Trusted by
& many more
Trusted by
& many more
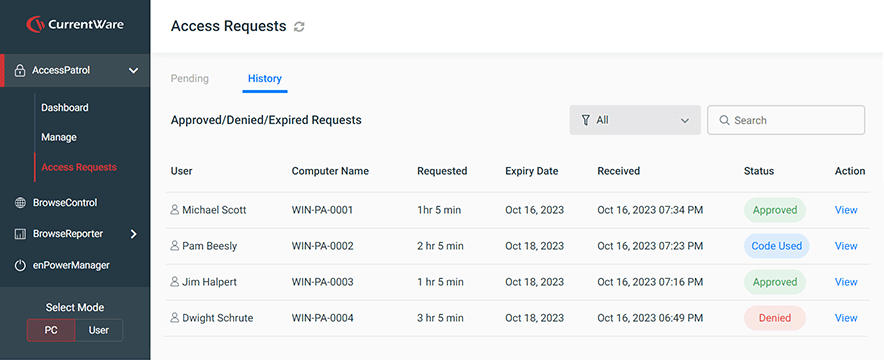
Manage Access Requests in the Web Console
- End-users submit access code generation requests and activates access codes from the CurrentWare client in their system tray
- End-users are prompted to provide their email address, the reason for their policy exemption request, and the desired date/duration for the exemption
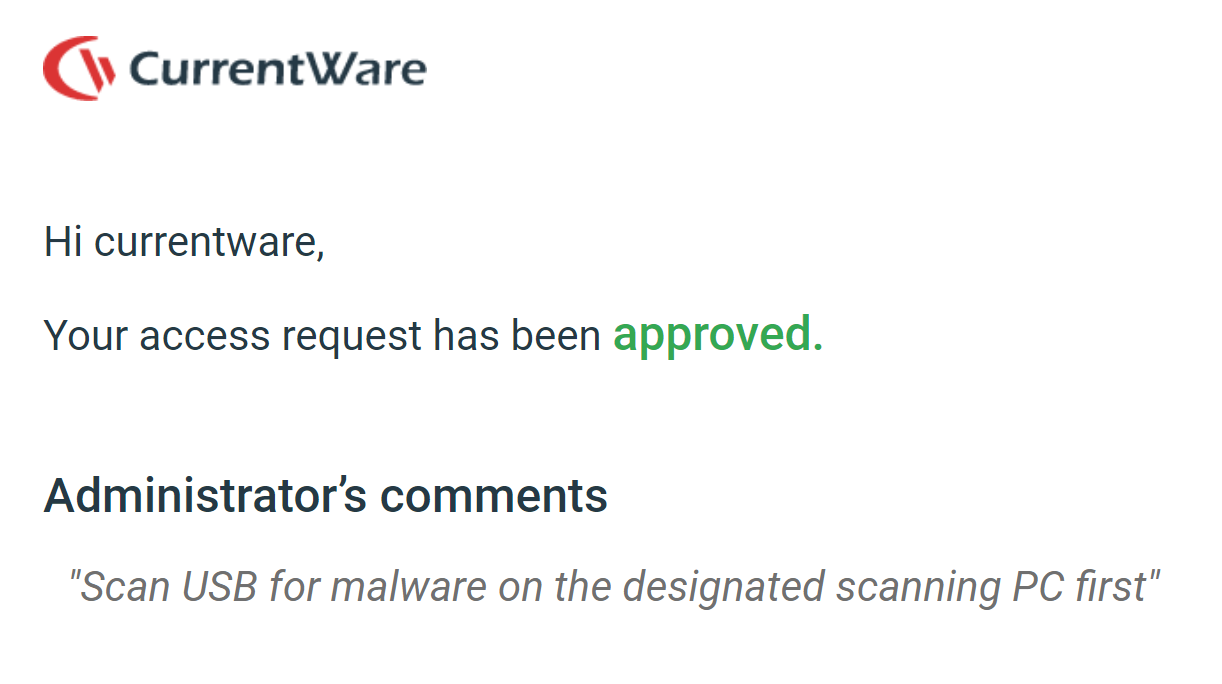
- Admins respond to requests in the web console where they can adjust the duration of the access code, accept/deny requests, provide a reason for their response, automatically retain a log of all access requests, and track which access codes have been activated
- Admins and users receive alerts and updates related to access codes in their email inbox
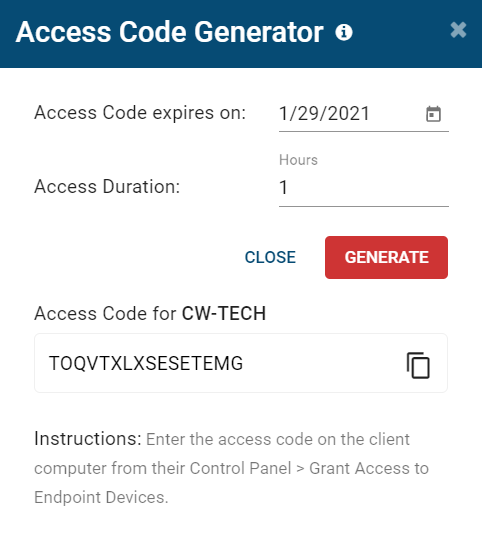
About Access Codes
- Access codes work on remote computers, even without an internet connection
- Balance security and productivity by providing exemptions to your USB security policies for edge-cases such as trusted vendors, special guests, and other third-parties
- Access codes are single-use, unique to a specific computer, and automatically expire to prevent misuse
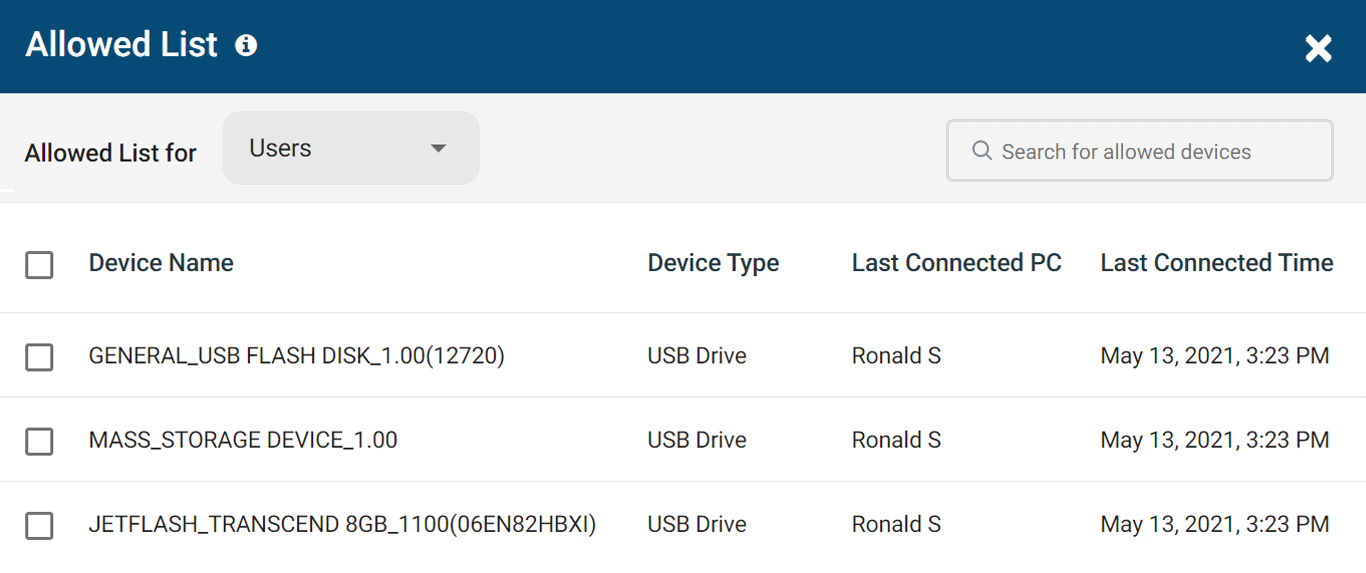
Allow Trusted Devices for Extended Use
Need a more permanent solution? Grant continuous access to authorized USB devices by adding them to the Allowed List.
Combine this feature with the USB Device Blocking and File Transfer Restriction features for full USB control.
- Allow authorized devices to be used on specific computers or by specific users
- Remove support bottlenecks by providing super users with access to trusted removable media
- Control the flow of sensitive data by limiting device use and monitoring USB file transfers
AccessPatrol’s USB Control & Data Loss Prevention Features
Block USB & Other Devices
Set full access, read only or no access on storage devices
Whitelist USB Devices
Allow only authorized storage devices to be used
Block File Transfers
Prevent files from being transferred to portable storage
Access Code Generator
Provide temporary access to peripheral devices
DLP Activity Reports
Track file transfers, storage device use, file operations, and more
File Transfer Monitoring
Monitor files that are copied to USBs, cloud storage, and more
Alerts & Reports
Automatically send USB activity reports to designated inboxes
Transparent & Stealth Modes
Run silently in the background or provide notice of monitoring
Central Web Console
Save time with a central admin console; optionally integrate Active
Directory OUs or security groups
Platform Security
Protect your CurrentWare console
with 2FA, passwords, privilege
management, and more
Offsite Management
Extend onsite security policies to computers running outside the corporate network
SQL Server Supported
Database scaled for enterprise and
large business operations using
Microsoft SQL Server