Trusted by
& many more
Trusted by
& many more
How to Monitor Employee Internet Use
BrowseReporter is a powerful employee internet usage monitoring software to monitor internet activity in the workplace.
Our employee monitoring software gives you detailed evidence of web activity in your company, making it the perfect complement to existing internet use policies.
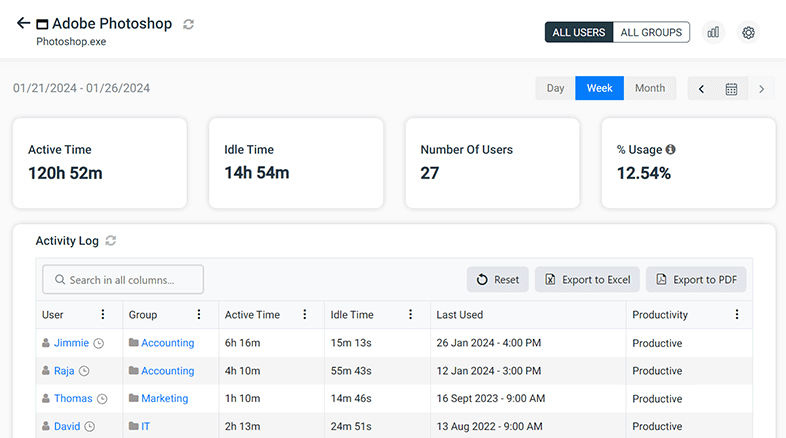
BrowseReporter’s detailed employee internet usage reports provide managers with the activity data they need to understand how in-house and remote teams are spending their time at work.
The Benefits of Employee Internet Monitoring Software
Enforce Computer Use Policies
An employee computer use policy helps ensure that your team members are aware of their responsibilities, but it’s not enough.
To make your policies truly effective you need visibility into which employees are visiting high-risk, inappropriate, or unproductive websites.
Find Bandwidth Hogs On Your Network
Are bandwidth upgrades necessary, or is an employee’s misuse of the internet what’s causing bottlenecks?
With CurrentWare's bandwidth monitoring features you can identify bandwidth hogs in your network, then block them to reduce unnecessary strain on your network’s bandwidth.
Manage Employee Productivity
While occasional web surfing might be okay so long as employees are getting their work done, workplace internet abuse can be a serious detriment to employee productivity.
The productivity insights provided by employee computer monitoring software allows you to identify inefficiencies so you can optimize work processes.
Protect Your Business From Liability Risks
Detect Software Piracy
Ensure only legitimately licensed software is being used on company computers.
Stop Workplace Harassment
Collect evidence of employees accessing pornographic, hateful, or crude websites at work.
Improve Visibility of Remote Workers
Identify poor performers, improve visibility into employee productivity, and provide high-performers an opportunity to demonstrate their efforts.
Using BrowseReporter’s productivity by location reports you can analyze employee productivity trends to see where they thrive and verify attendance.
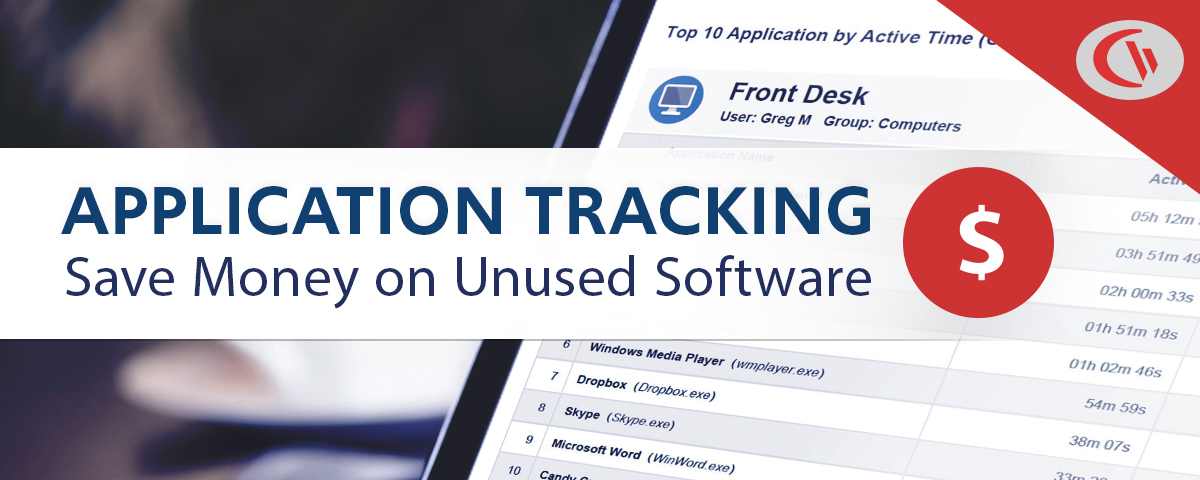
Save Money on Unused Software
36% of desktop software & 29% of SaaS spend is underutilized or wasted!
Track SaaS and desktop software usage to uncover insights into what applications can be decommissioned, consolidated, or reduced
The reports are very easy to understand and the fact that they can be emailed to you on a schedule is amazing, and have made finding productivity killers VERY easy. Customer support has been fantastic every time I've had to reach out to them; I highly recommend them!
Kristen S, Associate IT Director
The Coding Network, 700+ Employees
In my nearly 40 years in the IT business I’ve worked with a lot of support teams. I really appreciate CurrentWare going the extra mile to help me get the most out of the product. They’ve definitely outweighed any of the other competitors that I’ve looked at.
J.S, Managed Services Provider
Vehicle Dealership, 150-200 Employees
BrowseReporter is an extremely useful piece of software for monitoring our employees' devices while they are at work. It enables us to view data in real time, conduct detailed analyses of each employee's activities, and improve productivity where necessary.
Sebastian P, CMO & Customer Experience Officer
Retail Industry, 10,001+ Employees
BrowseReporter is simple to use and provides our company with the information we were looking for. Having BrowseReporter installed has prevented any internet abuse. This was exactly what we wanted!
Denise P, IT Manager
Paper & Forest Products, 51-200 Employees
Expand your capabilities with CurrentWare’s award-winning productivity and security software






Flexible Deployment Options
With CurrentWare’s cybersecurity, web filtering, data loss prevention, and user activity monitoring solutions you’re in complete control of how your data is stored, secured, and retained. Your employees' data cannot be accessed by CurrentWare.
On Premises
Keep Control of Your Data
Install the management software on a standard computer, then deploy the client software to your users' computers
Remote Workers
Monitor & Manage on Any Network
Connect your remote employees’ computers to the management software with simple port forwarding rules
Self-Managed Cloud & VDI
Citrix, Azure, AWS, GCP, and More!
Enjoy the scalability and availability of the cloud alongside the security, control, and flexibility of our on-premises solution
Go Beyond Employee Internet Use Monitoring
With the full capabilities of the CurrentWare Suite you can go beyond monitoring internet activity with advanced visibility and control over internet, application, and removable media usage. Get granular insights into file uploads/downloads, file transfers to removable media, logon/logoff times, and more!
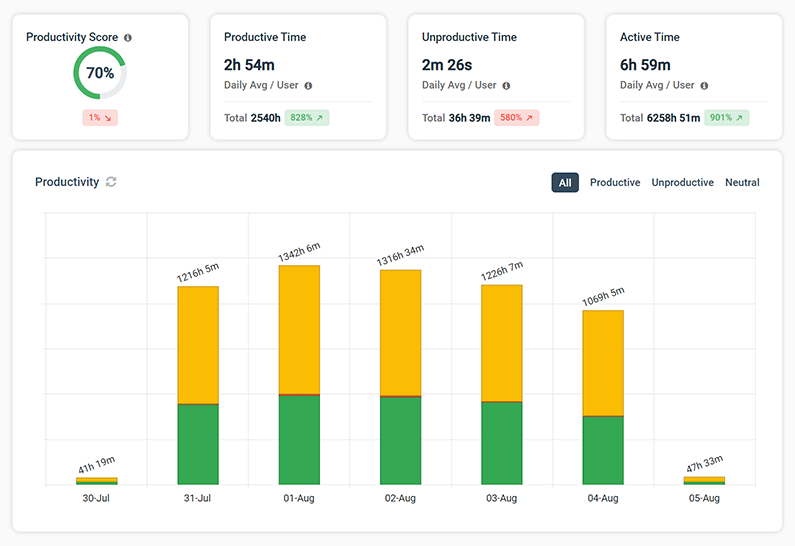
Monitor Employee Productivity
CurrentWare’s detailed employee productivity reports provide managers with the productivity metrics they need to better understand how employees spend their time at work.
- Track the use of apps and websites to find out who is wasting work time on social media, computer games, and other distractions
- Track employee engagement across your entire workforce, a specific team, and individual employees
- Review the websites that were open during inactive periods to verify that idle time was spent on work-related tasks
- Get insights into productivity trends based on time spent in-office vs working remotely
Keep a Pulse on
Real-Time Team Activity
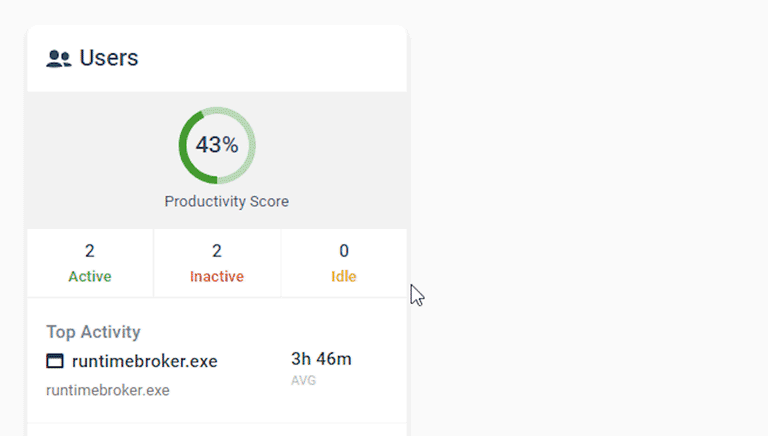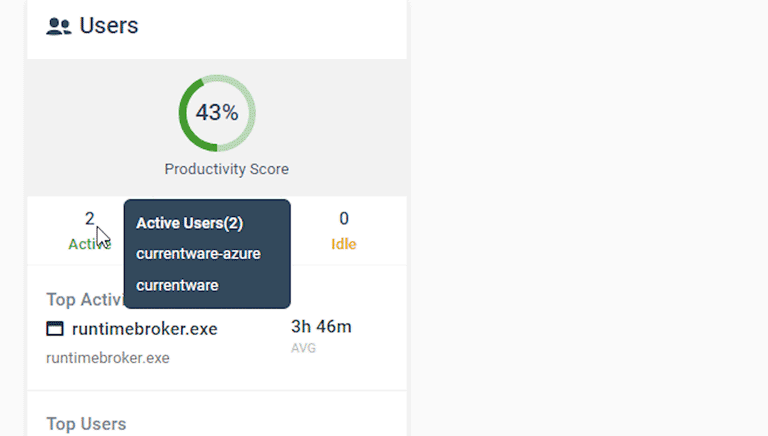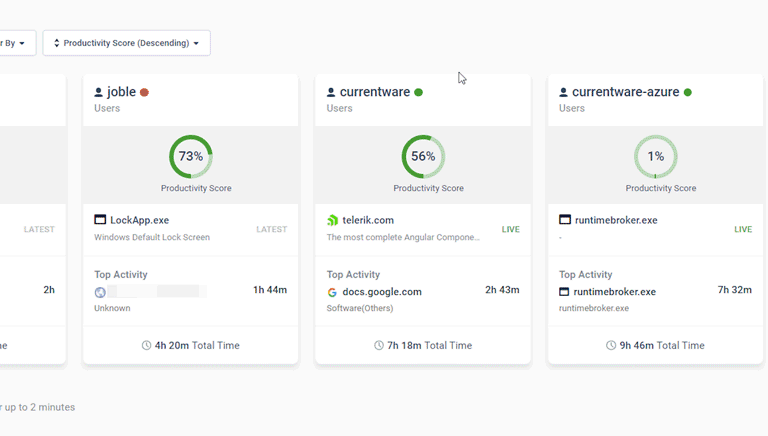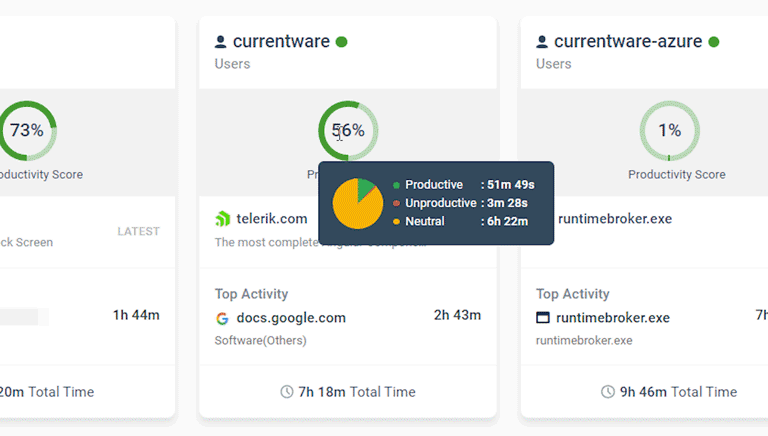
Today’s Insights displays the real-time productivity and availability status of individuals and teams via an at-a-glance dashboard.
Easily view the most recent productivity metrics to understand who is actively working and what application/website they last used.
- Get high-level views of the activity of individual users and teams
- Easily see who is online now and who hasn’t logged in today
- Filter cards by activity, productivity, name, and average activity time
Protect Company Data From Insider Threats
CurrentWare’s user activity monitoring and data loss prevention features give you the activity logs you need to protect against a data breach to insider threats.
- Prevent data breaches with proactive alerts of high-risk activities like using unauthorized portable storage devices
- Audit employee activity for suspicious activity and anomalous behaviors
- Track and restrict file movements across portable storage devices, cloud storage services, and network share drives
Take Screenshots
of Employees’ Screens
Our employee monitoring software lets you capture screenshots of your employees’ screens to see exactly what they are doing on their computers.
- Capture high-resolution and compressed screenshots
- Monitor desktops in real-time to watch for unsafe data handling and inappropriate behavior
- Screenshots are tagged with the website or application that was being used, the time, and the name of the computer
Save Money With Genuine Software Usage Data
Underutilized software costs businesses a staggering $34 billion per year! With genuine insights into employee application usage you can make informed software asset management decisions.
- Find the utilization rate of specific pieces of software
- Discover what SaaS tools have fallen out of use
- Ensure you have enough licenses to meet genuine demand
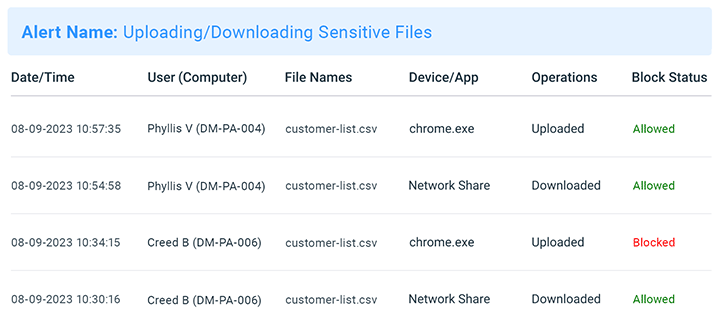
Monitor File Transfers for Suspicious & High-risk Behaviour
Improve data security with increased visibility into high-risk data transfers and USB activity.
- Receive real time email alerts when employees violate your endpoint security policies
- USB file tracing reports show files that have been copied, created, deleted, or renamed on removable media devices, cloud storage services, and network share drives
- Review file transfer activity logs to trace data breaches back to their source
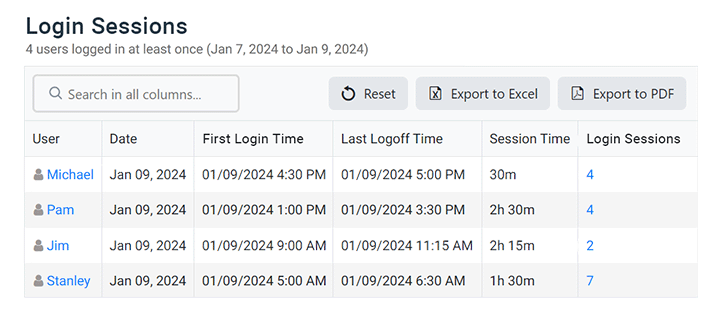
Track Login & Logout Times
Combine idle time tracking with logon history reports to get a full picture of your employee’s activity levels.
- Audit logon and logoff times to see how long your employee’s are working at their computers
- Get a record of each time your employees startup, restart, and shutdown their computers
- Verify that employees working from home are active during work hours and see when they are taking breaks
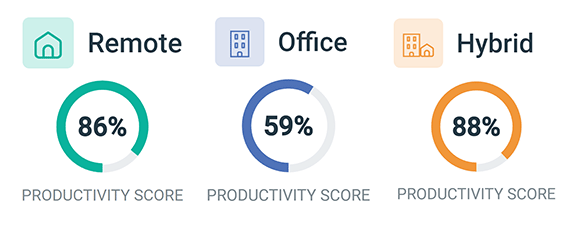
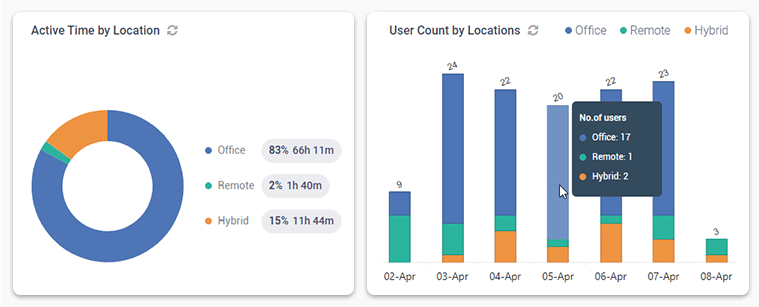
Get Insights Based on Employee Location
BrowseReporter’s Location Insights dashboard helps leaders make data-driven decisions about remote, in-office, and hybrid work.
Promote flexibility without sacrificing accountability with insights into how location flexibility affects employee performance and engagement.
- Compare productivity scores between groups of in-office, remote, and hybrid employees to gauge the impact that location has on employee performance
- See how much of your workforce is working in-office, remotely, or hybrid in a given timeframe
- Review productivity trends to decide if frequently abused distractions need to be limited with BrowseControl’s URL filter
CASE STUDY
Shady Maple Transforms Their Productivity With Internet Filtering and Monitoring Software
Being able to identify negative browsing trends and put a stop to them within a couple of hours has meant that our employees are focused on the job almost all of the time. We have become an extremely efficient workforce.
How to Address Objections to Internet Monitoring Software?
The world of employee monitoring is a bit of a double-edged sword. As an employer you want to use software to monitor internet activity to gain critical insights and prevent time theft by ensuring employees work as expected, but your high-performing employees might feel like they aren’t trusted to handle their task management independently.
The key to a successful employee monitoring strategy is to foster employee buy-in. Your employees need to know that their privacy is respected, that they are trusted, and that productivity tracking software isn’t the sole method for evaluating employee performance.
Be Transparent About Employee Activity Monitoring
Employees that are not aware that they are being monitored, why they are being monitored, and how they are being monitored are less likely to find the use of employee computer monitoring software acceptable.
CurrentWare’s employee and computer monitoring software solutions can be deployed with an optional stealth mode or configured to periodically notify employees that they are being monitored.
- Turn on BrowseReporter’s End Users Reports feature to give employees access to their data. This gives them the autonomy to monitor their own productivity.
- Disclose the scope of employee monitoring during onboarding and within company policies.
- Make sure employees understand how data is being collected, what data is being collected, and how it will be used.
Ensure Confidentiality & Privacy for the Employees Involved
While complete confidentiality cannot be guaranteed for all employees involved, the workplace investigation process must be conducted with as much confidentiality as possible for the parties involved.
Any monitoring or data collection should be conducted in compliance with applicable laws and regulations, as well as in accordance with the employer’s policies and procedures.
Additionally, it is essential to maintain the confidentiality of sensitive information and respect the privacy rights of employees during the investigation.
Consult With Legal Counsel
When it comes to workplace privacy, both the employee and the employer have rights that vary based on the jurisdiction of the company, as well as any relevant collective bargaining agreements.
Before monitoring employee computer activity for workplace investigations, be certain to consult with legal counsel to understand what employment laws apply to your organization and what steps you must take to monitor employees lawfully.
At a minimum your legal team will recommend a Workplace Monitoring Policy that outlines what data is collected and how it will be used.
How to Increase Buy-in for Employee Monitoring
- Consult your employees. Involve a representative sample of employees to ensure that their voices are heard. Allow them to voice any concerns they have regarding your use of employee computer monitoring software.
- Do not track more than necessary. Only collect, store, and use the types of data that are adequate and relevant for the stated purposes. Overly invasive monitoring methods such as capturing individual keystrokes and webcam feeds are highly likely to infringe on employee privacy rights unless there is a legitimate business need that cannot be adequately met through less invasive methods.
- Limit access to employee monitoring data. Restricting access to monitoring data to a “need to know” basis limits opportunities for misuse. Use CurrentWare’s operator permissions to password protect the console and limit who has access to certain features.
Protect Employee Monitoring Data From Misuse
Employee monitoring data can be sensitive. Organizations need to ensure that administrative and technical security measures are in place to prevent data from being misused or leaked to unauthorized parties.
- Password-protect employee data. The CurrentWare Console can be password protected to limit who has access to employee computer activity data.
- Limit data access. With CurrentWare's Operator Accounts you can provide a manager with access to their department's data without providing them with the data of other departments. You can also use the email reports feature to automatically send data about specific users/PCs on a regular basis.
- Only use employee computer activity data for its intended purpose. If employees consent to their data being collected for the purpose of enforcing acceptable use policies it is critical that it is not reappropriated for another purpose without their explicit and informed consent.
Only Monitor What is Needed
Employee monitoring is unique for every organization, and yours is no exception.
When you monitor your employees the best practice is to only monitor what is needed to meet your organization’s goals.
Rather than monitoring every single action your employees take without a clear reason to do so, you should map your clearly defined goals to the data points you need to collect in order to meet them.
This ensures that the monitoring methods used are as minimally invasive as is needed to meet your goals. You’ll also improve buy-in by clearly demonstrating the intended purpose of the monitoring.
Get Informed Consent From Monitored Employees
When implementing an employee monitoring solution, it is best practice to get explicit and informed consent from your employees that they are going to be monitored.
Even if there are no laws that specifically require that you disclose to employees that they are being monitored, it is the best practice to do so anyway.
What constitutes informed consent and lawful data collection varies by jurisdiction. As always, consult with legal counsel prior to monitoring employees to ensure you are compliant with data privacy and security requirements.
Combine the Insights With Other Workplace Investigation Techniques
Workplace investigations require thorough documentation and evidence before a final decision is made and corrective action is implemented.
While workplace investigation software is critical to the investigation process it is most effective when combined with traditional investigative techniques.
- Gather Other Evidence: Combine computer activity data with any information you already have, such as an employee complaint, a supervisor’s report, written statements from witnesses, or written warnings.
- Conduct Interviews: Interview witnesses, the involved parties, and other employees that may have insights into the alleged conduct. Gather all relevant information in thorough notes.
Employee Monitoring Resources
Employee Monitoring Best Practices [White Paper]
Ready to get started? Download this FREE white paper to learn the best practices for monitoring your employees
How to Monitor Employee Computer Activity (& Why You Should)
Learn how—and why—to monitor employee computer use with CurrentWare’s employee monitoring software solutions
Download a Free Workplace Monitoring Policy Template
Download this FREE electronic monitoring template and customize it to fit the needs of your organization.
What is Employee Monitoring?—A Comprehensive Guide
Learn about methods for monitoring employees in the workplace, the pros and cons of employee monitoring, and more
How to Get Buy-In for Employee Tracking Software
Learn how to evaluate monitoring software vendors and get buy-in for employee monitoring from all levels of your organization.
How Monitoring Software Improves Business Performance
Learn how computer monitoring software can help you make data-informed workforce management decisions.
Real-Time Employee and Computer Monitoring Features
Monitor Computer Activity
Get real-time insights into your users' technology use
Screenshot Monitoring
Take automatic screenshots or remotely view desktops
Track App Use
Get insights into software usage trends in your organization
Idle Time Tracking
Track mouse and keyboard movement to monitor inactivity
Email Reports & Alerts
Automatically send reports to designated inboxes based on events or schedules
Tracking Scheduler
Limit activity tracking to specific days and schedules such as employee work hours
Employee Privacy
Optional privacy-enhancing features improve transparency and minimize data collection
Stealth Mode Option
The software can run silently in the background or be configured to alert users
Central Web Console
Save time with a central admin console; optionally integrate Active
Directory OUs or security groups
Platform Security
Protect your CurrentWare console
with 2FA, passwords, privilege
management, and more
Software License Optimization
Optimise your organisation’s software spending with insights about associated costs and usage.
SQL Server Supported
Use the included Microsoft SQL Express database or connect your own SQL server
The Benefits of the Best Employee Monitoring Software
Why is computer monitoring software so popular? This video shows the key reasons why employers use computer monitoring software to track activity on employee computers.
How to Choose the Best Employee Monitoring Software
Deciding on what the best employee monitoring software is for an organization can be a daunting process as individual requirements will change depending on the organization’s current infrastructure, the types of monitoring they would like to conduct, their data privacy and security compliance requirements, as well as several other factors.
This employee monitoring software buyer’s guide covers the essential considerations your organization must evaluate when determining the best employee monitoring software for its needs.
Define Your Goals
In order to get the most value out of employee monitoring tools, your organization must have a clear understanding of the goals it has and how its employee monitoring strategy will best meet those goals.
For example, employee monitoring software provides insights into employee web browsing habits. This data is essential for ensuring that all employees are following your organization’s acceptable use policies.
Common Goals Include
- Ensuring compliance with data privacy and security regulations
- Mitigating and detecting insider threats
- Prevent the inappropriate usage of the internet and bandwidth
- Improving employee productivity
- Enforcing acceptable use policies for technology in the workplace
Common Features & Benefits of the Best Employee Monitoring Software
Internet Use Monitoring
Insights into bandwidth consumption, web browsing, and search queries provide detailed evidence of web activity, making it the perfect tool for enforcing internet use policies.
Software Utilization
36% of desktop software & 29% of SaaS spend is underutilized or wasted, with the average cost of unused computer software being $259 per desktop.
In this economic climate organizations need to maximize the value of their software investments by reducing unnecessary expenses and ensuring productivity-enhancing tools are adequately adopted.
With insights into software usage organizations can optimize software spend by identifying opportunities to reduce licenses for underutilized software and consolidate licenses for redundant solutions.
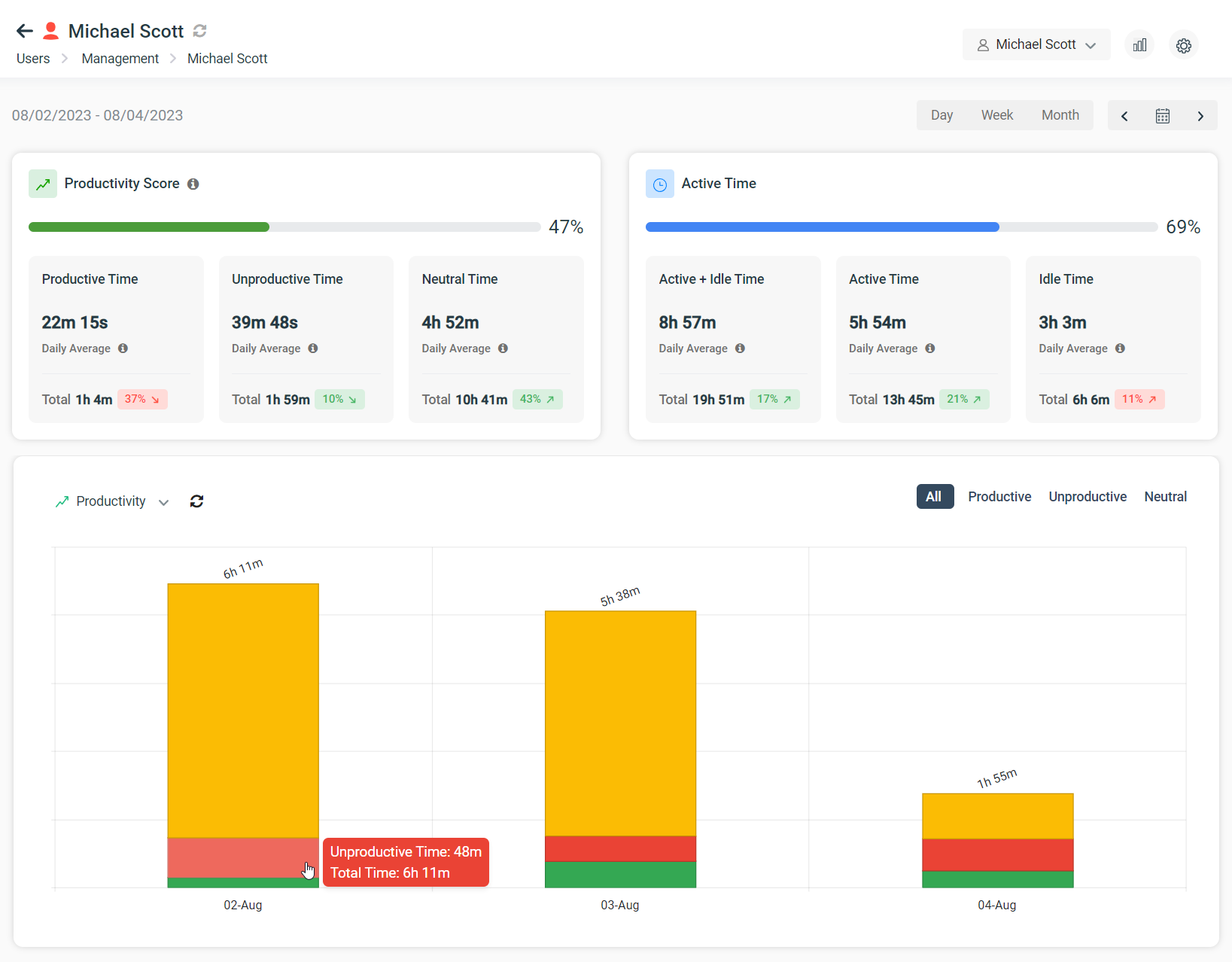
Productivity Monitoring
How much time is spent using productive vs unproductive applications and websites? Productivity tracking equip managers with the activity data they need to understand how in-house and remote team members are spending their time at work.
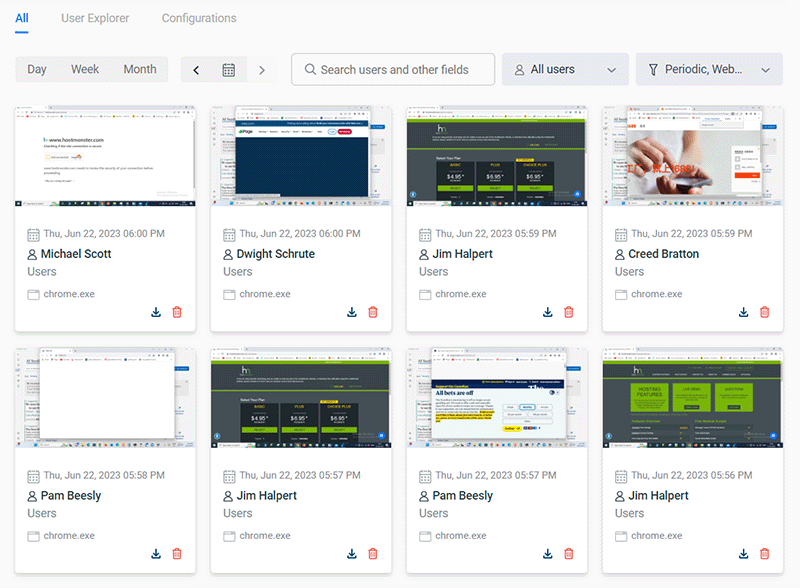
Screenshot Monitoring
Automatically capture screenshots when specific websites or applications are used, or take screenshots at a set interval. Screenshot monitoring provides a visual record of employee activities to complement user activity data.
Idle vs Active Time
How much time an employee spends actively using their computer vs simply having it turned on with apps and websites running in the background
Logon/Logoff Times
Records of when computers are turned on and off help verify employee attendance, detect computer activity outside of normal working hours, and provide insights into when employees with flexible schedules are typically working
Involve Stakeholders
A successful employee monitoring software deployment requires buy-in from your key stakeholders; your employees, business leaders, and software administrators.
Buy-in for new software starts from the top. Be prepared to address business requirements such as workplace privacy expectations, the anticipated ROI of employee PC monitoring software, and the suitability of the vendors you shortlist.
If employee buy-in is important to you, consult them early. Employees may have negative assumptions about tracking software; consult them in the planning process to mitigate these issues and have their voices heard.
By involving key stakeholders early in the process you’ll prevent barriers to implementation that could have been proactively addressed, such as financial backing and limitations from collective bargaining agreements.
Common Stakeholders
- Human resources staff, legal teams and union reps need to be consulted to ensure that your organization’s legitimate business interests are balanced with employee privacy rights and expectations.
- IT & security teams will be responsible for deploying and maintaining the monitoring solutions; they can provide insights into the security and system requirements that are suitable for your environment.
- Managers and other staff who will use the insights day-to-day need to understand how to use the tool and what insights they can gain from employee activity data. Where they work closely with their teams they may also serve as an advocate for any concerns your employees may have.
Learn More: How to Get Buy-In for Employee Tracking Software
Legal Considerations
When it comes to what you are allowed to monitor, many believe that if an employee is using company equipment, on company time, and getting paid by the company, that the company has every right to monitor their equipment and what the employee is doing with it.
While in the majority of cases, a company can monitor their employees so long as they have a legitimate business reason for doing so, it’s not always that simple. A variety of factors influence what employers can and cannot monitor.
Legal Considerations for Using Employee Monitoring Tools
- Jurisdiction: Employee privacy and monitoring laws vary depending on where the employer and the employee reside. A catch-all approach may not be suitable for a multinational company.
- Union Agreements: Independent agreements with unions and other workers’ rights organizations may include limitations about what employers can track and how data will be used.
- Proportionality: Different forms of monitoring may be restricted based on potential privacy impacts. For example, monitoring individual keystrokes is more invasive than monitoring web browsing history as tracking specific keystrokes has a greater chance of capturing sensitive personal information such as passwords.
- Privacy Expectations: Employees have a greater expectation of privacy on their personal devices. Monitoring laws may even go so far as to restrict the degree of monitoring that can take place when employees use company devices for personal use.
- Disclosure: Has the company made a legitimate effort to inform employees that they are being monitored? Are employees clear about whether or not they have a reasonable expectation of privacy on company devices?
Read Reviews & Case Studies
When determining the best employee monitoring software for your organization, it’s essential to seek out case studies from similar industries and company sizes, as well as reviews from independent third-party websites.
These resources help validate that a given solution has provided value for organizations that have similar requirements and needs as your own.
What to Look for in Employee Monitoring Software Reviews & Case Studies
- Customer Support Quality: Is their support team known to be knowledgeable, available, and helpful?
- Value & ROI: What value does the solution provide to its customers? Is this value worth the cost of deploying and maintaining the solution?
- Scalability & Reliability: Is the software stable, easy to manage, and working as advertised? Are customers with similar user counts experiencing any issues?
Demos & Trials
Having a first-hand proof-of-concept for the software is integral as it allows the organization to see how the software interacts with their existing environment before they invest considerable time, effort, and finances in fully implementing a given solution.
The software evaluation period is an ideal time to build a relationship with the software provider and judge whether or not they have the knowledge and skills to support the full-scale deployment of their software throughout the organization after purchasing.
If the software provider proves to be dismissive, uncommunicative, or unhelpful during the evaluation period, this is a sure sign that they do not prioritize the needs and success of their customers.
Pricing & Purchasing Considerations
While price shouldn’t be the most important factor when determining the best monitoring software for your organization, it’s certainly relevant.
Monitoring solutions can cost anywhere from $4-46 USD per user per month so it’s important to compare your requirements to each vendor’s capabilities and their associated costs.
During your evaluation, you’ll likely find that some of the requirements you identified may increase the cost factor considerably. In such an event it’s important to re-review your requirements to determine what is truly essential and what is a nice-to-have.
Common Pricing & Purchasing Considerations
- Minimum License Requirements: While some vendors allow you to get started with as little as 1 user, it’s more common to see 10 or greater license minimums
- Subscription vs Perpetual Licensing: The majority of employee monitoring software vendors use a subscription model; you must factor in these ongoing costs as part of your evaluation
- Monthly vs Annual Billing: Some vendors allow you to use their monitoring software month-to-month, though annual contracts are common. Pre-purchasing multiple years in advance is also a great way to reduce licensing costs
- Support Costs: Some vendors will charge an additional fee to help with the initial deployment and ongoing 1:1 support. Some may also offer premium support tiers with greater availability and responsiveness for an added cost.
Subscription vs Perpetual Licensing
Subscription pricing provides access to the software only for so long as an ongoing monthly or annual fee is paid. With subscription-based pricing, the organization will have immediate access to the latest feature updates provided by the software vendor and the associated costs can be made into an operating expense if desired. These advantages come at the expense of requiring ongoing payments to have access to the software.
Perpetual pricing provides permanent lifetime access to the software following a one-time payment. Perpetual pricing models allow the associated costs to be made into a capital expense if desired. As for the cost of updates, many software vendors will include a fixed-term period of software updates following the initial purchase.
Subscription pricing is the best model for computer monitoring solutions. These tools need continuous updates to remain compatible with operating systems, internet browsers, and other components.
As the ecosystem they are deployed in evolves, unexpected compatibility issues may arise. Choosing a vendor with a subscription licensing model ensures that you’ll receive the security and compatibility updates the solution requires to continue working.
Customer Support
Here at CurrentWare, we pride ourselves on our customer support. During and after your evaluation our team is here to help you over a phone call, live chat, or email. We will make sure that you get the best experience possible.
What To Look For In a Vendor’s Customer Support:
- Onboarding & Deployment: Does the software vendor provide the direct onboarding and customer support required to make the product integration as painless as possible? Is that level of support included with the software purchase or will an upgraded support and maintenance plan need to be purchased?
- Guides & Resources: Are the provided self-serve support resources (manuals, videos, website, etc) well-written and organized? How readily can solutions be found with the resources provided?
- Support Knowledge: How knowledgeable is the product support team of the vendor? Are they familiar with the specific needs of the organization and how they need to adapt to accommodate?
- Support Channels: How are customer support inquiries handled? Can you call and speak to someone directly? Is email and live chat support available? Or is self-serve the only option?
- Language & Communication: How well does the support team express themselves and understand your queries? Is multilingual support available?
Security & Privacy Considerations
The data collected by employee monitoring software can be incredibly sensitive. When evaluating vendors it’s essential to understand how your data is protected, who has access to it, and how it will be used.
- Do any third parties have access to your data? If so, does that violate any data security and privacy responsibilities your organization has?
- Can data be stored and managed on-premises, or are you forced to use the vendor’s cloud storage servers?
- Is your data accessible to the vendor in any way? If so, how are their employees prevented from accessing and misusing the data?
- Does the vendor engage in any form of data scraping?
- Are security updates regularly provided to ensure the platform remains secure as new threats and vulnerabilities emerge?
Employee Monitoring Software FAQ
Does CurrentWare Have Access To Employee Data?
No, CurrentWare cannot access your employee’s computer activity tracking data. CurrentWare’s software does not send your user’s computer usage data to CurrentWare. They are installed and managed by your organization.
All of the data collected by CurrentWare’s employee tracking software is stored on a database that is installed in your organization’s data center or cloud service provider.
With CurrentWare’s on-premises & self-managed cloud deployment options, you’re in complete control of your data.
- Sensitive employee data stays secured to your standards rather than being sent to a third party.
- Maintain data localization and residency compliance requirements by keeping employee data exactly where it needs to be.
- Retain auditable records of user activity for as long as you need
For more information please refer to our Terms of Service.
What Is Employee Monitoring Software? What Does It Do?
Employee monitoring software is a powerful monitoring tool that is used to see what users are doing on a remote computer.
This data provides valuable information for improving the performance and security of monitored devices.
By tracking the online behavior of employees you can ensure that their internet access is being used appropriately.
The best employee monitoring software records a variety of computer activities, including:
- Internet history (Websites visited, idle/active time, etc)
- Applications used
- Bandwidth usage
- File operations (files that are copied/created/deleted)
- Startup/shutdown events
- Logon/logoff events
Employee monitoring tools can also send email notifications to alert a manager when undesirable or suspicious activities happen on monitored computers.
These activity reports serve as valuable evidence of unproductive or high-risk computer activity.
How Does Employee Monitoring Software Work?
Employee monitoring software typically works by installing a monitoring agent on the employee’s computer. The software then captures and logs data related to the employee’s computer and internet activities. From there the monitoring software agent sends the activity data to a central server where it is stored and made available to the administrator of the software.
What Are The Benefits Of The Best Employee Monitoring Software?
There are numerous productivity, security, and cost-optimization benefits of using employee monitoring software, such as:
- Deterring counterproductive work behaviors (CWB) such as tardiness, time theft, bullying, and absenteeism.
- Improving employee productivity by deterring excessive personal internet usage and gaining deeper insights into employee workflows.
- Monitoring software utilization and adoption rates to determine what software should be consolidated or decommissioned
- Protecting sensitive information against high-risk computer activities such as visiting potentially dangerous websites or uploading files to personal cloud storage accounts.
According to a 2017 Spiceworks survey of IT professionals, the most common reasons that their employers monitor employees is to protect against malware and phishing scams, to prevent unacceptable user behavior, to prevent users from visiting inappropriate websites, for liability management/compliance purposes, and to protect sensitive information.
Learn More: The Benefits of Employee Productivity Tracking Software
Is Employee Monitoring Software Legal?
When determining how employee monitoring software will be used with the teams in your organization it is important to understand the potential privacy implications for your employees and what factors influence your right to monitor employee activity.
Depending on your jurisdiction and the jurisdiction of your employees you may have legal obligations to fulfill before monitoring employees in the workplace. The best practice is to consult with a legal professional first.
Most workplace privacy and employee monitoring laws require you to be transparent about data collection. This includes informing employees about what is being monitored, how their data will be protected, and how it will be used.
Typically this disclosure is provided in an employee manual, workplace monitoring policy, or acceptable use policy.
The best computer monitoring software helps you meet your privacy requirements with privacy-enhancing features such as alerting your users that their computer activity is being monitored.
Who Uses Employee Monitoring Software?
Employee computer monitoring software is used by a wide variety of industries. It is most commonly found in industries that are required to monitor employee activity for data security compliance purposes.
Examples of industries that use employee monitoring software include financial services, manufacturing, government, and healthcare.
What Are the Challenges of Using Employee Monitoring Software?
Implementing an employee monitoring solution is not without its risks. Before monitoring your employees with employee monitoring software you must first evaluate the pros and cons of employee monitoring to see if it’s the right choice for your company.
Some common challenges of monitoring employees include:
- Potentially sensitive personal information may be captured. If employees doubt whether or not their personal information is adequately protected from misuse there is a legitimate concern that their web browsing history can be unfairly used against them.
- If employees use their work computer for personal tasks the monitoring software may capture personal details such as racial identity, personal web browsing habits, religious beliefs, and health concerns
- Automated screenshot capturing software will capture everything on their screens including banking details, personal messages they may be writing, and any classified information they may be working with
- Employees could be concerned that the insights will be used unfairly or that their activity data will create a bias that will impact their professional career
- An invasive employee monitoring solution may lead to legal issues if the company does not adequately comply with employee privacy legislation. Privacy laws typically require advanced disclosure of the intent to monitor and only monitoring what is required to meet the business’ legitimate interests without disproportionately harming employee privacy.
Learn More: The Negative Effects of Employee Monitoring (& What You Can Do)
How Can I Get The Best Price For Employee Monitoring Software?
While at first glance it may appear that the advertised list price of employee monitoring software is the best price you will get, the majority of vendors will negotiate for more advantageous pricing based on a variety of factors.
How to Get the Best Price for Employee Monitoring Software
- Prepayment & Bulk Licensing: Pricing breaks are typically available for businesses that sign up for multi-year plans or can commit to bulk orders. The starting volume of license discounts varies by vendor, with some vendors offering discounts at as low as 100 users. Volume discounts often increase depending on the number of licenses and the length of the contract term.
- Managed Service Providers & Resellers: Vendors with partner programs for MSPs and VARs will provide licenses for their software at a cost below MSRP so that their partners can earn money based on their resale margins and ability to provide employee monitoring capabilities to their clients.
- Industry Discounts: Some vendors will provide exclusive discounts to particular industries such as nonprofits and education institutions.
Should I Tell Employees That They Are Being Monitored?
While being transparent about employee monitoring is the recommended best practice, giving notice to employees is not always required.
The majority of jurisdictions require each worker to be made aware of their employer’s intent to monitor. Some jurisdictions with greater rules and laws will further dictate that employees must be made explicitly aware of what data is captured, how it will be used (such as productivity management), and who will have access to it.
The best employee monitoring software will allow your organization to be in control of how visible the data loss prevention software is.
CurrentWare’s employee monitoring software solutions operate in stealth mode by default.
In stealth mode, the CurrentWare software client is not visible in the system tray or control panel of the user’s computer. Your users will not be able to uninstall the program or stop it without administrator privileges.
If you would like your users to be aware that they are being monitored, you can choose to show the CurrentWare software client in their system tray by enabling it in the client software settings.
CurrentWare provides a variety of privacy-enhancing features such as
- The ability to choose what computer activities are monitored, such as not monitoring idle vs active time or disabling tracking for specific users
- A tracking scheduler that allows you to stop monitoring your users at designated off-hours times such as breaks
- The ability to make the CurrentWare client visible in the system tray
- An end-user reports dashboard that provides your users with access to their data
- The ability to display a custom message to notify your users that they are being monitored
Learn More: CurrentWare’s privacy features
Can Employers Monitor Their Employees’ Personal Computers?
It depends. If an employer allows employees to use personal devices for work purposes the employer may have legitimate business reasons to require the use of employee tracking software such as:
- Protecting sensitive data against data breaches/data leaks
- Automated time tracking
- To track employee productivity
- Insider threat detection
- App tracking to reduce costs
- Deter access to certain websites that may pose cybersecurity risks to sensitive data and related systems
That said, from a legal perspective employers are seldom justified in monitoring the computer activity of employee-owned devices.
Furthermore, under the vast majority of circumstances, an employer will not be justified in secretly monitoring an employee’s personal computer. They will be required to notify them through a workplace monitoring policy, acceptable use policy, or similar company policy.
From both a security and privacy perspective, employers with a BYOD program should have their employees connect to a virtual machine that allows them to keep their computer activity, company software, and files separate from their personal activity.