Trusted by




& many more
Trusted by



& many more
Port Filter to Block Unused Ports
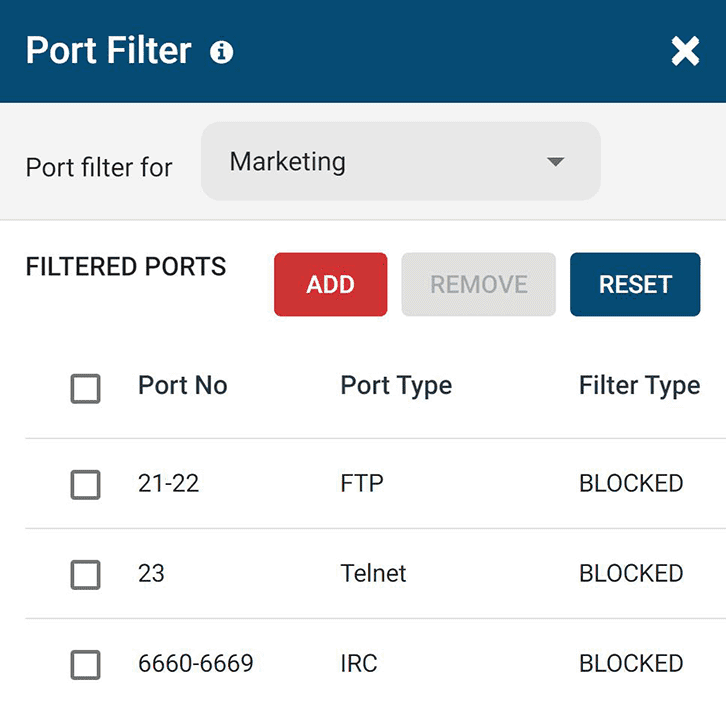
BrowseControl’s port filtering feature allows you to block port numbers based on a variety of well-known ports, specific port numbers, or a port range.
- Deny by Default: All ports should be closed by default unless there is a documented, reviewed, and approved business case.
- Defense in Depth: Combine BrowseControl’s host-based port filtering with a perimeter-based firewall for a defense-in-depth approach.
- Risk Assessment: Any port can be exploited by an attacker. Blocking unused ports reduces the attack surface of your network.
Why Block Ports?
Malicious hackers can use port scanning tools to discover open ports in your network.
Once they find an available port number they can use it to search for potential vulnerabilities that they can use to gain unauthorized access into your network.
By proactively blocking unused ports with port blocking software you can reduce the attack surface available to threat actors and improve network security by making the filtered port inaccessible.
What is Port Filtering?
Port filtering is the practice of filtering packets based on port number to restrict traffic within a network.
The internet and applications use Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) ports to transmit network protocol packets (data).
In a TCP/IP network, a port is a number that identifies the type of network traffic. If an incoming or outgoing port is “closed,” packets with that port number are not allowed into or out of the LAN. With BrowseControl’s port filter these packets are restricted on a per-endpoint basis.
Ports 1024 to 49151 are Registered Ports. Ports 49152 to 65535 are Public Ports.
Using a port filter allows administrators to restrict specific operations such as file transfers through FTP and torrents. With the filtered port inaccessible you can reduce the attack surface of your network.
Recommended Ports to Block
While any port number can be potentially exploited, there are some ports that are known security risks.
For example, port 20 and 21 are used by the File Transfer Protocol (FTP). Generally, port 21 is used to establish the connection between the 2 computers (or hosts) and port 20 is used to transfer data (via the Data channel).
If a Deny-by-Default approach isn’t feasible for your organization, try these recommended ports to block in your port filter.
- Internet Relay Chat (IRC): Botnets can use IRC to communicate with infected machines. Close the port range 6660 – 6669 to block IRC.
- Telnet: Telnet is not a secure protocol and is unencrypted. Block port 23 to restrict access to it
- Memorable Numbers: Some malware authors use easy-to-remember numbers such as 234, 6789, 1111, 666, and 8888
- File Transfer Protocol (FTP): FTP is used to transfer computer files from a server to a client on a computer network. Block port 21 to restrict this data egress point on client computers.
What Ports Need to Be Left Open?
Port requirements are unique to each organization and its networks; which ones are considered important ports will vary widely based on the software/services used and network setup.
The specific ports required by business applications will evolve over time as well. Here are some ways to determine which ones you need to keep open.
- Product Documentation: Consult the manuals of any software and hardware used in your organization and see if they require particular TCP/UDP ports to be left open.
- Netstat & Resource Monitor: Use a netstat command and Windows resource monitor to identify ports that are currently in use by a specific computer.
- Trial & Error: If you only use internet-connected computers and have no other special needs, try blocking all ports except for port 80 (HTTP) and port 443 (HTTPS). Test all services and applications in your organization to see if there are any connection issues and monitor IT support tickets for any unforeseen issues.
- Research Ports: If you need to perform special actions such as file transfers over FTP or hosting your own email servers you’ll need to consult this list to see the ports that are required by each of them.
BrowseControl Web Filtering Features
Category Filtering
Block websites based on specific web content categories
URL Filter
Allowed list or Blocked list for
specific URLs
Application Blacklisting
Block specific Windows
applications from launching
Block Downloads/Uploads
Prevent uploading and downloading based on file type
Port Filter
Close unused and high-risk
TCP/UDP ports
Customize Message
Display a customized warning
message on blocked websites
Google Safe Search
Search engine filters prevent explicit results in search engines
Time-Based Policies
Schedule internet access and control browsing based on time
Central Web Console
Save time with a central admin console; optionally integrate Active
Directory OUs or security groups
Platform Security
Protect your CurrentWare console
with 2FA, passwords, privilege
management, and more
Offsite Management
Extend onsite security policies to computers running outside the corporate network
SQL Server Supported
Database scaled for enterprise and
large business operations using
Microsoft SQL Server