Trusted by
& many more
Trusted by
& many more
How CurrentWare’s Security Solutions Align With Cyber Essentials Compliance Goals
Monitor Activity on Privileged Accounts
Prevent administrator accounts from being used to carry out every day tasks with CurrentWare’s user activity monitoring and restriction capabilities
- Audit privileged account activity for excessive use
- Get automated user activity reports in your inbox
- Proactively restrict access to unnecessary websites to limit exposure to the internet
“Use separate accounts to perform administrative activities only (no emailing, web browsing or other standard user activities that may expose administrative privileges to avoidable risks)”
— Cyber Essentials v3.1 (Montpellier)

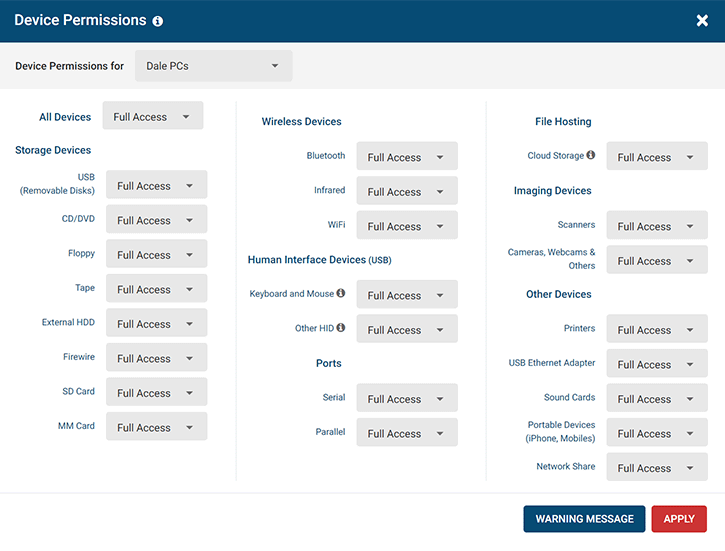
Enforce the Principle of Least Privilege
Leverage CurrentWare’s understanding of user activities to design granular RBAC policies
- Restrict access to applications, websites, peripheral devices, and more to further enforce user access restrictions
- Monitor user activity to see who is accessing sensitive applications and websites
- Assign specific access permissions to user groups based on their job functions
“Provide access to only those applications, computers and networks the user needs to carry out their role”
“Remove or disable special access privileges when no longer required (when a member of staff changes role, for example)”
— Cyber Essentials v3.1 (Montpellier)

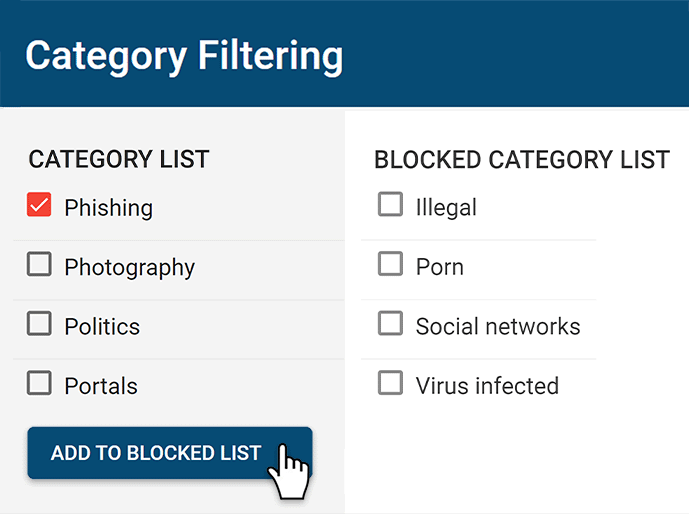
Restrict Access to High-Risk Sites
Enforce internet use policies and improve internet security with granular internet access control policies
- Block websites based on URLs and content categories
- Effortlessly block millions of websites across 100+ URL categories
- Limit internet use to an Allow List for optimal endpoint security
Monitor & Control Software Usage
CurrentWare monitors software usage, helping you identify unauthorized applications running on devices.
- Audit user activity to identify the use of unauthorized software
- Proactively block the launching of specific applications
- Prevent the downloading of executable files such as .msi and .exe
“Have you removed any software installed on your devices that is no longer supported and no longer receives regular updates for security problems?”
“Where you are able to do so, have you removed or disabled all the software and services that you do not use”
“Do you ensure that users only install applications that have been approved by your organisation?”
— Cyber Essentials Question Set (Montpellier)

“Software that is not removed from devices when it becomes un-supported will need to be placed onto its own sub-set with no internet access.
If the out-of-scope subset remains connected to the internet, you will not be able to achieve whole company certification”
— Cyber Essentials Question Set (Montpellier)

The Benefits of Cyber Essentials Certification
Cybersecurity Threats Are on the Rise
74% of large and 70% of medium businesses in a 2024 DSIT survey reported experiencing a recent cyber attack
Ensure Business Continuity
59% of buyers in an Arcserve report said they are likely to avoid companies that suffered from a recent cyberattack
Build Trust
70% of consumers believe that businesses aren’t doing enough to keep their personal information secure
How to Improve Data Security With CurrentWare
Go beyond the minimum Cyber Essentials compliance requirements with all of the security controls available in the CurrentWare Suite
Block & Audit Storage Devices
Control who can use portable storage devices and set security policies to limit what devices are allowed. Monitor data transfers to removable media and network storage devices to ensure that your data security policies are being followed.
Prevent Data Loss to Cloud Platforms
Protect sensitive data against the risks of cloud file sharing sites. Block cloud storage sites/apps, restrict uploads/downloads, and monitor file transfers for high-risk or anomalous activity.
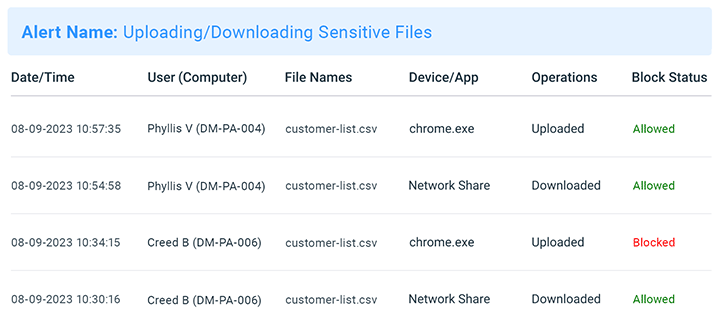
Audit User Activity for Insider Threat Risks
Monitor employee computer usage for signs of insider threats. Track file transfers, web browsing, app use, and login/logout times for high-risk, anomalous, or inappropriate activity. Receive automated alerts straight to your inbox when specific events occur.
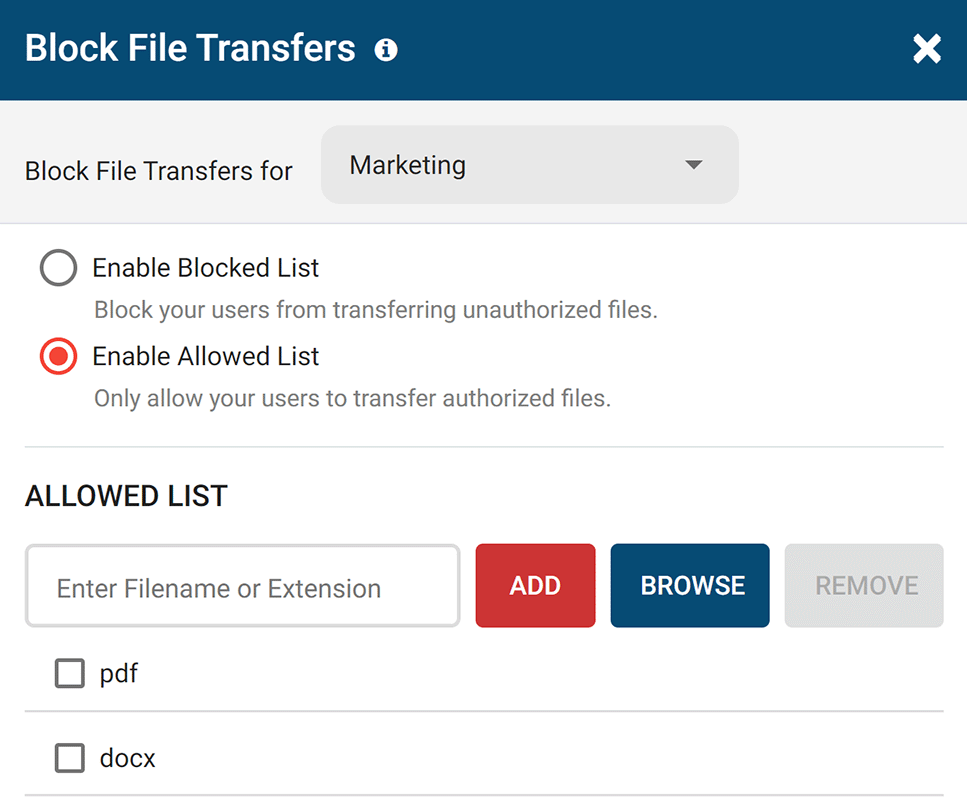
Block Data Transfers to Portable Storage & Uploads/Downloads
Go beyond simply blocking unauthorized devices; ensure optimal data protection with your trusted devices, too. Block file transfers to portable storage devices based on file extension and file name.
Use the File Filter to prevent the uploading and downloading of specific files such as EXEs.
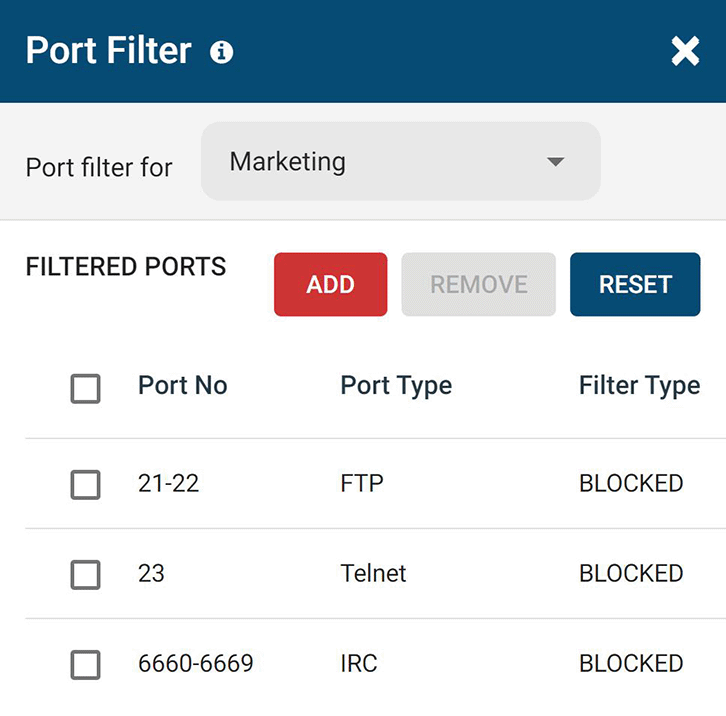
Block High-Risk Network Ports
Block unused TCP/UDP ports to reduce the attack surface of your network. Improve data protection by mitigating the threat of data leakage over FTP, SFTP, IRC, and other high-risk network ports.
Block Risky Sites
BrowseControl’s web content category filtering database provides you with a convenient way to block millions of websites across over 100 URL categories. Easily block users from accessing social media, porn, games, known virus-infected websites, and more!
CASE STUDY
Boston Centerless Scales Production & Secures Their Remote Workforce
CurrentWare has been nothing but supportive of us since we started. This is probably one of the best systems that we’ve ever invested in.
Once we got CurrentWare installed it opened the door for remote work for us; we could control the equipment and make sure our people were being productive and safe.
CurrentWare's Key Features
User Activity Monitoring
Track web browsing, software use, search queries, and more
Screenshot Monitoring
Take automatic screenshots or remotely view desktops
Track Software Usage
Get insights into software usage trends in your organization
Transparent & Stealth Modes
Run silently in the background or provide notice of monitoring
Block USB & Other Devices
Set full access, read only or no access on storage devices
Device Whitelist
Allow only authorized storage devices to be used
Block File Transfers
Prevent files from being transferred to portable storage
DLP Activity Reports
Track file transfers, storage device use, file operations, and more
Block Websites
Block websites based on
URLs & content categories
Block Downloads/Uploads
Prevent uploading and downloading based on file type
Application Blacklisting
Block specific Windows
applications from launching
PC Power Management
Remotely track and control PC power states
Central Web Console
Save time with a central admin console; optionally integrate Active
Directory OUs or security groups
Platform Security
Protect your CurrentWare console
with 2FA, passwords, privilege
management, and more
Offsite Management
Extend onsite security policies to computers running outside the corporate network
SQL Server Supported
Database scaled for enterprise and
large business operations using
Microsoft SQL Server
Learn How to Meet These Compliance Requirements With CurrentWare
NERC CIP
Protect TCAs & BCSI From Insider Threats
ISO 27001
Increase the Maturity of Your ISO27K ISMS
NIST 800-171/53
Protect Controlled Unclassified Information
CIPA for Education
Qualify for the FCC’s
E-Rate Program

Cyber Essentials
Critical Security Controls For Your Assessment

CMMC
Protect CUI to qualify for DoD contracts