Trusted by
& many more
Trusted by
& many more
NERC CIP Compliance Requirements You Can Address With CurrentWare
NERC CIP-003-8 — Security Management Controls
The purpose of NERC CIP-003-8 is to specify consistent and sustainable security management controls that establish responsibility and accountability to protect BES Cyber Systems against compromise that could lead to misoperation or instability in the Bulk Electric System (BES).
CurrentWare’s NERC CIP compliance solutions provide several security controls to mitigate the risk of introducing malicious code to BES Cyber Systems through the use of Transient Cyber Assets or Removable Media.
| Requirement | CurrentWare Modules & Features |
|
Cyber Security Awareness
Each Responsible Entity shall reinforce, at least once every 15 calendar months, cyber security practices. |
BrowseReporter
AccessPatrol
|
|
Cyber Security Incident Response
Each Responsible Entity shall have one or more Cyber Security Incident response plan(s), either by asset or group of assets, which shall include identification, classification, and response to Cyber Security Incidents |
BrowseReporter
AccessPatrol
|
|
Transient Cyber Asset and Removable Media Malicious Code Risk Mitigation
Each Responsible Entity shall implement, except under CIP Exceptional Circumstances, one or more plan(s) to achieve the objective of mitigating the risk of the introduction of malicious code to low impact BES Cyber Systems through the use of Transient Cyber Assets or Removable Media. |
AccessPatrol
BrowseControl
|
NERC CIP-007-6 — System Security Management
The purpose of NERC CIP-007-6 is to manage system security by specifying select technical, operational, and procedural requirements in support of protecting BES Cyber Systems against compromise that could lead to misoperation or instability in the Bulk Electric System (BES).
CurrentWare’s NERC CIP compliance solutions complement your Electronic Security Perimeter with technical security controls that protect against the use of unnecessary ports and removable media on managed endpoints.
Easily lock down Transient Cyber Assets used by field workers to protect BES Cyber Systems against insider threats and malicious activity.
| Requirement | CurrentWare Modules & Features |
|
Table R1– Ports and Services
Where technically feasible, enable only logical network accessible ports that have been determined to be needed by the Responsible Entity, including port ranges or services where needed to handle dynamic ports.
|
BrowseControl
|
|
Table R1– Ports and Services
Protect against the use of unnecessary physical input/output ports used for |
AccessPatrol
Learn More: Which devices can I control with AccessPatrol?
|
|
Table R3 – Malicious Code Prevention
Deploy method(s) to deter, detect, or |
AccessPatrol
BrowseControl
BrowseReporter
Learn More: CurrentWare’s endpoint security solutions
|
|
Table R4 – Security Event Monitoring
Log events at the BES Cyber System 4.1.1. Detected successful login 4.1.2. Detected failed access 4.1.3. Detected malicious code. ── 4.2 Generate alerts for security events that the Responsible Entity determines necessitates an alert. ── 4.4 Review a summarization or sampling of logged events as determined by the Responsible Entity at intervals no greater than 15 calendar days to identify undetected Cyber Security Incidents. |
enPowerManager
AccessPatrol
BrowseReporter
CurrentWare Web Console
|
|
Table R4 – Security Event Monitoring
Where technically feasible, retain applicable event logs identified in Part 4.1 for at least the last 90 consecutive calendar days except under CIP Exceptional Circumstances. |
|
NERC CIP-010-4 — Configuration Change Management and Vulnerability Assessments
The purpose of NERC CIP-010-4 is to prevent and detect unauthorized changes to BES Cyber Systems by specifying configuration change management and vulnerability assessment requirements in support of protecting BES Cyber Systems from compromise that could lead to misoperation or instability in the Bulk Electric System (BES). | Learn More
CurrentWare’s NERC CIP compliance solutions provide critical insights into what computer applications are being used in BES Cyber Systems, allowing you to detect and investigate unauthorized software that could pose a security risk.
| Requirement | CurrentWare Modules & Features |
|
Table R2 – Configuration Monitoring
Monitor at least once every 35 calendar days for changes to the baseline configuration. Document and investigate detected unauthorized changes. |
BrowseReporter
CurrentWare Web Console
|
NERC CIP-011-3 — Cyber Security — Information Protection
The purpose of NERC CIP-011-3 is to prevent unauthorized access to BES Cyber System Information (BCSI) by specifying information protection requirements in support of protecting BES Cyber Systems against compromise that could lead to misoperation or instability in the Bulk Electric System (BES). | Learn More
CurrentWare’s NERC CIP compliance solutions provide the technical security controls that Responsible Entities need to ensure the confidentiality of BCSI against insider threats.
| Requirement | CurrentWare Modules & Features |
|
Table R1 – Information Protection Program
Method(s) to protect and securely handle BCSI to mitigate risks of compromising confidentiality. |
AccessPatrol
BrowseControl
BrowseReporter
Learn More: CurrentWare’s data loss prevention solutions
|
Flexible Deployment Options
With CurrentWare’s cybersecurity, web filtering, data loss prevention, and user activity monitoring solutions you’re in complete control of how your data is stored, secured, and retained. Your employees' data cannot be accessed by CurrentWare.
On Premises
Keep Control of Your Data
Install the management software on a standard computer, then deploy the client software to your users' computers
Remote Workers
Monitor & Manage on Any Network
Connect your remote employees’ computers to the management software with simple port forwarding rules
Self-Managed Cloud & VDI
Citrix, Azure, AWS, GCP, and More!
Enjoy the scalability and availability of the cloud alongside the security, control, and flexibility of our on-premises solution
Get Advanced Activity Insights
BrowseReporter is a versatile computer activity monitoring software to track productivity, web browsing, and app use
- Make informed decisions
- Enforce company policies
- Improve productivity
Block Harmful Websites
BrowseControl is an easy-to-use website blocking software for restricting internet access
- Block URLs & categories
- Block unwanted apps
- Website allow & block lists
Stop Data Theft to USB Devices
AccessPatrol is USB control software to protect sensitive data against theft to portable storage devices
- Block USB devices
- USB file activity alerts
- Block file transfers
Control PC Power States
enPowerManager is a remote PC power manager for centrally managing power settings across all endpoints.
- Track logon and logoff times
- Log PC power event history
- Remotely shutdown PCs
We’re Here to Help
The CurrentWare team prides itself on its high-quality customer support. We will support you every step of the way—whether you’re just starting your free trial or actively using CurrentWare in your network.
At CurrentWare, customer success is our priority at every stage of your journey. We take pride in providing high-quality and reliable pre and post-sale support to make your experience exceptional.
We offer the same level of high-quality support to all of our customers—no extra fees or packages necessary!
Mike Noseworthy
Customer Support Lead
Product Training
CurrentWare provides the documentation, training, and other resources you need to take full advantage of the capabilities of our products.
Technical Support
Our expert support team is here to help you. Reach out to us over email, live chat, or phone from 8:00 AM – 6:00 PM ET, Monday to Friday.
See What Our Customers Have to Say
This software helps us to achieve compliance with industry and government requirements with respect to controlling the use of removable storage media. It fits the bill perfectly.
Matthew W, Project Manager
Aviation & Aerospace Industry, 11-50 employees
In my nearly 40 years in the IT business I’ve worked with a lot of support teams. I really appreciate CurrentWare going the extra mile to help me get the most out of the product. They’ve definitely outweighed any of the other competitors that I’ve looked at.
J.S, Managed Services Provider
Vehicle Dealership, 150-200 Employees
The reports are very easy to understand and the fact that they can be emailed to you on a schedule is amazing... Customer support has been fantastic every time I've had to reach out to them; I highly recommend them!
Kristen S, Associate IT Director
The Coding Network, 700+ Employees
We have experienced data leaks by dishonest employees in the past and AccessPatrol has helped us avoid them and work with greater security and peace of mind for us and our customers.
Julio V, Head of Information Technology
Financial Services Industry, 10,001+ employees
FREE DOWNLOAD
Removable Media Policy Template
Download this data security policy template to prevent data leakage to USB flash drives and other removable storage devices.
- Set data security standards for portable storage
- Define the acceptable use of removable media
- Inform your users about their security responsibilities
CurrentWare's Key Features
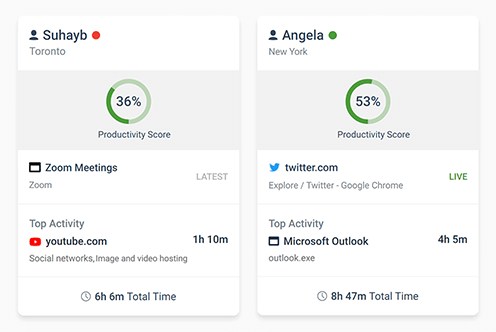
User Activity Monitoring
Track web browsing, software use, search queries, and more
Screenshot Monitoring
Take automatic screenshots or remotely view desktops
Track Software Usage
Get insights into software usage trends in your organization
Transparent & Stealth Modes
Run silently in the background or provide notice of monitoring
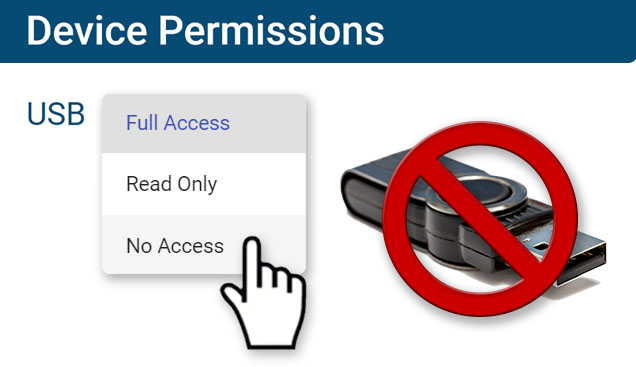
Block USB & Other Devices
Set full access, read only or no access on storage devices
Device Whitelist
Allow only authorized storage devices to be used
Block File Transfers
Prevent files from being transferred to portable storage
DLP Activity Reports
Track file transfers, storage device use, file operations, and more
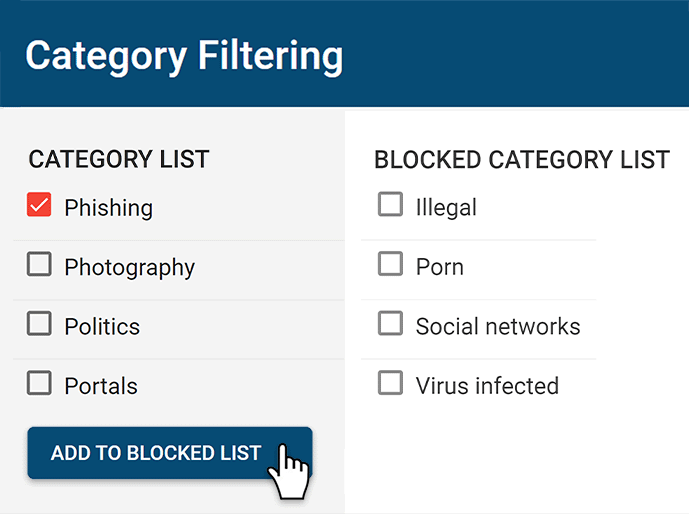
Block Websites
Block websites based on
URLs & content categories
Block Downloads/Uploads
Prevent uploading and downloading based on file type
Application Blacklisting
Block specific Windows
applications from launching
PC Power Management
Remotely track and control PC power states
Central Web Console
Save time with a central admin console; optionally integrate Active
Directory OUs or security groups
Platform Security
Protect your CurrentWare console
with 2FA, passwords, privilege
management, and more
Offsite Management
Extend onsite security policies to computers running outside the corporate network
SQL Server Supported
Database scaled for enterprise and
large business operations using
Microsoft SQL Server
Learn How to Meet These Compliance Requirements With CurrentWare
NERC CIP
Protect TCAs & BCSI From Insider Threats
ISO 27001
Increase the Maturity of Your ISO27K ISMS
NIST 800-171/53
Protect Controlled Unclassified Information
CIPA for Education
Qualify for the FCC’s
E-Rate Program

Cyber Essentials
Critical Security Controls For Your Assessment

CMMC
Protect CUI to qualify for DoD contracts