Trusted by
& many more
Trusted by
& many more
NIST 800-53 & NIST 800-171 Compliance Requirements
You Can Address With CurrentWare
| Requirement | CurrentWare Modules & Features |
|
Access Control AC-6 Least Privilege The organization employs the principle of least privilege, allowing only authorized accesses for users (or processes acting on behalf of users) which are necessary to accomplish assigned tasks in accordance with organizational missions and business functions.
|
BrowseControl
AccessPatrol
|
|
AC-18 Wireless Access The organization: a. Establishes usage restrictions, configuration/connection requirements, and implementation guidance for wireless access; and b. Authorizes wireless access to the information system prior to allowing such connections. AC-18 (3) Disable Wireless Networking |
AccessPatrol
|
|
AC-19 (4)(c) Restricts the connection of classified mobile devices to classified information systems in accordance with [Assignment: organization-defined security policies]. |
AccessPatrol
|
| Requirement | CurrentWare Modules & Features |
|
Audit and Accountability AU-3 Content of Audit Records The information system generates audit records containing information that establishes what type of event occurred, when the event occurred, where the event occurred, the source of the event, the outcome of the event, and the identity of any individuals or subjects associated with the event. AU-6 Audit Review, Analysis, and Reporting The organization: a. Reviews and analyzes information system audit records [Assignment: organization-defined frequency] for indications of [Assignment: organization-defined inappropriate or unusual activity]; and b. Reports findings to [Assignment: organization-defined personnel or roles]. AU-8 Time Stamps: The information system: b. Records time stamps for audit records that can be mapped to Coordinated Universal Time (UTC) or Greenwich Mean Time (GMT) and meets [Assignment: organization-defined granularity of time measurement]. AU-14 Session Audit: Session audits include, for example, tracking websites visited and recording information and/or file transfers
|
BrowseReporter
AccessPatrol
enPowerManager
CurrentWare Web Console
|
|
AU-4 Audit Storage Capacity
AU-11 Audit Record Retention: |
The CurrentWare Suite is hosted and managed by your company either on-premises or via a cloud service provider of your choice, giving you full control over data retention. Data can be culled automatically after a set time period; which data types are retained can also be customized.
|
|
AU-15 Alternate Audit Capability: The organization provides an alternate audit capability in the event of a failure in primary audit capability that provides [Assignment: organization-defined alternate audit functionality]. |
All of CurrentWare’s security policies and user activity data have a local cache failsafe in the event that a connection to the server is lost. All user activity is still captured and will sync with the primary database once a connection is reestablished. |
| Requirement | CurrentWare Modules & Features |
|
Configuration Management CM-7 Least Functionality a. Configures the information system to provide only essential capabilities; and b. Prohibits or restricts the use of the following functions, ports, protocols, and/or services: [Assignment: organization-defined prohibited or restricted functions, ports, protocols, and/or services]. CM-7 (4)(b) The organization employs an allow-all, deny-by-exception policy to prohibit the execution of unauthorized software programs on the information system
|
BrowseControl
|
|
CM-10 Software Usage Restrictions The organization: a. Uses software and associated documentation in accordance with contract agreements and copyright laws; b. Tracks the use of software and associated documentation protected by quantity licenses to control copying and distribution; and c. Controls and documents the use of peer-to-peer file sharing technology to ensure that this capability is not used for the unauthorized distribution, display, performance, or reproduction of copyrighted work. |
AccessPatrol
BrowseReporter
BrowseControl
|
|
CM-11 User-Installed Software The organization: a. Establishes [Assignment: organization-defined policies] governing the installation of software by users; b. Enforces software installation policies through [Assignment: organization-defined methods]; and c. Monitors policy compliance at [Assignment: organization-defined frequency]. |
AccessPatrol
BrowseReporter
BrowseControl
|
| Requirement | CurrentWare Modules & Features |
|
Incident Response IR-5 Incident Monitoring The organization tracks and documents information system security incidents. IR-5 (1) |
BrowseReporter
AccessPatrol
enPowerManager
CurrentWare Web Console
|
| Requirement | CurrentWare Modules & Features |
|
Media Protection MP-7 Media Use: |
AccessPatrol
Learn More: Which devices can I control with AccessPatrol?
|
| Requirement | CurrentWare Modules & Features |
|
Systems and Services Acquisition
SA-9 External Information System Services | Processing, Storage, and Service Location The organization restricts the location of [Selection (one or more): information processing; information/data; information system services] to [Assignment: organization-defined locations] based on [Assignment: organization-defined requirements or conditions]. Supplemental Guidance: The location of information processing, information/data storage, or information system services that are critical to organizations can have a direct impact on the ability of those organizations to successfully execute their missions/business functions. This situation exists when external providers control the location of processing, storage or services. The criteria external providers use for the selection of processing, storage, or service locations may be different from organizational criteria. For example, organizations may want to ensure that data/information storage locations are restricted to certain locations to facilitate incident response activities (e.g., forensic analyses, after-the-fact investigations) in case of information security breaches/compromises. |
All data collected by the CurrentWare Suite is controlled and managed by the organization with no reliance on third-party data processors or controllers required.
The organization can host the data on-premises or with a trusted cloud services provider of their choice. |
| Requirement | CurrentWare Modules & Features |
|
System and Communications Protection SC-43 Usage Restrictions The organization: a. Establishes usage restrictions and implementation guidance for [Assignment: organization-defined information system components] based on the potential to cause damage to the information system if used maliciously; and b. Authorizes, monitors, and controls the use of such components within the information system. Information system components include hardware, software, or firmware components (e.g., Voice Over Internet Protocol, mobile code, digital copiers, printers, scanners, optical devices, wireless technologies, mobile devices). |
AccessPatrol
BrowseControl
BrowseReporter
|
Flexible Deployment Options
With CurrentWare’s cybersecurity, web filtering, data loss prevention, and user activity monitoring solutions you’re in complete control of how your data is stored, secured, and retained. Your employees' data cannot be accessed by CurrentWare.
On Premises
Keep Control of Your Data
Install the management software on a standard computer, then deploy the client software to your users' computers
Remote Workers
Monitor & Manage on Any Network
Connect your remote employees’ computers to the management software with simple port forwarding rules
Self-Managed Cloud & VDI
Citrix, Azure, AWS, GCP, and More!
Enjoy the scalability and availability of the cloud alongside the security, control, and flexibility of our on-premises solution
FREE DOWNLOAD
Removable Media Policy Template
Download this data security policy template to prevent data leakage to USB flash drives and other removable storage devices.
- Set data security standards for portable storage
- Define the acceptable use of removable media
- Inform your users about their security responsibilities
See What Our Customers Have to Say
This software helps us to achieve compliance with industry and government requirements with respect to controlling the use of removable storage media. It fits the bill perfectly.
Matthew W, Project Manager
Aviation & Aerospace Industry, 11-50 employees
In my nearly 40 years in the IT business I’ve worked with a lot of support teams. I really appreciate CurrentWare going the extra mile to help me get the most out of the product. They’ve definitely outweighed any of the other competitors that I’ve looked at.
J.S, Managed Services Provider
Vehicle Dealership, 150-200 Employees
The reports are very easy to understand and the fact that they can be emailed to you on a schedule is amazing... Customer support has been fantastic every time I've had to reach out to them; I highly recommend them!
Kristen S, Associate IT Director
The Coding Network, 700+ Employees
We have experienced data leaks by dishonest employees in the past and AccessPatrol has helped us avoid them and work with greater security and peace of mind for us and our customers.
Julio V, Head of Information Technology
Financial Services Industry, 10,001+ employees
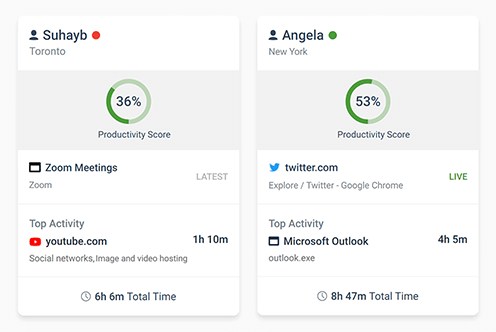
Get Advanced Activity Insights
BrowseReporter is a versatile computer activity monitoring software to track productivity, web browsing, and app use
- Make informed decisions
- Enforce company policies
- Improve productivity
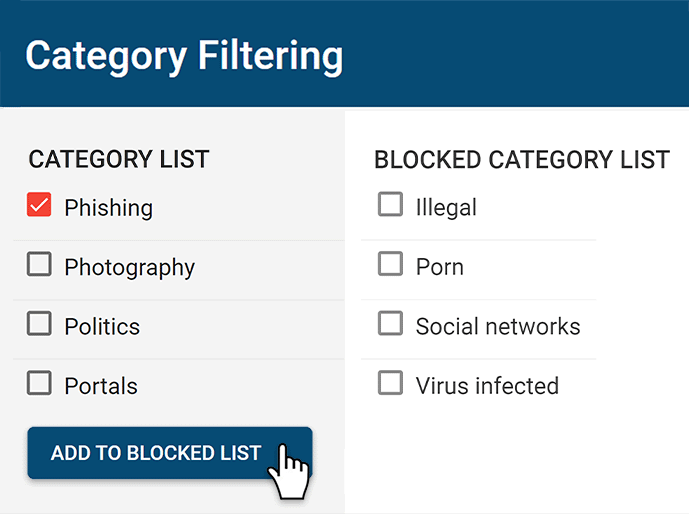
Block Harmful Websites
BrowseControl is an easy-to-use website blocking software for restricting internet access
- Block URLs & categories
- Block unwanted apps
- Website allow & block lists
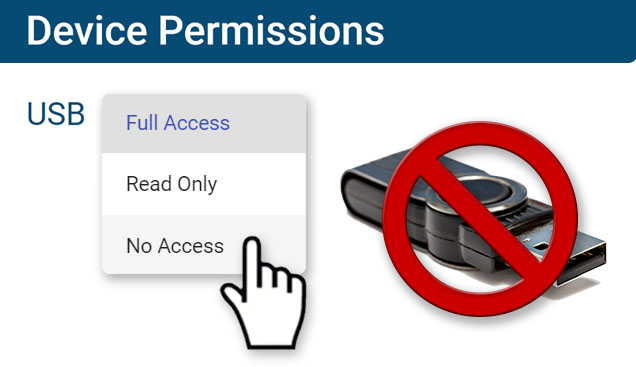
Stop Data Theft to USB Devices
AccessPatrol is USB control software to protect sensitive data against theft to portable storage devices
- Block USB devices
- USB file activity alerts
- Block file transfers
Control PC Power States
enPowerManager is a remote PC power manager for centrally managing power settings across all endpoints.
- Track logon and logoff times
- Log PC power event history
- Remotely shutdown PCs
CurrentWare's Key Features
User Activity Monitoring
Track web browsing, software use, search queries, and more
Screenshot Monitoring
Take automatic screenshots or remotely view desktops
Track Software Usage
Get insights into software usage trends in your organization
Transparent & Stealth Modes
Run silently in the background or provide notice of monitoring
Block USB & Other Devices
Set full access, read only or no access on storage devices
Device Whitelist
Allow only authorized storage devices to be used
Block File Transfers
Prevent files from being transferred to portable storage
DLP Activity Reports
Track file transfers, storage device use, file operations, and more
Block Websites
Block websites based on
URLs & content categories
Block Downloads/Uploads
Prevent uploading and downloading based on file type
Application Blacklisting
Block specific Windows
applications from launching
PC Power Management
Remotely track and control PC power states
Central Web Console
Save time with a central admin console; optionally integrate Active
Directory OUs or security groups
Platform Security
Protect your CurrentWare console
with 2FA, passwords, privilege
management, and more
Offsite Management
Extend onsite security policies to computers running outside the corporate network
SQL Server Supported
Database scaled for enterprise and
large business operations using
Microsoft SQL Server
Learn How to Meet These Compliance Requirements With CurrentWare
NERC CIP
Protect TCAs & BCSI From Insider Threats
ISO 27001
Increase the Maturity of Your ISO27K ISMS
NIST 800-171/53
Protect Controlled Unclassified Information
CIPA for Education
Qualify for the FCC’s
E-Rate Program

Cyber Essentials
Critical Security Controls For Your Assessment

CMMC
Protect CUI to qualify for DoD contracts
Meet NIST 800-53 & NIST 800-171 Compliance With CurrentWare
Frequently Asked Questions
How does CurrentWare help with NIST 800‑171 compliance?
CurrentWare helps enforce NIST 800‑171 controls by providing robust endpoint security and visibility:
- Logging user and system activity with BrowseReporter for comprehensive audit trails.
- Restricting USB and peripheral access with AccessPatrol to prevent unauthorized data exfiltration.
- Controlling internet and application usage with BrowseControl to minimize unauthorized software and network access.
- Generating audit logs and real-time alerts for suspicious or non-compliant behavior.
These features support compliance with essential NIST 800-171 requirements for continuous monitoring, strong access control, and comprehensive audit trail maintenance.
What are the logging requirements for NIST 800‑171 and how does CurrentWare meet them?
CurrentWare supports NIST 800-171’s audit logging requirements by automatically capturing detailed activity logs, including:
- USB device usage and file transfers.
- Website visits and application activity.
- User login and logout sessions.
- Admin activity and policy changes.
These logs are stored centrally, provide timestamps, and can be used to demonstrate compliance with the NIST 800-171 Audit and Accountability (AU) controls, enabling organizations to monitor, analyze, investigate, and report on system activity.
Is employee monitoring necessary for NIST compliance, and how does CurrentWare support it?
Yes, continuous monitoring is crucial for NIST 800-171 compliance. CurrentWare enables continuous monitoring of on-site and remote endpoints to detect unauthorized activity, enforce usage policies, and maintain comprehensive audit trails. This helps organizations meet the stringent monitoring and incident response requirements under NIST 800-171 by providing visibility into user behavior and system interactions, ensuring accountability and security.
What features does CurrentWare provide to support NIST 800-171 compliance?
CurrentWare’s suite includes several key features designed to support NIST 800-171 compliance:
- User activity logging (BrowseReporter): Tracks web Browse, software use, screenshot monitoring, and more.
- USB and peripheral control (AccessPatrol): Manages access to removable media and other devices to prevent data loss and malware introduction.
- Web and application restrictions (BrowseControl): Blocks access to unauthorized websites and applications to reduce the attack surface.
- Real-time alerts and policy enforcement: Notifies administrators of policy violations and suspicious activity.
- Centralized reporting for audits: Provides granular, exportable reports essential for compliance audits and investigations.
These tools directly support control objectives related to auditing, access control, media protection, and system integrity within the NIST 800-171 framework.
Does CurrentWare support NIST 800-171 control families like Access Control and Audit Logging?
Yes. CurrentWare supports multiple NIST 800-171 control families through its robust feature set:
- Access Control (AC): Enforces USB, web, and application access restrictions, and supports the principle of least privilege.
- Audit and Accountability (AU): Logs detailed user and system activity, generates audit trails, and allows for the review of access patterns and system events.
- Media Protection (MP): Provides granular control over removable media devices, logging transfers and preventing unauthorized data movement.
- System and Communications Protection (SC): Monitors endpoints to detect and restrict unauthorized data flows, and prevents the introduction of malicious code.
- Configuration Management (CM): Helps identify and manage unauthorized software installations (shadow IT) and system configurations.
- Incident Response (IR): Supports incident detection through real-time alerts and provides forensic data for post-incident analysis.
These features help organizations meet various security requirements outlined in the NIST SP 800-171 framework.
Can CurrentWare help detect and respond to insider threats?
Yes. CurrentWare is a powerful tool for insider threat detection and prevention. It enables organizations to monitor user behavior, identify anomalous activity (e.g., unusual data transfers, attempts to access restricted resources), and send real-time alerts for policy violations. These capabilities align directly with NIST 800-171’s requirements for continuous system monitoring, audit logging, and incident response readiness, allowing organizations to detect and mitigate insider risks effectively.