CurrentWare’s Platform Security Options
CurrentWare is committed to the security of its platform, its customers, and their data. Here’s an overview of the security measures we take to keep the CurrentWare Suite safe.
Authentication Security
- Password Protected: The admin console cannot be accessed without a designated password-protected Admin or Operator account
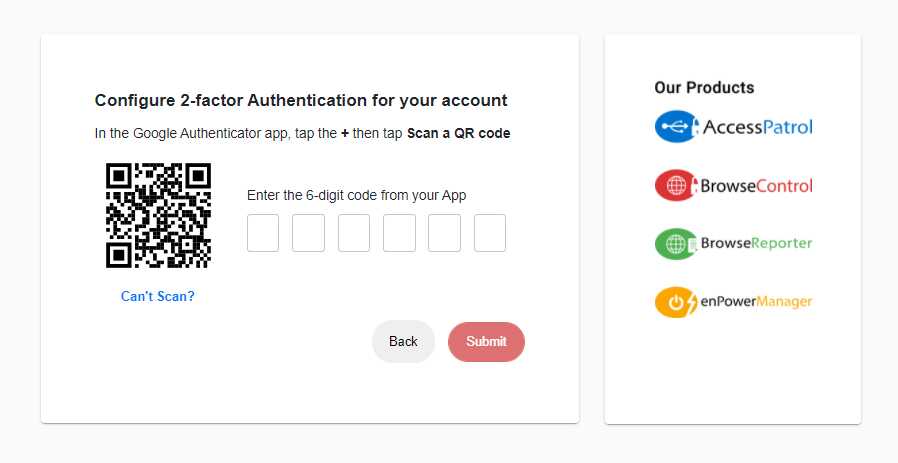
- Two-Factor Authentication: Require Admins and Operators to provide both a username/password and a time-based one-time password (TOTP)
- Single Sign-On(SSO) Authentication: Integrate with your organizations existing identity provider for seamless authentication.
Privilege & Access Control
-
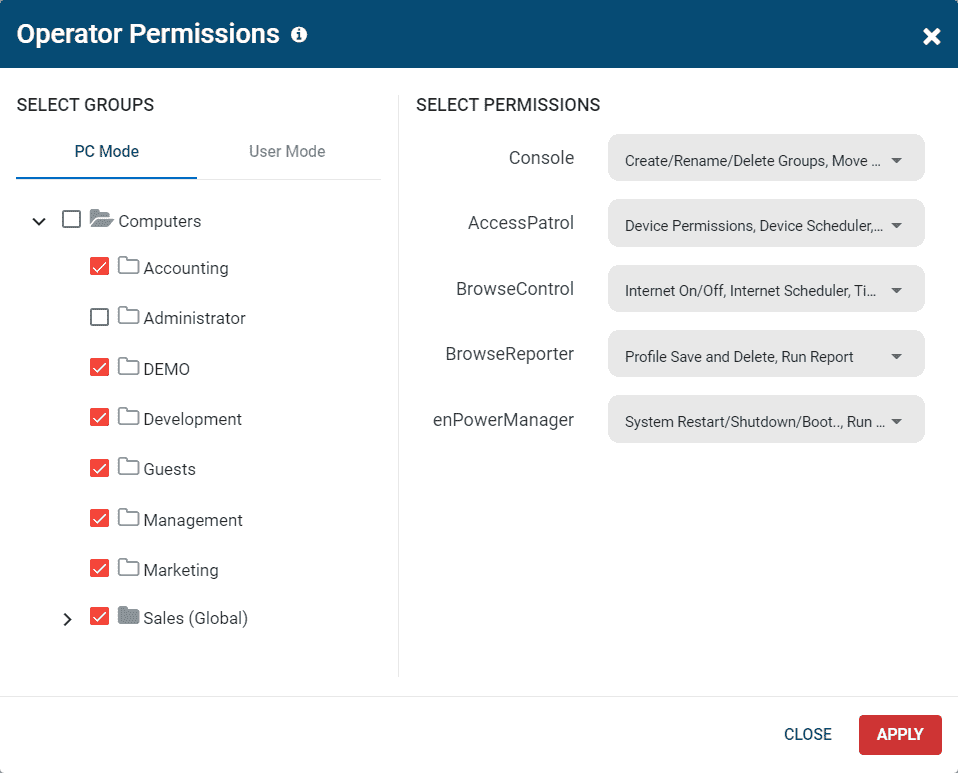
Role-Based Access Control (RBAC): Password-protected and selectively restricted Operator accounts are created by the administrator to provide trusted employees with access to select functions or user/PC groups within the CurrentWare Suite.
- Limit Data Access: Give Operators access to the data of their direct reports without providing them access to the rest of the database.
- Restrict Privileges: Control what user/PC groups each Operator can modify security policies for, such as allowing a manager to block/unblock websites for their department only.
- No Default External Access: Access the web console from the convenience of a web browser on any computer in your internal network, or configure optional remote access options.
Admin Activity Logs
- Web Console Login Activity: Track the login activity of Admins and Operators within the CurrentWare Web Console
- BrowseControl Policy Updates Log: See when web filtering policies have been updated, the # of URLs/Categories updated, and information about the client computer that received the update
- Admin Audit Logs: These audit logs help you answer “who did what, where, and when?” when it comes to configuration changes and data access within the CurrentWare Suite.
Data Security
- You Control Your Data: The CurrentWare Suite is hosted and managed by your company either on premises, through VDI, or using a cloud service provider of your choice; CurrentWare cannot access your user’s data or modify your policies
- Custom Data Retention: Automatically delete user activity data at a set schedule using the Auto Delete Scheduler
- Limit Data Collection: Selectively enable/disable what is being tracked or only track your users during set hours
- HTTPS: The web console includes a self-signed SSL certificate that provides encrypted access to the web console
- SQL Encryption: Use SQL Transparent Data Encryption (TDE) to keep your user activity data safe
Client Integrity
- Unstoppable: End-users cannot stop the client from running, ensuring your security policies and data collection continue uninterrupted.
- Stealth Mode: Install CurrentWare in stealth mode to prevent end-users from detecting the client in their programs list.
- Password Protected: When the client is optionally made visible to end-users is remains protected by an admin password to prevent interference.
CurrentWare’s Security Practices
A third-party security vendor has completed a security assessment that validates CurrentWare is following industry best practices to ensure the confidentiality, availability, and integrity of all of our IT assets and data.
CurrentWare has implemented an information security policy and system of controls aligned to the ISO 27001/27002 standard, with additional best practices from industry-standard frameworks such as NIST 800-171, the NIST Cybersecurity Framework (CSF), and the CyberSecure Canada Baseline Controls.
Our focus is on implementing controls from these standards to enhance our security posture, specifically tailored to our customers’ and stakeholders’ needs.
For further information about CurrentWare’s security practices, please contact info@currentware.com or your CurrentWare representative.
Single Sign-On(SSO) Integration
- Seamless Access: Integrate with your organizations existing identity provider. Streamlined authentication process simplifies access for authorized users.
- Enhanced Security: Reduces password fatigue and phishing risks while enabling stronger authentication methods.
- Regulatory Compliance: Helps meet security and compliance requirements with enforced access controls.
- Simplified IT Management: Centralized authentication reduces the burden of password resets and support tickets.
CurrentWare's Key Features
User Activity Monitoring
Track web browsing, software use, search queries, and more
Screenshot Monitoring
Take automatic screenshots or remotely view desktops
Track Software Usage
Get insights into software usage trends in your organization
Transparent & Stealth Modes
Run silently in the background or provide notice of monitoring
Block USB & Other Devices
Set full access, read only or no access on storage devices
Device Whitelist
Allow only authorized storage devices to be used
Block File Transfers
Prevent files from being transferred to portable storage
DLP Activity Reports
Track file transfers, storage device use, file operations, and more
Block Websites
Block websites based on
URLs & content categories
Block Downloads/Uploads
Prevent uploading and downloading based on file type
Application Blacklisting
Block specific Windows
applications from launching
PC Power Management
Remotely track and control PC power states
Central Web Console
Save time with a central admin console; optionally integrate Active
Directory OUs or security groups
Platform Security
Protect your CurrentWare console
with 2FA, passwords, privilege
management, and more
Offsite Management
Extend onsite security policies to computers running outside the corporate network
SQL Server Supported
Database scaled for enterprise and
large business operations using
Microsoft SQL Server