, transparency, and accountability or get started today with a free trial
REMOTELY VIEW & CAPTURE EMPLOYEE DESKTOPS
📷 On-Demand Screenshots & Live Screen Monitoring
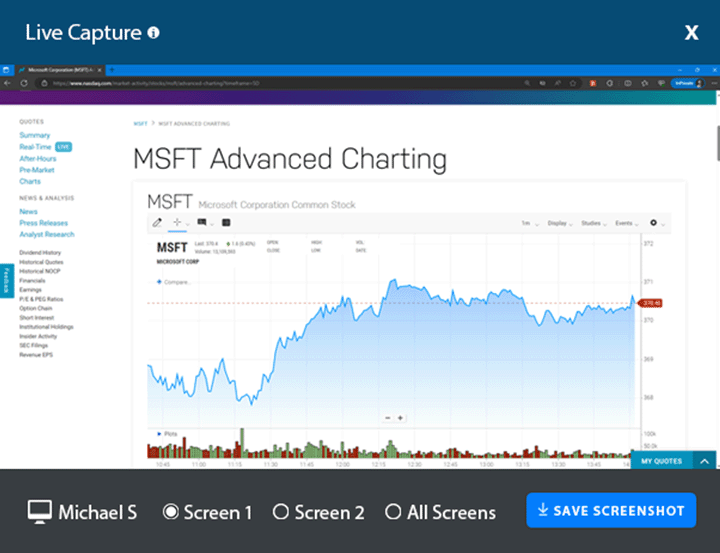
With BrowseReporter’s Live Screen Monitoring feature you can remotely view employee PC screens in real-time and take screenshots on-demand.
Get a live feed of exactly what an employee is doing on their computer and remotely capture ad-hoc screenshots of their desktop, even on multi-screen setups.
Combine this feature with the trigger-based and interval-based screenshots for complete coverage of employee computer activity.
How to Use This Feature
- Cybersecurity & Compliance
Watch high-risk users for unsafe data handling and inappropriate behavior, such as visiting NSFW websites or attempting to access confidential information - Employee Training & Troubleshooting
Get a live stream of an employee’s computer for remote troubleshooting and training, or monitor new hires in real time to identify inefficiencies and compliance concerns - Employee Productivity
Remotely view the screens of employees to check-in on their current priorities and activities without walking to their desks and potentially interrupting their workflow
Important Notes
- This feature requires port 8988 to be open by default; if you’d like to use a different port number this can be optionally reconfigured. | Learn More
- In v9.0.2 on-demand screenshots are individually saved locally to the device being used to capture screenshots; they cannot currently be found in the feed used by the interval-based and trigger-based screen captures.
Learn More
GET INSIGHTS INTO EMPLOYEE WORK HOURS
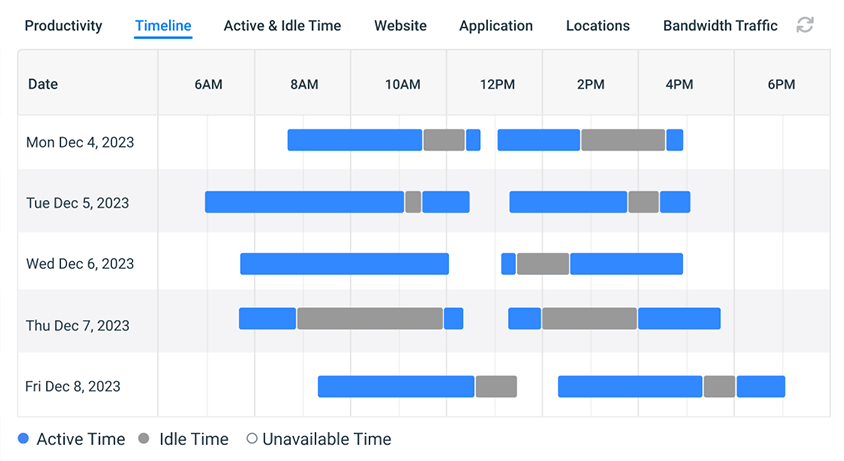
🔑 Login Sessions Dashboard & Active vs Idle Timeline
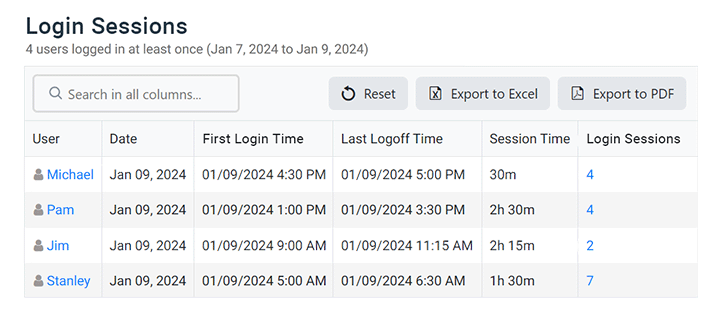
With the new login session dashboard and active vs idle timeline view you can readily see how user login/logoff times correspond with their active and idle time from a convenient dashboard.
With an at-a-glance overview of when your employees are actively using their computers, you will gain new insights into user activity patterns such as frequency of breaks, when employees start/stop working on their computers, and instances of users walking away from their computers without locking them or logging out.
How to Use This Feature
Productivity Monitoring
- Identify and analyze start/stop times to assess employee working patterns
- Understand peak productivity times and allocate tasks accordingly
- Identify and address potential productivity bottlenecks or distractions
Attendance Tracking & Project Management
- Compare timesheets for specific projects or tasks to an employee’s actual usage
- Ensure accurate records of employee attendance, login, and logoff times with supporting documentation
- Encourage accountability by having a transparent record of work hours; address any discrepancies or concerns related to time management
Resource Planning
- Efficiently allocate resources based on real-time data on employee availability
- Identify periods of high and low activity to optimize workforce scheduling
Remote Work Monitoring
- Monitor remote employees to ensure they are actively working during scheduled hours
Security and Compliance
- Enhance security by monitoring login/logoff activities for anomalies such as high-privilege employees logging in to sensitive systems after hours
Employee Well-being
- Monitor work patterns to identify potential burnout or stress factors and promote a healthy work-life balance based on actual working hours
Important Notes
- The login sessions dashboard requires both BrowseReporter and enPowerManager to be enabled. If you need a module that is not a part of your current subscription you can reach out to our sales team for an upgraded license—No need to re-deploy!
- “Idle time” is defined as a period of time where there has been no mouse or keyboard input from an end-user for X minutes. You can configure the idle time threshold by going to Settings> BrowseReporter > Tracking Options | Learn More
Learn More
GREATER INSIGHTS INTO RECENT ACTIVITY
👩💻 Track When Apps/Websites Were Last Used
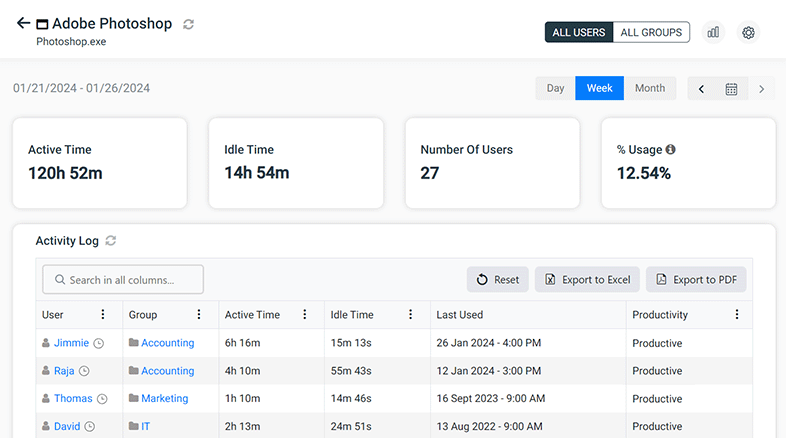
With this new data point in BrowseReporter you can readily view each users’ last accessed time for specific apps/websites.
You will find this data point in various activity logs across BrowseReporter’s user activity dashboards as a dedicated column in the dashboard for a specific app or website.
How to Use This Feature
Software Asset Management
Monitor web and application utilization rates to uncover opportunities to optimize software spend by decommissioning or consolidating underutilized tools
Monitor Productivity & Time Management
See how much time is spent on different apps/websites and identify any distractions or inefficiencies
Optimizing Device Performance And Storage
Find out which apps/websites are used frequently and which ones are rarely or never used; uninstall or disable underused tools free up space and resources on your device
Cybersecurity & Liability
Check if any apps/websites have been accessed by users that should not be able to, or if users are accessing sensitive apps/websites at anomalous hours
Learn More
 Quality-of-Life Updates, Security Improvements & Bug Fixes
Quality-of-Life Updates, Security Improvements & Bug Fixes
The CurrentWare team is committed to providing a high-quality and secure product. With each CurrentWare release, we include quality-of-life and security updates such as performance improvements, bug fixes, and minor features that make the CurrentWare Suite even easier to use.
Automated Reports on CurrentWare Operator Activity (Audit Logs)
Get scheduled summaries of your CurrentWare operator’s web console activities such as changes made to security policies, which operator was responsible for the change, and when the change occurred. | Learn More
Bulk Apply Licenses Based On Computer Groups
The search box in Settings > Licensing > License Computers can now search by group names rather than just computer names, allowing your Operators to apply licenses in bulk | Learn More
50+ Miscellaneous Bug Fixes, Performance Enhancements & Security Updates
As always, we recommend keeping your CurrentWare deployment up-to-date to take advantage of the latest functionality, stability, and security developments. | How to Upgrade
Conclusion
CurrentWare version 9.0.2 is available now. To get access to the latest features you will need to update your CurrentWare deployment. If you’re new to CurrentWare you can get started today with a free 14-day trial of the latest version.
Learn more about updates to CurrentWare in the release notes.
See More CurrentWare Product Updates:
- Improved Reporting, AD Security Groups, Category Descriptions, and More! (v10.0.2)
- UI/UX Updates, Performance Enhancements, QoL Improvements (v10)
- Live Screen Monitoring, Audit Logins, DLP Upgrades, and More! (v9.0.2)
- USB Access Codes, Security Enhancements, and More! (v9.0.1)
- Full Historical Release Notes


