Cybersecurity Tips for Small Businesses on a Limited Budget

Cybersecurity for small businesses doesn’t have to be expensive, but it is critical. According to the 2019 Data Breach Investigations Report by Verizon, 43% of reported data breaches involved small business victims. Worse yet, the U.S. National Cyber Security Alliance estimates that 60% of all SMBs are forced to shut down their operations following an attack.
As a small-to-medium business owner, you have big security needs that shouldn’t be limited by over-priced and complicated cyber security solutions forcing you to take on yet another costly monthly bill. In this guide I will outline the importance of cyber security for small businesses and show you the most important steps you can take to improve your data loss prevention strategy on a budget.
Table of Contents- Key Takeaways
- Is Your Small Business Making These Cyber Security Mistakes?
- Why Small Businesses Need To Make Data Security A Priority
- The Greatest Data Security Risks Faced by Small Businesses
- The Top Cyber Security Priorities For Small Businesses
- How to Improve Data Security on a Budget
- The Best Cyber Security Resources For Small Businesses
- Conclusion
Key Takeaways

- Small-to-medium businesses (SMB) are valuable targets for cyber criminals. Because of the monetary value of the data they hold and their lack of cyber security resources, small-to-medium businesses are frequently targeted by opportunistic threat actors.
- Cyber security is an essential investment. The cost of a data breach is devastating for businesses of all sizes, but SMBs are particularly vulnerable. The U.S. National Cyber Security Alliance estimates that 60% of all SMBs are forced to shut down their operations following an attack
- Security awareness training is a priority. The majority of security threats can be managed by training employees on common methods used by attackers to breach networks such as phishing, social engineering, and cracking insecure passwords.
- Data loss prevention is possible on a budget. While security software will require an initial investment, there are cost-effective security solutions and best practices that will help protect a small business from viruses and other cyber threats.
Is Your Small Business Making These Cyber Security Mistakes?
Free eBook:
5 Common Cybersecurity Threats in 2020
Learn cost-effective solutions to protect your business
against cybersecurity threats in 2020
1) Thinking That Cyber Security is Too Expensive to Invest in

Small-to-medium business owners and startups have a much more personal relationship with money than large enterprises. Every expense hits much closer to home as that money could very well be coming from your pocket, the pockets of early investors, or from the modest revenue that you’d much rather be spending on the things that will directly grow your business.
Here’s the thing…
Improving the cyber security capabilities of your business doesn’t have to be expensive! While there are absolutely some things that will require resources (time for training staff, investing in data loss prevention software, etc), any short term gains you might see from investing that money elsewhere will quickly go down the drain in the event of a data breach.
Your business – any business – simply cannot afford to skimp on securing the sensitive data in your custody. You don’t necessarily need the most expensive security softwares, multi-staff dedicated IT security teams, and your own dedicated data storage servers – you just need to invest in cost-effective resources that make sense for your business’ security needs.
That said, there is a very real barrier that small-to-medium businesses face when it comes to investing in cyber security software – economies of scale. Smaller organizations have less users and a smaller revenue base to work with, which means they are not able to take full advantage of volume discounts like large enterprises do.
All hope is not lost, though. We’ll touch more on the types of cost-effective (and free!) resources your small business needs to improve its data loss prevention capabilities later in this article.
2) Assuming That You’re Not a Valuable Target For Cybercriminals

A common mistake made by small business owners is assuming that they aren’t a valuable target for threat actors (the security industry term for ‘hackers’). Shockingly, 68% of SMBs in the 2015 Security Pressures Report from Trustwave believed their organization was safe from cyberattacks and data compromises – you cannot afford to make this mistake!
All small businesses have sensitive data that they need to protect:
- Customer information
- Payment data from customers and merchants
- Human resources data (employee SIN #s, performance data, etc)
- Intellectual property and trade secrets
- Personally identifiable information (PII)
Threats to data security are entirely industry agnostic and small businesses have far more valuable data than they might realize. Even if you’re not a tech company you are still a valuable target to scam artists, cybercriminals, and insider threats because of the value associated with the sensitive data you need to operate your business.
3) Thinking That You Won’t Need Help From IT Security Professionals

When you’re bootstrapping your business, it’s highly likely that having a dedicated IT person on staff isn’t going to be financially feasible. Your business may also genuinely not have as great of a need for regular ongoing IT maintenance as other companies – but that doesn’t mean you don’t need IT security!
There are going to be occasions where your company needs to seek professional help from dedicated IT security professionals. Fortunately, there are ways that small business owners can leverage the expertise of cyber security experts without breaking the bank.
Small businesses with semi-regular IT needs can outsource their IT work through Managed Service Providers (MSP) that specialize in data security services. With an MSP on retainer a small business will always have access to critical security expertise without having to maintain dedicated staff members. MSPs will also help guide businesses through their IT software and hardware needs, saving them considerable time that would be spent on research and testing multiple solutions.
Small businesses need professional IT help when:
- They are first starting to outline and address their cyber security needs.
- They are undergoing a period of expansion where they’ll be introducing new network infrastructure.
- They regularly handle sensitive data & they do not have the in-house resources to address data security needs.
- They need assistance to meet compliance with data security and data privacy frameworks such as GDPR, CCPA, HIPAA, and PIPEDA.
While many businesses opt for a break/fix model where IT support is only called on to fix immediately identifiable issues, budgeting for routine IT maintenance where feasible can help further maintain the security of your network and keep things up and running. Continual IT maintenance will help save on costs associated with downtime and data breaches, making it a valuable investment.
Why Small Businesses Need To Make Data Security A Priority
Neglecting Security Makes Your Business Less Trustworthy

Reputation is everything for small businesses, particularly in local circles where word quickly gets around if the business simply isn’t up to snuff. While not every consumer or potential client is going to think to ask about your approach to data security, they will certainly steer clear if it develops a reputation of negligence and mismanagement of sensitive data.
Aside from the cost of a data breach, being unable to demonstrate that you’re serious about your corporate data security responsibilities is going to guarantee that any potential partners are going to think twice before trusting your business.
Don’t think that a large company will want to work with a small-to-medium business? Think again!
Larger companies love working with small businesses, and the partnerships they make can be of great benefit for both parties. The large companies benefit from the agility and flexibility that their small business partners have and the small businesses benefit from the connections and reputation that their larger partners have – it’s a total win-win!
If you want to play ball with established enterprises, your business needs to step up its data security game big time.
The Cost of a Data Breach Can Ruin Your Business
All it takes is one nasty data breach to irreparably end your business. The U.S. National Cyber Security Alliance estimates that 60% of all SMBs are forced to shut down their operations following an attack
IBM’s 2019 Cost of Data Breach Report found the average cost of a breach to be $150 per record stolen. While there are plenty of examples of companies that have recovered from costs of data leaks, more often than not these companies are better equipped to withstand the fallout.
The costs of a data breach are more than fines:
- Lawsuits from customers affected by the breach
- Lost revenue and higher customer acquisition costs (CAC) from a damaged reputation
- Resources spent investigating and addressing the cause of the breach
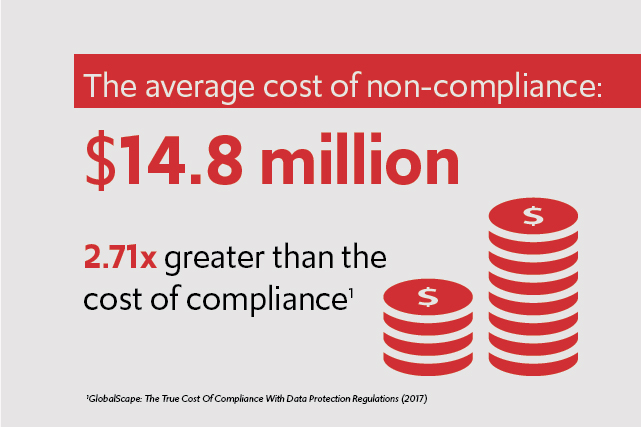
The average costs of compliance for the companies surveyed by GlobalScape in 2017 was $5.47 million and the average cost of non-compliance was $14.8 million – 2.71x greater than the cost of compliance. When the cost of a data breach is compared to the investment of maintaining adequate data security and data privacy standards, there’s a clear winner.
The Greatest Data Security Risks Faced by Small Businesses
An internet connection is the single greatest vulnerability to data security, but you’ll be hard pressed to find a business that doesn’t benefit from having an internet connection in some way. The key is to be aware of the data security risks associated with the internet and plan your cyber security strategy accordingly.
Social Engineering & Phishing Scams

If you’ve been using email for a fair stretch of time, it’s almost guaranteed that you’ve stumbled upon a phishing email before. Those cryptic emails claiming to be your ticket to wealth aren’t just annoying spam messages, they are the most common and dangerous tool used by threat actors to infiltrate your network.
62% of businesses experienced phishing and social engineering attacks in 2018. Phishing attacks can be far more convincing and sophisticated than what you might be used to seeing, so don’t think your employees are guaranteed to see these messages for what they are.
A particularly personalized phishing attack – known as spear phishing – can be used by threat actors to craft eerily convincing phishing emails that can convince your employees to visit malicious websites that install computer spy software on your network. Spear phishing attacks use personal information collected from social media and other available sources to directly relate to their target, greatly increasing the chances that they’re would-be victims will fall for their trap.
A Lack of Cyber Security Training

Security software simply isn’t enough to protect data. While dedicated tools are absolutely important for providing your business with the critical security controls it needs to address vulnerabilities, investing in the security knowledge of your employees is the single greatest step you can take to keep corporate and customer data secure.
Consider this – your employees are on the front-lines and interacting directly with the endpoints (computers, laptops, mobile phones, etc) that are vulnerable to attacks from threat actors if not used properly. Your employees need to be equipped with adequate security awareness training that covers common workplace vulnerabilities.
Personal Devices in the Workplace

In an effort to improve procurement efficiency and reduce costs, many workplaces will allow their employees to use their personal devices at work. This practice is known as “Bring Your Own Device” or “BYOD”, and it can be a serious security problem if it’s not well executed.
That’s not to say that employees should never be allowed to use personal devices, just that business owners and security teams need to be aware of the risks associated with BYOD policies and plan accordingly.
Why BYOD can be dangerous:
- How personal devices are used outside of work is entirely out of your control and there is no guarantee that each employee is using their personal devices securely.
- Mobile device management (MDM) apps that are often used to track devices when they’re lost or stolen are likely to violate the privacy of employees.
- Employees that mix personal and work devices may accidentally leak data by transmitting it away from a secured database and onto personal cloud storage accounts.
- How personal devices are used naturally increases their risk profile, whereas work-only devices are often limited in what they are used for.
Insider Threats

As a business owner you will naturally build a close relationship with your employees. Your employees are what make your business possible and they have understandably earned your trust, but that doesn’t mean that they shouldn’t be managed as part of your data security plan.
Insider threats aren’t always malicious. While you will absolutely need to have a plan for preventing jaded employees from loading company secrets on a flash drive and selling it to your competitors, more often than not insider threats are simply employees that are careless.
How good employees become insider threats:
- Clicking on a malicious link in a phishing email
- Falling victim to social engineering tricks
- Temptations to sell company data when they’re struggling financially
- Not taking their cyber security responsibilities seriously (or not understanding them at all!)
- Accidentally sending a sensitive file to the wrong person
- Developing resentment after being fired or not receiving an expected promotion/salary increase
- Circumventing security controls to ease productivity blocks caused by strict security policies
- Misplacing technology such as USB storage devices, laptops, and phones.
According to Verizon’s 2019 Data Breach Investigations Report 34% of all breaches that happened in 2018 were caused by insider threats. The proximity and access that employees have to a small business make them a likely source of cyber security incidents if not managed appropriately.
The Top Cyber Security Priorities For Small Businesses
With all of the information that’s available about cyber security, it can be overwhelming for a small business owner to get started in improving their data security capabilities. To help you get started, here are the most critical data loss prevention steps that small businesses need to take. Once this essential framework is established, you’ll be in a much better position to start incorporating more advanced security controls as your data security needs evolve.
Assess The Cyber Security Risk Level of the Business
This is one of those stages where having the advice of a security expert is going to pay off the most. Even if you perform a security risk self-assessment (and you really should!), there’s bound to be less obvious vulnerabilities that can be missed by the untrained eye.
When developing a cyber security risk management plan, it is important to tailor the security controls based on the risk level associated with the device. Endpoint devices can be placed into three risk categories: Low Risk, Moderate Risk, and High Risk.
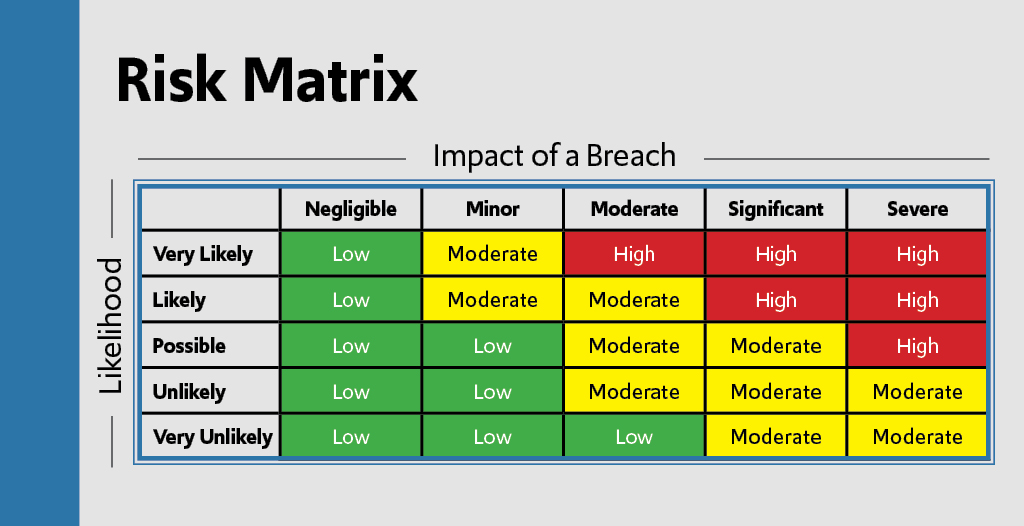
The unfortunate reality of any cyber security plan is that you cannot protect everything equally – your risk management plan will need to prioritize higher risk devices and networks over those that pose a lower risk
What to Include in Your Assessment
- Data: What data does your business collect, where is it stored, how do you protect it, who has access to it, and how valuable is it to potential threats? If that data is lost or stolen, how will that impact your business?
- Devices: What devices will have access to the network? Make note of operating systems and device types (laptop/desktop/phone/etc) as they will have their own unique security considerations.
- Threats: What threats is my business vulnerable to, and how can I mitigate those risks? Include the potential data and business impacts of natural disasters, theft, loss, system failures, insider threats, and third parties.
- Controls: Based on the known threats, what can be implemented to mitigate them? Data backups, employee training, service-level agreements with third parties, limiting privileges, etc
- Prioritize: Compare the probable threats to the costs of mitigating them and their likelihood of occuring. When doing data loss prevention on a budget this process is critical as you realistically cannot protect against everything all at once, you will need to prioritize based on what can be reasonably protected against and what is likely to happen.
Following the initial assessment, make a plan to revisit your risk planning at least once a year. As your business grows and develops your risk profile will naturally fluctuate and you may need to account for new threats that have emerged.
Get Cyber Security Training for Employees

If your employees aren’t adequately equipped with the knowledge they need to use technology safely in the workplace they’re bound to slip up eventually. Do not let your employees be your weakest link – make sure they’re kept up-to-date on their security responsibilities and the steps they can take to protect sensitive data.
If the means for training employees is not available in-house, seek out dedicated training services and free online materials. At the end of this article I’ve provided links to free and paid resources to get you started.
Manage The Security Risks Of Third Parties

The 2013 data breach of Target that resulted in the payment card data of 41 million consumers being leaked was caused by a third-party vulnerability. A small HVAC company that had a virtual connection to one of Target’s servers was hacked as a result of a malware-laced email. Once the HVAC company was compromised, the threat actors had a direct connection to Target’s network where they could continue their attacks. Target was forced to pay $18.5 million as a result of the data breach – do not let your small business fall victim to security gasps of third-party vendors.
Businesses of all sizes rely on third-party vendors to bolster their capabilities without heavily investing in cultivating those capabilities internally. When you establish a connection with a third party that lets them have access to your business and its systems, you still have data security responsibilities that you need to attend to.
When selecting a third-party vendor, you need to perform due diligence to ensure that they’ve done everything they can to ensure the security of their systems and the data that you’ll be sharing with them. Where possible limit any direct access that the third party has to your systems and set clear data security expectations in a service-level agreement (SLA).
Backup Critical Business Data

With the increased prevalence of ransomware attacks, the dire need to have secure backups of data is greater than ever before. Ransomware attacks infect computers and maliciously encrypt files, only (potentially) releasing the encryption key when a ransom is paid.
Even without the threat of ransomware, any data that your business cannot afford to lose needs to have redundant copies to prevent the loss of that data.
Critical business data should be securely backed up in 3 places:
- Onsite #1: Placed on a hard drive that is easily accessible and regularly backed up. Hard drives are cheaper and more robust than SSDs, making them a better alternative for backing up data.
- Onsite #2: A second copy of the very same data that is in the first harddrive; this protects data from loss due to hard drive failures. This hard drive should be disconnected from the main network to prevent loss due to malware, malicious deletion, or power surges.
- Offsite: An offsite backup can be made through cloud storage or by storing data on a physical drive/server that is kept off-site. This protects data from loss due to floods, fires, theft, and other disasters.
For small businesses that do not have the time to invest in physical backups, cloud storage providers provide the peace of mind that comes with data redundancy without the hassle. While cloud storage vulnerabilities do exist, leading providers implement robust security measures that protect the data from external threats. Your main priority will be ensuring that employees do not have unrestricted access to cloud storage backups of data as they could potentially download data they shouldn’t be accessing.
Reduce the Risks of Insider Threats

As I mentioned before, insider threats are a serious problem for businesses of all sizes. While you may get away with physically monitoring for suspicious and undesirable behavior when you have a small team (though that’s really not the best use of your time), this sort of insider threat management strategy simply isn’t going to be scalable as your business grows.
How to protect data from insider threats:
- Protect against common cyber security mistakes by investing in regular training for your employees.
- Make security a priority in your company to create a security-conscious workforce
- Fight social engineering attacks by developing procedures for how visits from external contractors are communicated and authorized.
- Have a plan for how you will secure data when employees are dismissed. Have someone stay with them while they clear out their desk and go through a checklist of every account and device they had access to.
- Use employee monitoring software to watch for unexpected or suspicious behavior.
- Block USB devices from being used by employees that have access to high-risk data
Set Clear Policies and Procedures

Policies and procedures that are focused on cyber security planning provide your workforce with clear guidance for how they are expected to use technology and data in the workplace. At minimum you should include rules and processes for data handling, the acceptable use of devices, and the cyber security responsibilities of your employees.
Develop a Cyber Incident Response Plan

Data breaches are not a matter of if – they are a matter of when. Proactively planning a cyber incident response plan will ensure that your business is well prepared to respond to a data breach incident. The last thing you will want to be doing when resolving a security issue is incident response planning from scratch; by having the key considerations worked out in advance you can focus your energy on remediation and executing the response plan.
Tips for Preparing for & Responding to a Data Breach:
- Cyber Insurance: If the use of sensitive data is a regular part of your business operations, consider investing in an insurance policy that is dedicated to covering the expenses of a cyber incident. These insurance plans will often help with the costs of restoring and recreating lost data, hiring digital forensics experts to investigate the breach, credit monitoring for affected data subjects, and legal counsel for your business.
- Data Breach Notification: Depending on your jurisdiction and industry you are likely to have a central authority that you will be required to report certain categories of data breaches to. Make note of who that is in advance and be prepared to file a report in the event of an incident. You should also plan for how you will notify affected customers and other data subjects.
- Customer Support: If the data that was breached contains sensitive customer information, you will need to consider how you will help your customers in their time of need. On a limited budget you may not have the resources necessary to provide a dedicated customer support line but you should consider identity theft monitoring and information resources that you can provide to affected customers.
- Determine Roles: Map out in advance who will be responsible for executing the stages set out in your data breach response plan. This will help to keep everyone focused on their core responsibilities and make your response more efficient and organized.
- Documentation: As the nature of the breach comes to light, maintain detailed documentation that outlines what has been discovered. This will prove to be valuable information for reporting the incident and protecting your business against future attacks.
- Security: Once a data breach is discovered, take any affected devices offline and leave them running. This will remove them from your network while maintaining potential evidence that will be useful in a digital forensics investigation. You should also update the credentials of any affected user accounts to ensure that they aren’t accessible to threat actors.
For more information, this incident response checklist from Process Street has the specific steps you can take immediately after an IT security incident. This FTC article also has great insights into responding to data breaches.
In addition to the steps you will take in response to a security incident, you should also document the data loss prevention and cyber security measures that your business takes on a day-to-day basis. This will not only serve as important evidence of your business’s honest efforts to secure data, it will also provide you with a clear overview of what can be improved in the future.
How to Improve Data Security on a Budget
Follow an Employee Offboarding Checklist
The employee offboarding process presents significant data security risks. Employees have intimate access to corporate data, insider knowledge of the organization’s systems, and a level of trust that can allow them to steal data undetected.
- 70% of intellectual property theft occurs within the 90 days before an employee’s resignation announcement
- 88% of IT workers have stated that they would take sensitive data with them if they were fired
- 72% of CEOs admit they’ve taken valuable intellectual property (IP) from a former employer
- 50% of respondents in a Symantec survey say they have taken information, and 40% say they will use it in their new jobs
These vulnerabilities need to be addressed as part of any insider threat management program. Click here to learn the best practices for protecting data during a termination and gain access to a downloadable IT offboarding checklist.
Block Unsafe Websites

A web filter is a cost-effective security tool for protecting your business against web-based threats. CurrentWare’s content control software BrowseControl supports category filtering to proactively prevent employees from stumbling on known malicious websites that can stealthily infect your network with drive-by downloads.
Category filtering makes internet access permissions easy to manage by seamlessly blocking millions of websites across over 100 URL categories such as porn, warez, social media, and viruses.
Benefits of a web filter:
- Network Security: Malicious and compromised websites can stealthily infect networks with drive-by downloads. All an employee has to do is stumble upon one of these sites on social media or a phishing email for an exploit to compromise the network. A web filter adds an added layer of security by blocking these websites from being accessed in your network.
- Increase Productivity: Nearly 82% of employees surveyed in the “On Cyberslacking: Workplace Status and Personal Internet Use at Work” report admitted to using the internet for personal reasons during work hours. A web filter can be used to block access to commonly abused websites such as social media and games.
- Data Loss Prevention: Unauthorized cloud storage, social networks, and web apps provide channels where sensitive data can be leaked. A web filter can proactively prevent access to these channels and stop employees from mishandling data.
- Workplace Behavior: A web filter limits opportunities for employees to access NSFW content such as pornography, reducing inappropriate web usage that would otherwise contribute to a hostile work environment.
Identity & Access Management (IAM)
Password Managers & Multi-factor Authentication (MFA)
Practicing proper password hygiene is the single most important thing that a business with a limited security budget can do to protect data. Unfortunately poor password hygiene is far too prevalent, with a shocking 59% of users surveyed in the LastPass Psychology of Passwords Report admitting to reusing passwords.
Reused passwords are an absolute nightmare for data security. If a previously used password is made public through a data breach, any accounts that the password was used on are now vulnerable. Using unique passwords for each account limits the amount of damage that can happen when an account is compromised, but it’s tedious to remember hundreds of unique passwords. That’s where password managers come in!
With a password manager such as LastPass, KeePass, and 1Password, your employees can generate unique and complex passwords that are then encrypted and stored in the password manager. With this method all that needs to be remembered is a single strong master password – no more password reuse!
How to make a strong master password:
- Make It Unique: Make it entirely unique from any other password used on other accounts. This includes not simply adding a few numbers to the end of an old password. If a previous password is breached, an attacker will build off of that password to try to access other accounts.
- Long & Simple: Think of your master password as more of a passphrase. Use a series of words to create long, simple passwords rather than short and complex ones. These are easier to remember for those that need it and harder for attackers to guess. For a detailed explanation of why this is more secure, check out this comic from XKCD.
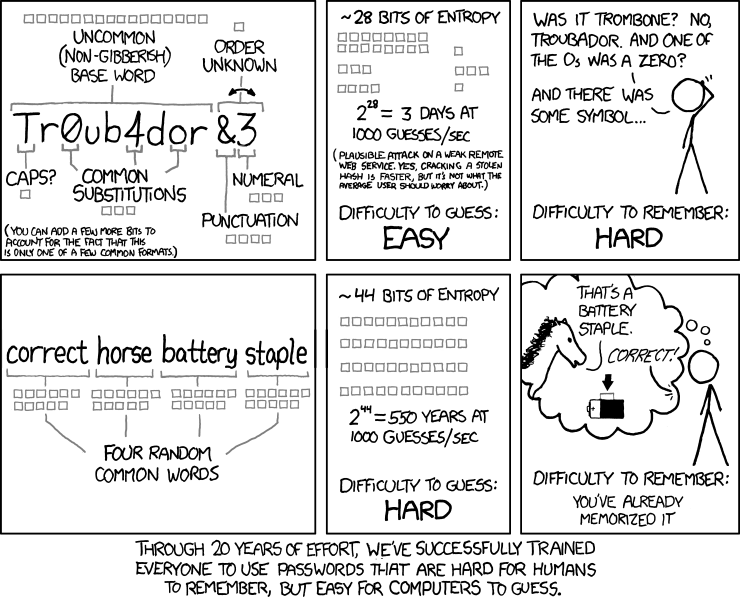
Unfortunately, even a strong password can be a security risk if it is somehow breached. That’s where multi-factor authentication (MFA) comes in. With MFA, your employees will be required to provide a second piece of authentication to prove they are who they say they are. With MFA enabled you will have an added layer of security to prevent an attacker from gaining access into corporate accounts.
Examples of MFA:
- Physical hardware keys such as the YubiKey that need to be inserted into the computer
- One-time passwords sent to an email account or to a phone number via SMS (SMS is less secure as a highly motivated attacker can pretend to be an employee to get the phone number’s texts sent to their cell)
- An authenticator app such as Authy or Microsoft Authenticator
- PIN #s that are only stored locally on the device, preventing logins to local services without direct access to the machine
Identity As A Service (IDaaS) & Single Sign-on (SSO)
There is something problematic about using password managers in a professional setting. What do you do if an employee that has dozens or hundreds of company account passwords leaves on bad terms or is fired?
If the former employee is feeling vindictive this could lead to serious damages if the account passwords cannot be reset in time. Even without this aspect of risk, resetting passwords is an incredibly time consuming process. That’s where identity as a service (IDaaS) & single sign-on (SSO) come in.
Traditionally, access permissions are handled with dedicated tools such as Microsoft’s Active Directory (AD). As cloud-based applications became more popular, IDaaS providers stepped in to help fill the gaps. While Microsoft also offers a cloud-friendly version of AD called Azure Active Directory, IDaaS providers have proven to be valuable for businesses that need added support for their identity management.
SSO is remarkably similar to password managers in that they allow employees to access all of the services they need at work using a single login. The key difference is that SSO also lets you manage the access permissions that individual employees have. SSO will also provide IT admins with greater details into the context of each login such as where the user is, the device they’re using, and their IP address.
Identity-as-a-service vendors not only provide SSO capabilities, they also cover the access permissions that employees have to business applications. These features are critical for ensuring that employees only have access to the resources they need and nothing more.
If your business uses a lot of different applications, you will want to consider investing in IDaaS. This will add another monthly expense to your budget but it’s a worthwhile investment to help make authorization-based security scalable.
Monitor Computer Activity On Your Network
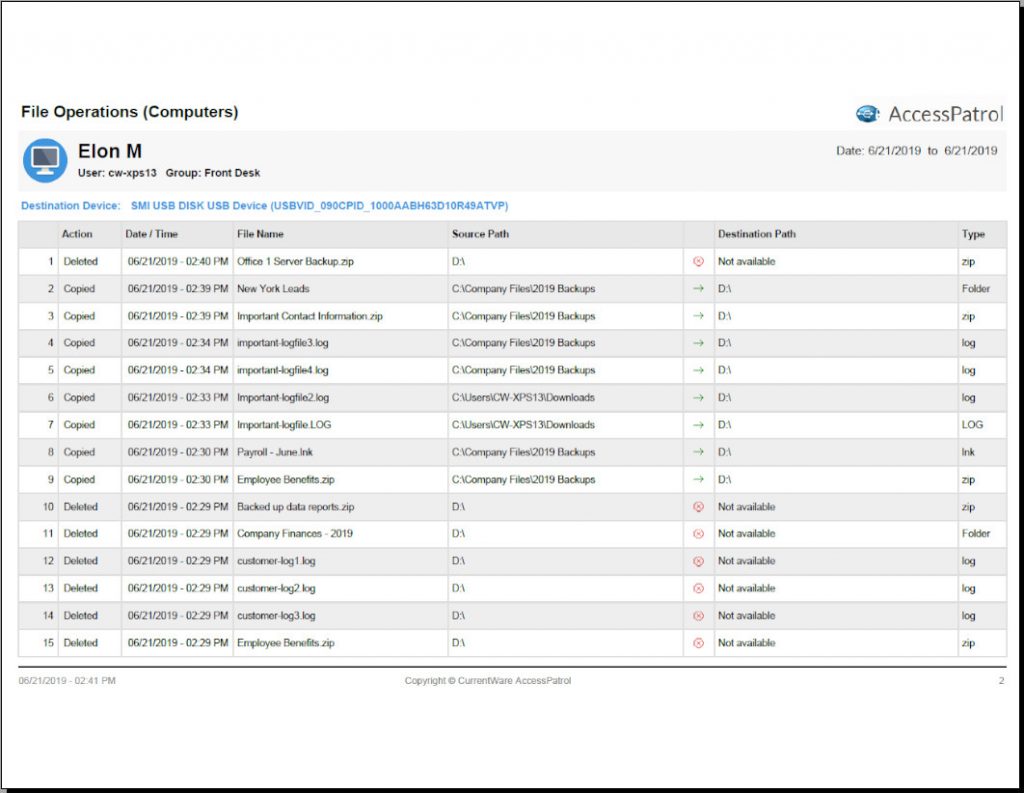
Employee monitoring software is an affordable solution for managing the risk of insider threats. By using software to monitor computer activity on your network you can detect unsafe internet usage and suspicious employee behavior.
- File Operations: Data loss prevention software can monitor for suspicious file operations such as attempts to copy data to external storage devices.
- Unsafe Websites: When employees browse the internet for personal usage they may stumble upon websites that contain malware. Computer monitoring provides an opportunity to address unsafe web browsing behaviors.
- USB Device History: If personal USB devices are banned in the workplace, a notable history of personal USB device usage may indicate attempts to exfiltrate company data.
How to Monitor Employees While Respecting Their Privacy
Employee monitoring software can be perceived as invasive. Follow these expert tips from CurrentWare’s managing director Neel Lukka to monitor your employees in a way that is transparent and respectful of their privacy expectations.
Data Minimization
Data minimization (data minimalism) is the process of ensuring that only the exact data needed for legitimate business use is collected and stored. In the era of ‘big data’ it is often tempting for businesses to capture and store as much data as possible in an effort to gain the greatest amount of insights. Unfortunately, hoarding greater amounts of data than is truly necessary opens up your business to a higher degree of risk that the data will be leaked.
Best Steps for Minimizing Data:
- Periodically review the data that is held and delete anything that is no longer needed.
- Only collect the amount of information that is needed and only collect it when it is needed.
- To avoid duplication, carefully organize sensitive data into a centralized repository and ensure that employees do not save local copies to their own devices.
Patch Automation
According to “Market Snapshot Report: Secure Operations Automation.” by Voke, 80 percent of data breaches were caused by poor patch management and configuration updates. Every piece of software (and even hardware such as routers) will provide periodic security updates that are designed to patch known vulnerabilities. To reduce the resources required to maintain regular patching, minimize the amount of software that is used in your organization and enable automatic updates.
Block Unused Network Ports
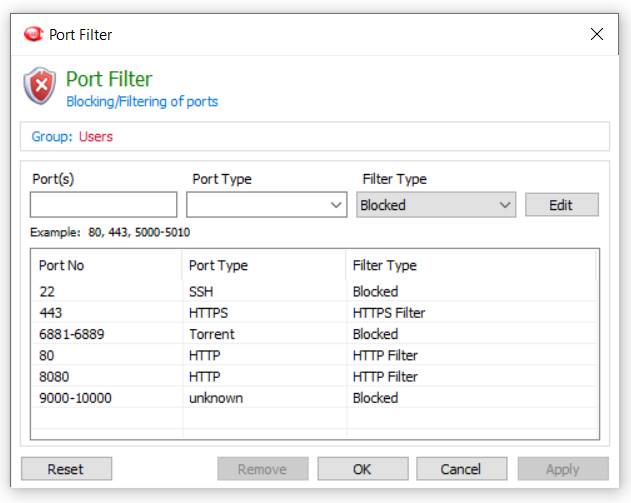
The internet relies on the use of network ports to send different kinds of data. If you leave all of your network ports open by default you provide threat actors with greater options for accessing your network.
The best practice is to only leave open the specific ports that are needed by your business and use a port filter to close any unused ports. This particular tip can be difficult to follow if you are strapped for time, but it will help improve the security of your network.
Many businesses forgo this step because special applications may stop working if a port they need is blocked, forcing whoever has opted to take on IT management to research the port the app is requesting and unblocking it.
How to discover which ports need to be left open:
- Product Documentation: Consult the manuals of any software and hardware used in your organization and see if they require specific ports to be left open.
- Netstat & Resource Monitor: Use a netstat command and Windows resource monitor to identify ports that are currently in use by a specific computer.
- Network Analytics: Various types of network monitoring tools will include features for reporting on network port activity, including which ports are used by the organization.
- Trial & Error: If you only use internet-connected computers and have no other special needs, try blocking all ports except for port 80 (HTTP internet) and port 443 (HTTPS internet). Test all services and applications in your organization to see if there are any connection issues and monitor IT support tickets for any unforeseen issues.
- Research Ports: If you need to perform special actions such as file transfers over FTP or hosting your own email servers you’ll need to consult this list to see the ports that are required by each of them.
If you will be using CurrentWare products, visit this article to see the ports you will need to keep open.
Encrypt Sensitive Data
Data encryption is a critical security control for preventing breached files and stolen harddrives from being usable by hackers unless they have the decryption key or a significant amount of computing resources to brute-force the decryption process.
If you are running business-ready versions of Windows 10+, you can use Bitlocker to encrypt virtual storage volumes, USB storage devices, and even entire hard drives. You can also encrypt specific folders using the Encrypted File System (EFS) that comes with Windows.
Improve The Security of USB Flash Drives

USB devices that are commonly used in the workplace can be incredibly dangerous. To protect against these devices, consider implementing a data loss prevention solution such as AccessPatrol to enforce the exclusive use of authorized USB devices.
The Dangers of USB Devices:
- External storage devices (including cell phones) can unknowingly transmit malware to an otherwise secure system.
- Sensitive data can be transferred to USB devices that are later lost, stolen, or sold.
- Specifically engineered ‘payloads’ can be created to give attackers control over the machines that the USB device is connected to.
- Seemingly innocent USB devices such as fans and lights can be engineered to transmit data.
Limit Access to Admin Accounts
While it may be convenient to provide employees with the ability to install their own software and make adjustments to their computers as needed, administrator credentials provide user accounts with far too much control over devices to be considered safe. Accounts with admin rights can potentially overwrite file access permissions, creating a potential data security incident by making restricted data more accessible.
By limiting the amount of admin accounts you can also reduce the amount of resources required to monitor these accounts for suspicious activity and reduce the amount of accounts that can be potentially compromised.
Install Anti-virus & Anti-malware Software
Anti-virus and anti-malware software are essential for protecting company endpoints against exploits from malicious software. While some free programs are available, many of these prohibit use in a commercial setting in their end-user license agreement (EULA).
These free alternatives may also lack the full functionality of their paid counterparts or not be as up-to-date on the latest threats, making them a less-than-optimal solution for data loss prevention and network security. Paid anti-virus and anti-malware programs will also often include a centralized management platform that allows all of the computers in the network to be managed from a single workstation rather than checking each computer manually.
It’s important to note that while there are similarities between anti-virus and anti-malware programs, they are not exactly the same.
- Anti-virus: Prevention-based, protects networks by proactively stopping endpoint devices from becoming infected.
- Anti-malware: Treatment-based, protects networks by detecting and destroying malicious programs that have infiltrated the network.
Pay Attention to Physical Security

Data loss prevention is not exclusive to managing digital threats. When computers, laptops, and USB devices are lost or stolen, any unencrypted or unredacted data that resides on them must be considered breached.
How to Improve Physical Security:
- Traveling: If employees will be using mobile devices to work while traveling, ensure that any sensitive data they have access to is encrypted and that they have their devices on them at all times. They should also be mindful of anyone within their line of sight that could be watching their screens.
- In-Office: Implement a system for gatekeeping company resources from the general public. This can include deadbolts, keyless entry systems, and alarm systems. Consider training employees on appropriate procedures for identifying and managing unwanted visitors and installing a security camera system to deter theft of company equipment.
The Best Cyber Security Resources For Small Businesses
Managed Services Providers (MSP)
Managed services providers (MSP) and Managed security services providers (MSSPs) make advanced cyber security and data loss prevention accessible to companies that do not have the resources to hire and train their own on-site IT support staff.
An MSP will typically sell their services on a subscription model with costs being priced per user or device. Some MSPs will also offer flat-fee pricing to handle the support of all their customer’s IT infrastructure.
The Benefits of an MSP for Small Businesses:
- Cost Savings: When you work with an MSP to outsource your IT needs you save on the costs of onboarding and maintaining dedicated staff, purchasing specialized software, troubleshooting IT issues, and the time spent managing your security.
- Convenience: MSPs will take care of proactive IT support and maintenance, letting you focus your energy on developing your businesses.
- Planning: An experienced MSP can serve as a valuable resource for determining what changes will need to be made to the business’s IT infrastructure as it grows.
Businesses that need to manage their cyber security on a budget may be weary about the monthly expenses that come with an MSP. When deciding whether contracting an MSP is the right investment for your business it’s important to factor in the costs of a data breach, lost productivity due to equipment failures, and the time it takes to manage your own IT infrastructure.
Web Filtering Software For Small Business
BrowseControl is easy-to-use and affordable, making it the best internet filter for small-to-medium businesses that want to protect their network and manage employee productivity on a budget.
Why BrowseControl is the Best Internet Filter for Small Businesses:
- Customer Support: Your time is valuable – we’ll guide you through the installation of our easy-to-use software solution so you can start using CurrentWare right away. Each subscription comes with ongoing product upgrades, installation assistance, and on-demand technical support.
- Volume Licensing: Volume-based licensing provides advantageous pricing for organizations that need to manage large quantities of devices. Volume license discounts are available starting for as low as 100 users, with discounts increasing depending on the number of licenses.
- Advantageous Pricing: CurrentWare’s solutions can be purchased individually for the greatest flexibility or as a bundle for the best value. There are additional discounts available for educational organizations, non-profits, managed services providers, and for businesses that pre-purchase multiple year plans. Looking for a quote? Contact our sales team here.
Employee Monitoring Software For Small Businesses
BrowseReporter is CurrentWare’s computer monitoring software for tracking how employees use technology in the workplace. Track time spent on unproductive websites and applications to identify employees that are actively disengaged from their duties or engaging in harmful internet usage.
Why BrowseReporter is the Best Employee Monitoring Software for Small Businesses:
- Internet Usage Monitor: Application and internet usage monitoring to maintain logs of computer activity and alert administrators to undesirable web activities.
- Screen Monitoring: View the screens of employees in real-time and remotely capture their contents.
- Auditable Monitoring Records: Maintain perpetual records of applications used, websites visited, bandwidth consumed, and keywords input into search engines.
- Track Applications: BrowseReporter reports on employee software usage so you an see the applications they use each day.
Data Loss Prevention Software For Small Businesses
AccessPatrol allows small business owners to easily manage the risks of USB devices in the workplace by enforcing the exclusive use of encrypted USB devices, blocking unauthorized USB devices, and monitoring file transfers.
Why AccessPatrol is the Best DLP Software for Small Businesses:
- Custom Device Permissions: Assign read-only, no access, and full access for USB devices based on user, device, or organizational unit.
- USB Blocker: Prevent employees from using unauthorized devices that can be used to transmit ransomware and illicitly exfiltrate data.
- File Transfer Visibility: Alert administrators to suspicious file activity and maintain an auditable log of files that have been copied, created, and deleted on USB devices.
Free Cyber Security Resources For Small Businesses
To further help guide your small business cyber security strategy, these free resources provide actionable insights to improve the security of your network and data.
| Resource | Description |
| The CurrentWare Blog | We regularly post insights into cyber security, employee monitoring, technology, and remote workforce management on our blog. Sign up for our monthly newsletter to stay up-to-date! |
| Cybersecurity & Infrastructure Security Agency (CISA) | This is an official website of the US Department of Homeland Security. They provide in-depth resources that help organizations of all sizes combat cybercrime. |
| Common Vulnerabilities and Exposures (CVE) | The CVE list is used by the global cyber security community to track publicly known cyber security vulnerabilities. With the CVE you can see if your vulnerability scanners are checking for recently uncovered threats. |
| National Cyber Awareness System Alerts | Similar to the CVE list, this is a list of alerts published by the US government. These alerts provide security recommendations to help fight recently discovered threats. |
| Federal Communications Commission – Small Business cyber security Resources | The FCC maintains a page on their websites with dozens of links to valuable cyber security resources to help empower small businesses. |
| ESET cyber security Awareness Training | Many companies such as ESET offer free and paid cyber security training courses to help keep your employees working safely. |
| Center for Internet Security (CIS) – The 20 CIS Controls & Resources | This detailed resource collection from CIS offers informational videos, PDFs, and spreadsheets detailing the controls you can implement to protect sensitive data. |
| Tech Support Guy | This open forum allows small business owners to post their tech support questions. The community is frequented by IT support professionals that are eager to help. |
Conclusion
Managing data loss prevention on a budget is no small task. Proactive cyber security often requires specialized knowledge and consistent upkeep to pull off effectively. With the resources and best practices shown in this article your small-to-medium business can better protect itself against hackers, insider threats, and breaches of sensitive business data.
FREE GUIDE & CHECKLIST
How to Keep Data Safe When Offboarding Employees
The employee offboarding process presents significant data security risks. Employees have intimate access to corporate data, insider knowledge of the organization’s systems, and a level of trust that can allow them to steal data undetected.
Click the button below to learn the best practices for managing insider threat risks during offboarding & gain access to a checklist of key cybersecurity items you must include in your offboarding process.



